Cisco 200-201 - Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS)
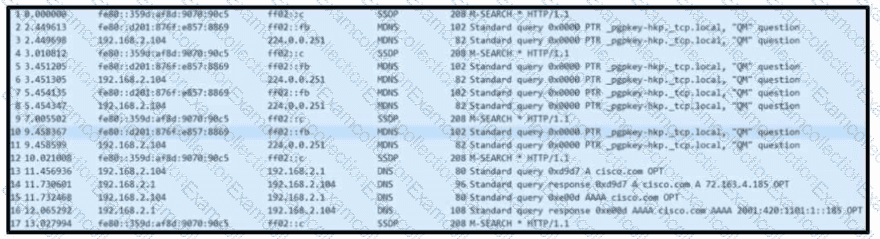
Refer to the exhibit. Based on the .pcap file, which DNS server is used to resolve cisco.com?
What ate two categories of DDoS attacks? (Choose two.)
What are the two characteristics of the full packet captures? (Choose two.)
What are two denial-of-service (DoS) attacks? (Choose two)
What is the difference between antimalware and antivirus solutions?
A suspicious user opened a connection from a compromised host inside an organization. Traffic was going through a router and the network administrator was able to identify this flow. The admin was following 5-tuple to collect needed data. Which information was gathered based on this approach?
A security team receives a ticket to investigate suspicious emails sent to company employees from known malicious domains. Further analysis shows that a targeted phishing attempt was successfully blocked by the company’s email antivirus. At which step of the Cyber Kill Chain did the security team mitigate this attack?
What is a comparison between rule-based and statistical detection?
Which two elements are used by the defense-in-depth strategy? (Choose two)
What is corroborating evidence?



