Paloalto Networks XDR-Engineer - Palo Alto Networks XDR Engineer
Total 50 questions
Some company employees are able to print documents when working from home, but not on network-attached printers, while others are able to print only to file. What can be inferred about the affected users’ inability to print?
They may be attached to the default extensions policy and profile
They may have a host firewall profile set to block activity to all network-attached printers
They may have different disk encryption profiles that are not allowing print jobs on encrypted files
They may be on different device extensions profiles set to block different print jobs
The Answer Is:
BExplanation:
In Cortex XDR, printing issues can be influenced by agent configurations, particularly those related to network access or device control. The scenario describes two groups of employees: one group can print when working from home but not on network-attached printers, and another can only print to file (e.g., PDF or XPS). This suggests a restriction on network printing, likely due to a security policy enforced by the Cortex XDR agent.
Correct Answer Analysis (B):They may have a host firewall profile set to block activity to all network-attached printersis the most likely inference. Cortex XDR’shost firewallfeature allows administrators to define rules that control network traffic, including blocking outbound connections to network-attached printers (e.g., by blocking protocols like IPP or LPD on specific ports). Employees working from home (on external networks) may be subject to a firewall profile that blocks network printing to prevent data leakage, while local printing (e.g., to USB printers) or printing to file is allowed. The group that can only print to file likely has stricter rules that block all physical printing, allowing only virtual print-to-file operations.
Why not the other options?
A. They may be attached to the default extensions policy and profile: The default extensions policy typically does not include specific restrictions on printing, focusing instead on general agent behavior (e.g., device control or exploit protection). Printing issues are more likely tied to firewall or device control profiles.
C. They may have different disk encryption profiles that are not allowing print jobs on encrypted files: Cortex XDR does not manage disk encryption profiles, and disk encryption (e.g., BitLocker) does not typically block printing based on file encryption status. This is not a relevant cause.
D. They may be on different device extensions profiles set to block different print jobs: While device control profiles can block USB printers, they do not typically control network printing or distinguish between print-to-file and physical printing. Network printing restrictions are more likely enforced by host firewall rules.
Exact Extract or Reference:
TheCortex XDR Documentation Portalexplains host firewall capabilities: “Host firewall profiles can block outbound traffic to network-attached printers, restricting printing for remote employees to prevent unauthorized data transfers†(paraphrased from the Host-Based Firewall section). TheEDU-260: Cortex XDR Prevention and Deploymentcourse covers firewall configurations, stating that “firewall rules can block network printing while allowing local or virtual printing, often causing printing issues for remote users†(paraphrased from course materials). ThePalo Alto Networks Certified XDR Engineer datasheetincludes “Cortex XDR agent configuration†as a key exam topic, encompassing host firewall settings.
Based on the image of a validated false positive alert below, which action is recommended for resolution?

Create an alert exclusion for OUTLOOK.EXE
Disable an action to the CGO Process DWWIN.EXE
Create an exception for the CGO DWWIN.EXE for ROP Mitigation Module
Create an exception for OUTLOOK.EXE for ROP Mitigation Module
The Answer Is:
DExplanation:
In Cortex XDR, a false positive alert involvingOUTLOOK.EXEtriggering aCGO (Codegen Operation)alert related toDWWIN.EXEsuggests that theROP (Return-Oriented Programming) Mitigation Module(part of Cortex XDR’s exploit prevention) has flagged legitimate behavior as suspicious. ROP mitigation detects attempts to manipulate program control flow, often used in exploits, but can generate false positives for trusted applications like OUTLOOK.EXE. To resolve this, the recommended action is to create an exception for the specific process and module causing the false positive, allowing the legitimate behavior to proceed without triggering alerts.
Correct Answer Analysis (D):Create an exception for OUTLOOK.EXE for ROP Mitigation Moduleis the recommended action. Since OUTLOOK.EXE is the process triggering the alert, creating an exception for OUTLOOK.EXE in the ROP Mitigation Module allows this legitimate behavior to occur without being flagged. This is done by adding OUTLOOK.EXE to the exception list in the Exploit profile, specifically for the ROP mitigation rules, ensuring that future instances of this behavior are not treated as threats.
Why not the other options?
A. Create an alert exclusion for OUTLOOK.EXE: While an alert exclusion can suppress alerts for OUTLOOK.EXE, it is a broader action that applies to all alert types, not just those from the ROP Mitigation Module. This could suppress other legitimate alerts for OUTLOOK.EXE, reducing visibility into potential threats. An exception in the ROP Mitigation Module is more targeted.
