Cisco 200-201 - Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS)
Drag and drop the definition from the left onto the phase on the right to classify intrusion events according to the Cyber Kill Chain model.
An analyst is investigating a host in the network that appears to be communicating to a command and control server on the Internet. After collecting this packet capture, the analyst cannot determine the technique and payload used for the communication.
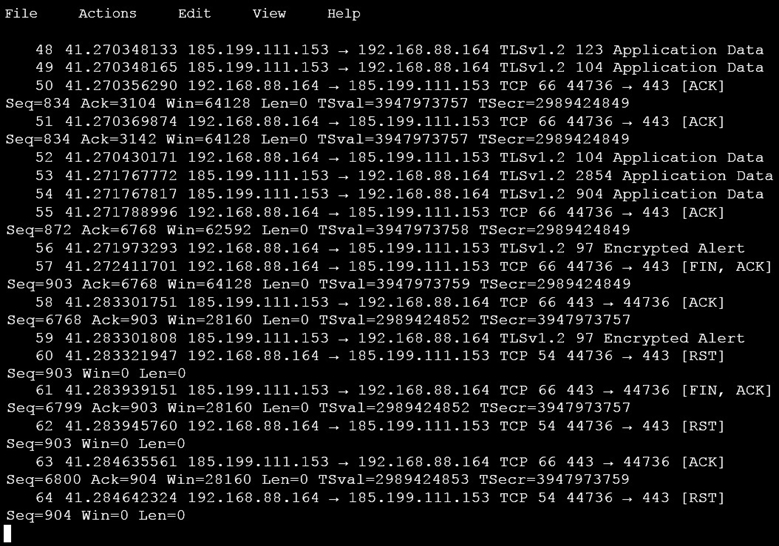
Which obfuscation technique is the attacker using?
What is the difference between vulnerability and risk?
Refer to the exhibit.
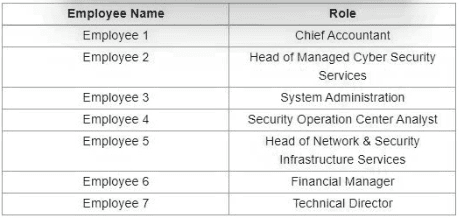
Which stakeholders must be involved when a company workstation is compromised?
Refer to the exhibit
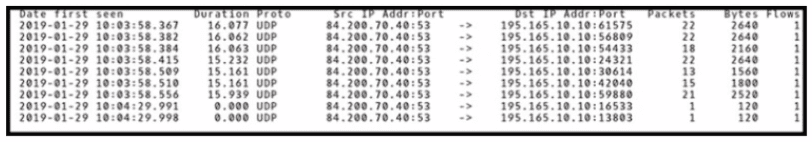
An engineer is analyzing DNS response packets that are larger than expected The engineer looks closer and notices a lack of appropriate DNS queries What is occurring?
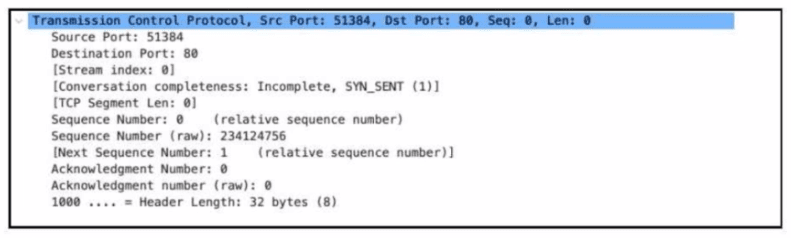
Refer to the exhibit. Which alert is identified from this packet?
What is an example of social engineering attacks?
Refer to the exhibit.

Which type of evidence is this file?
Which data capture includes payload and header information?
Which process represents the application-level allow list?




