Cisco 200-201 - Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS)
Refer to the exhibit.
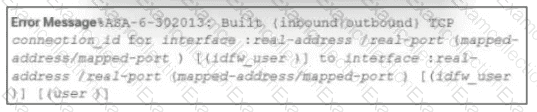
During the analysis of a suspicious scanning activity incident, an analyst discovered multiple local TCP connection events Which technology provided these logs?
What is a difference between SI EM and SOAR security systems?
Which vulnerability type is used to read, write, or erase information from a database?
Which two measures are used by the defense-m-depth strategy? (Choose two)
A user received a targeted spear-phishing email and identified it as suspicious before opening the content. To which category of the Cyber Kill Chain model does to this type of event belong?
What should a security analyst consider when comparing inline traffic interrogation with traffic tapping to determine which approach to use in the network?
Which technology assures that the information transferred from point A to point B is unaltered and authentic?
Which NIST IR category stakeholder is responsible for coordinating incident response among various business units, minimizing damage, and reporting to regulatory agencies?
Refer to the exhibit.
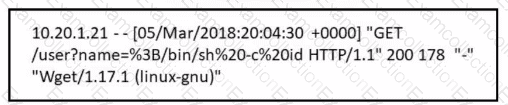
Which attack is being attempted against a web application?
Refer to the exhibit.
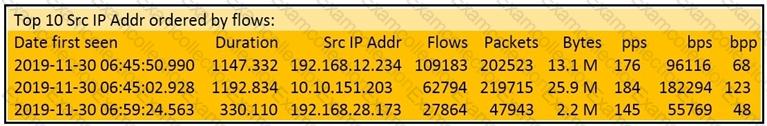
What information is depicted?