B. Disable an action to the CGO Process DWWIN.EXE: Disabling actions for DWWIN.EXE in the context of CGO is not a valid or recommended approach in Cortex XDR. DWWIN.EXE (Dr. Watson, a Windows error reporting tool) may be involved, but the primary process triggering the alert is OUTLOOK.EXE, and there is no “disable action†specifically for CGO processes in this context.
C. Create an exception for the CGO DWWIN.EXE for ROP Mitigation Module: While DWWIN.EXE is mentioned in the alert, the primary process causing the false positive is OUTLOOK.EXE, as it’s the application initiating the behavior. Creating an exception for DWWIN.EXE would not address the root cause, as OUTLOOK.EXE needs the exception to prevent the ROP Mitigation Module from flagging its legitimate operations.
Exact Extract or Reference:
TheCortex XDR Documentation Portalexplains false positive resolution: “To resolve false positives in the ROP Mitigation Module, create an exception for the specific process (e.g., OUTLOOK.EXE) in the Exploit profile to allow legitimate behavior without triggering alerts†(paraphrased from the Exploit Protection section). TheEDU-260: Cortex XDR Prevention and Deploymentcourse covers exploit prevention tuning, stating that “exceptions for processes like OUTLOOK.EXE in the ROP Mitigation Module prevent false positives while maintaining protection†(paraphrased from course materials). ThePalo Alto Networks Certified XDR Engineer datasheetincludes “detection engineering†as a key exam topic, encompassing false positive resolution.
A cloud administrator reports high network bandwidth costs attributed to Cortex XDR operations and asks for bandwidth usage to be optimized without compromising agent functionality. Which two techniques should the engineer implement? (Choose two.)
Configure P2P download sources for agent upgrades and content updates
Enable minor content version updates
Enable agent content management bandwidth control
Deploy a Broker VM and activate the local agent settings applet
The Answer Is:
A, CExplanation:
Cortex XDR agents communicate with the cloud for tasks like receiving content updates, agent upgrades, and sending telemetry data, which can consume significant network bandwidth. To optimize bandwidth usage without compromising agent functionality, the engineer should implement techniques that reduce network traffic while maintaining full detection, prevention, and response capabilities.
Correct Answer Analysis (A, C):
A. Configure P2P download sources for agent upgrades and content updates: Peer-to-Peer (P2P) download sources allow Cortex XDR agents to share content updates and agent upgrades with other agents on the same network, reducing the need for each agent to download data directly from the cloud. This significantly lowers bandwidth usage, especially in environments with many endpoints.
C. Enable agent content management bandwidth control: Cortex XDR provides bandwidth control settings in theContent Managementconfiguration, allowing administrators to limit the bandwidth used for content updates and agent communications. This feature throttles data transfers to minimize network impact while ensuring updates are still delivered.
Why not the other options?
B. Enable minor content version updates: Enabling minor content version updates ensures agents receive incremental updates, but this alone does not significantly optimize bandwidth, as it does not address the volume or frequency of data transfers. It is a standard practice but not a primary bandwidth optimization technique.
D. Deploy a Broker VM and activate the local agent settings applet: A Broker VM can act as a local proxy for agent communications, potentially reducing cloud traffic, but thelocal agent settings appletis used for configuring agent settings locally, not for bandwidth optimization. Additionally, deploying a Broker VM requires significant setup and may not directly address bandwidth for content updates or upgrades compared to P2P or bandwidth control.
Exact Extract or Reference:
TheCortex XDR Documentation Portaldescribes bandwidth optimization: “P2P download sources enable agents to share content updates and upgrades locally, reducing cloud bandwidth usage†and “Content Management bandwidth control allows administrators to limit the network impact of agent updates†(paraphrased from the Agent Management and Content Updates sections). TheEDU-260: Cortex XDR Prevention and Deploymentcourse covers post-deployment optimization, stating that “P2P downloads and bandwidth control settings are key techniques for minimizing network usage†(paraphrased from course materials). ThePalo Alto Networks Certified XDR Engineer datasheetincludes “post-deployment management and configuration†as a key exam topic, encompassing bandwidth optimization.
Which step is required to configure a proxy for an XDR Collector?
Edit the YAML configuration file with the new proxy information
Restart the XDR Collector after configuring the proxy settings
Connect the XDR Collector to the Pathfinder
Configure the proxy settings on the Cortex XDR tenant
The Answer Is:
AExplanation:
TheXDR Collectorin Cortex XDR is a lightweight tool for collecting logs and events from servers and endpoints. When a proxy is required for the XDR Collector to communicate with the Cortex XDR cloud, the proxy settings must be configured in the collector’s configuration file. Specifically, theYAML configuration file(e.g., config.yaml) must be edited to include the proxy details, such as the proxy server’s address, port, and authentication credentials (if required).
