Cisco 100-160 - Cisco Certified Support Technician (CCST) Cybersecurity
Your company is creating a BYOD policy to allow employees to join their personal smartphones to the company network.
Which three requirements are commonly included in a BYOD policy?(Choose 3.)
A client cannot connect to the corporate web server. You discover a large number of half-open TCP connections to the server.
What should you do?
Which network security technology passively monitors network traffic and compares the captured packet stream with known malicious signatures?
During an incident response, the security team needs to isolate a compromised server from the rest of the network but still allow forensic analysis. Which action should they take?
What is the primary purpose of running a vulnerability scan on your network?
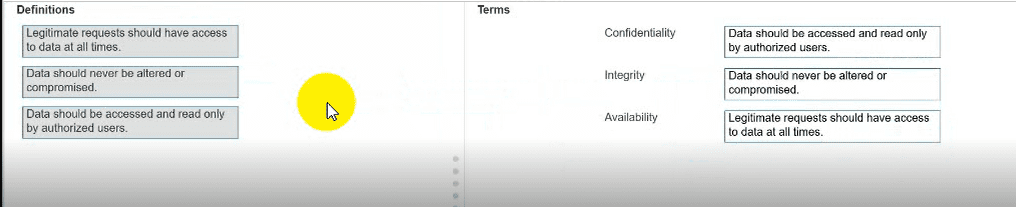
Move each definition from the list on the left to the correct CIA Triad term on the right.
Note: You will receive partial credit for each correct answer.

You work for a hospital that stores electronic protected health information (ePHI) in an online portal. Authorized employees can use their mobile devices to access patient ePHI.
You need to ensure that employees’ mobile devices comply with HIPAA regulations.
Which safeguard should you develop and implement?
Which encryption type is commonly used to secure WiFi networks?
A remote worker is visiting a branch office to attend face-to-face meetings. The worker tries to associate their company laptop with the branch wireless access point (WAP) but is unable to do so.
What is a possible cause?
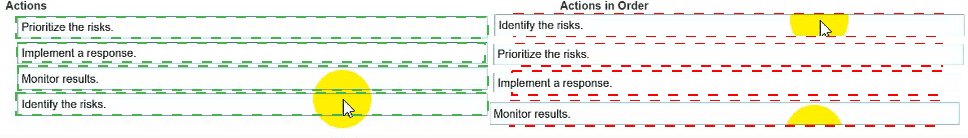
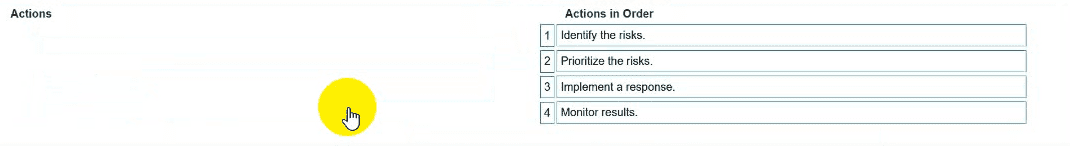
You need to manage security risks at your company. In which order should you complete the actions?
Move all the actions to the answer area and place them in the correct order.