Cisco 200-201 - Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS)
Refer to the exhibit.
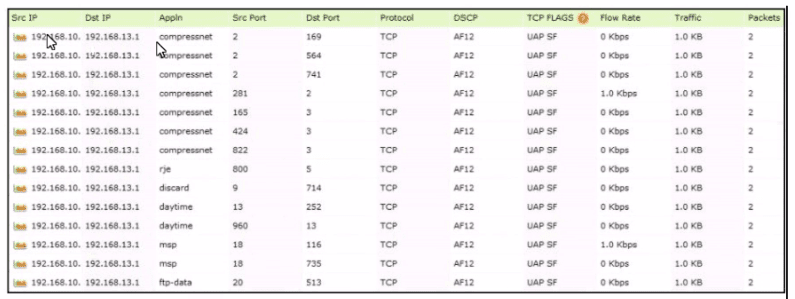
Which tool was used to generate this data?
An investigator is examining a copy of an ISO file that is stored in CDFS format. What type of evidence is this file?
A cyberattacker notices a security flaw in a software that a company is using They decide to tailor a specific worm to exploit this flaw and extract saved passwords from the software To which category of the Cyber Kill Cham model does this event belong?
What is a difference between rule-based and role-based access control mechanisms?
What is the difference between mandatory access control (MAC) and discretionary access control (DAC)?
Which piece of information is needed for attribution in an investigation?
Refer to the exhibit.
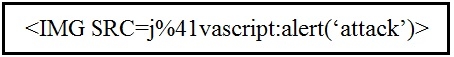
Which kind of attack method is depicted in this string?
Which technology should be used to implement a solution that makes routing decisions based on HTTP header, uniform resource identifier, and SSL session ID attributes?
What causes events on a Windows system to show Event Code 4625 in the log messages?
Which action prevents buffer overflow attacks?