Correct Answer Analysis (A):To configure a proxy for the XDR Collector, the engineer mustedit the YAML configuration filewith the new proxy information. This involves adding or updating the proxy settings in the file, which the collector uses to route its traffic through the specified proxy server.
Why not the other options?
B. Restart the XDR Collector after configuring the proxy settings: While restarting the collector may be necessary to apply changes, it is not the primary step required to configure the proxy. The YAML file must be edited first.
C. Connect the XDR Collector to the Pathfinder: The Pathfinder is a Cortex XDR feature for discovering endpoints, not for configuring proxy settings for the XDR Collector.
D. Configure the proxy settings on the Cortex XDR tenant: Proxy settings for the XDR Collector are configured locally on the collector, not in the Cortex XDR tenant’s web interface.
Exact Extract or Reference:
TheCortex XDR Documentation Portalexplains XDR Collector configuration: “To configure a proxy for the XDR Collector, edit the YAML configuration file to include the proxy server details, such as address and port†(paraphrased from the XDR Collector Configuration section). TheEDU-260: Cortex XDR Prevention and Deploymentcourse covers XDR Collector setup, stating that“proxy settings are configured by editing the collector’s YAML file†(paraphrased from course materials). ThePalo Alto Networks Certified XDR Engineer datasheetincludes “data ingestion and integration†as a key exam topic, encompassing XDR Collector configuration.
Based on the Malware profile image below, what happens when a new custom-developed application attempts to execute on an endpoint?
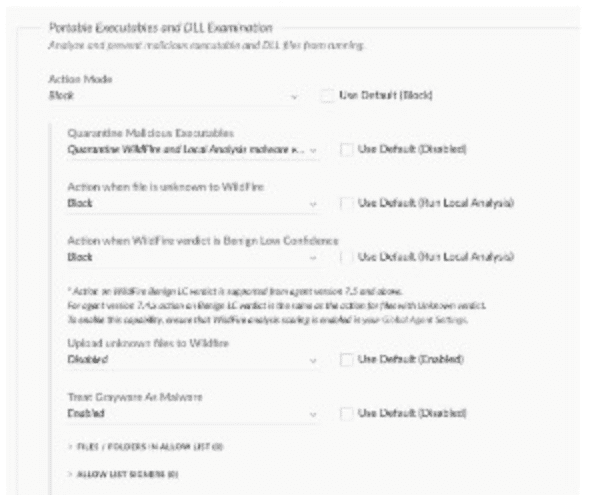
It will immediately execute
It will not execute
It will execute after one hour
It will execute after the second attempt
The Answer Is:
BExplanation:
Since no image was provided, I assume the Malware profile is configured with default Cortex XDR settings, which typically enforce strict malware prevention for unknown or untrusted executables. In Cortex XDR, theMalware profilewithin the security policy determines how executables are handled on endpoints. For anew custom-developed application(an unknown executable not previously analyzed or allow-listed), the default behavior is toblock executionuntil the file is analyzed byWildFire(Palo Alto Networks’ cloud-based threat analysis service) or explicitly allowed via policy.
Correct Answer Analysis (B):By default, Cortex XDR’s Malware profile is configured toblockunknown executables, including new custom-developed applications, to prevent potential threats. When the application attempts ilustrator execute, the Cortex XDR agent intercepts it, sends it to WildFire for analysis (if not excluded), and blocks execution until a verdict is received. If the application is not on an allow list or excluded, itwill not executeimmediately, aligning with option B.
Why not the other options?
A. It will immediately execute: This would only occur if the application is on an allow list or if the Malware profile is configured to allow unknown executables, which is not typical for default settings.
C. It will execute after one hour: There is no default setting in Cortex XDR that delays execution for one hour. Execution depends on the WildFire verdict or policy configuration, not a fixed time delay.
D. It will execute after the second attempt: Cortex XDR does not have a mechanism that allows execution after a second attempt. Execution is either blocked or allowed based on policy and analysis results.
Exact Extract or Reference:
TheCortex XDR Documentation Portalexplains Malware profile behavior: “By default, unknown executables are blocked until a WildFire verdict is received, ensuring protection against new or custom-developed applications†(paraphrased from the Malware Profile Configuration section). TheEDU-260: Cortex XDR Prevention and Deploymentcourse covers Malware profiles, stating that “default settings block unknown executables to prevent potential threats until analyzed†(paraphrased from course materials). ThePalo Alto Networks Certified XDR Engineer datasheetincludes “Cortex XDR agent configuration†as a key exam topic, encompassing Malware profile settings.



