Cisco 200-201 - Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS)
Which metric in CVSS indicates an attack that takes a destination bank account number and replaces it with a different bank account number?
An engineer is working with the compliance teams to identify the data passing through the network. During analysis, the engineer informs the compliance team that external penmeter data flows contain records, writings, and artwork Internal segregated network flows contain the customer choices by gender, addresses, and product preferences by age. The engineer must identify protected data. Which two types of data must be identified'? (Choose two.)
How does agentless monitoring differ from agent-based monitoring?
What is indicated by an increase in IPv4 traffic carrying protocol 41 ?
A security engineer must implement an Intrusion Prevention System (IPS) inside an organization’s DMZ. One of the requirements is the ability to block suspicious traffic in real time based on a triggered signature. The IPS will be connected behind the DMZ firewalls directly to the core switches. Which traffic integration method must be implemented to complete this project?
An engineer needs to have visibility on TCP bandwidth usage, response time, and latency, combined with deep packet inspection to identify unknown software by its network traffic flow. Which two features of Cisco Application Visibility and Control should the engineer use to accomplish this goal? (Choose two.)
Which data format is the most efficient to build a baseline of traffic seen over an extended period of time?
Refer to the exhibit.

What is occurring?
What is the benefit of processing statistical data for security systems?
Drag and drop the event term from the left onto the description on the right.
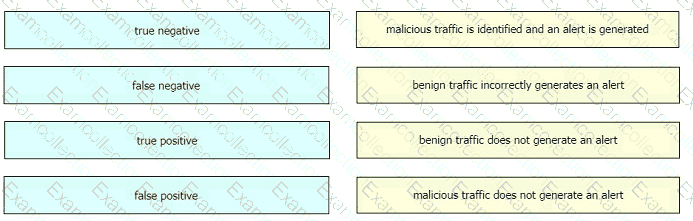



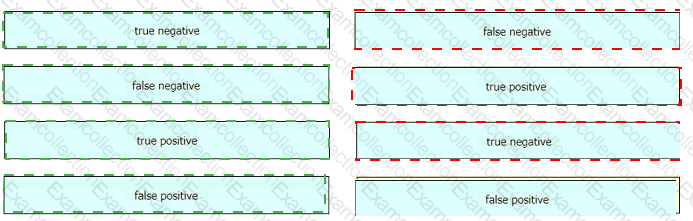
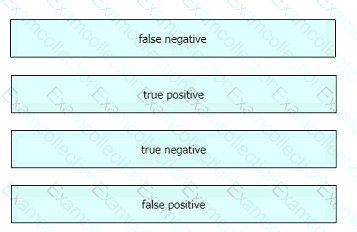 A screenshot of a computer Description automatically generated
A screenshot of a computer Description automatically generated