Cisco 100-160 - Cisco Certified Support Technician (CCST) Cybersecurity
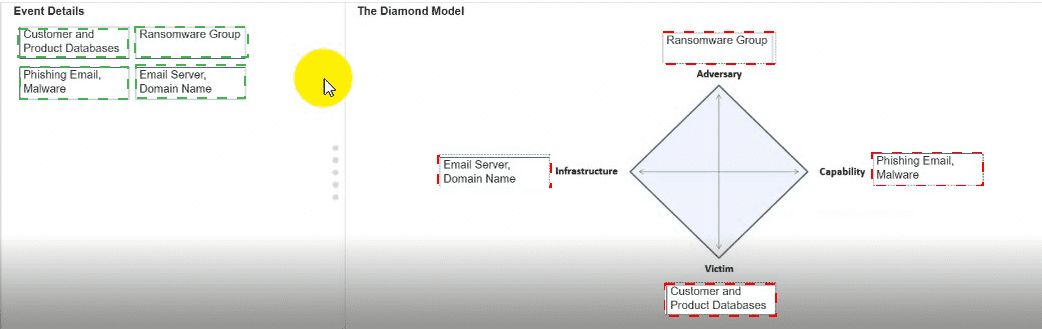
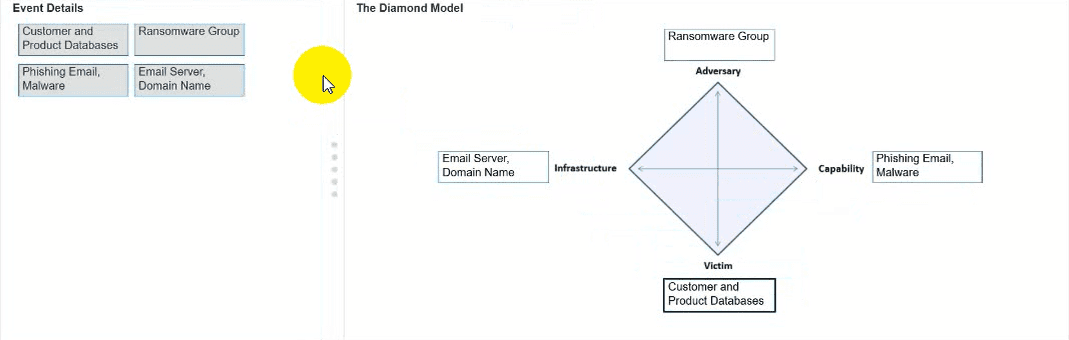
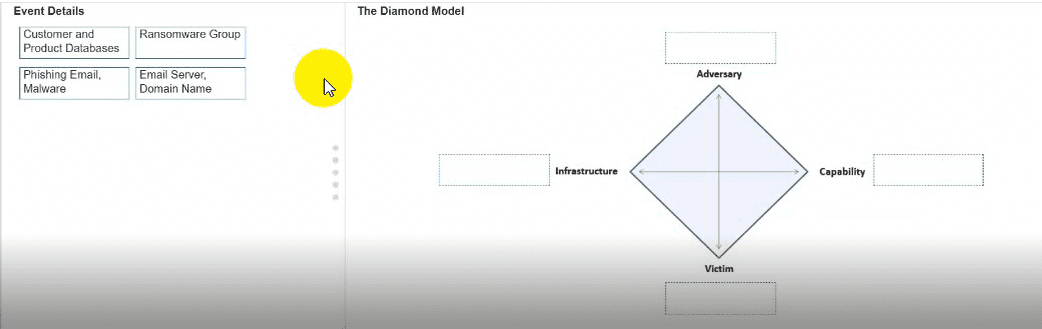
You need to diagram an intrusion event by using the Diamond Model.
Move each event detail from the list on the left to the correct location in the diagram on the right.
Note: You will receive partial credit for each correct response.
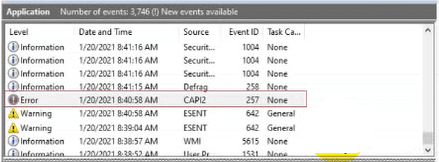
You are reviewing the Application log on a Windows computer. You see an event with an error-level message as shown.
What can you determine about the application that generated the event message?
Which data type is protected through hard disk encryption?
You are planning to work from home. Your company requires that you connect to the company network through a VPN.
Which three critical functions do VPNs provide to remote workers?(Choose 3.)
A threat actor sets up a rogue access point (AP) at a local cafe. The rogue AP captures traffic and then forwards the traffic to the cafe AP.
Which type of attack does this scenario describe?