Cisco 200-201 - Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS)
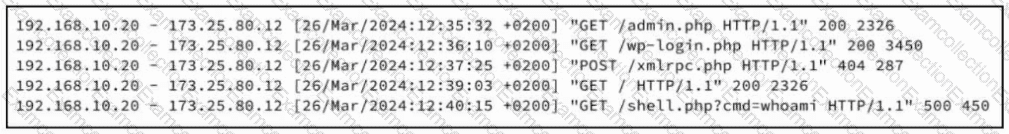
Refer to the exhibit. A security analyst examines Apache web server logs and notices the entries. Which security concern is occurring?
What is the function of a command and control server?
Which utility blocks a host portscan?
Which two components reduce the attack surface on an endpoint? (Choose two.)
A large load of data is being transferred to an external destination via UDP 53 port. Which obfuscation technique is used?
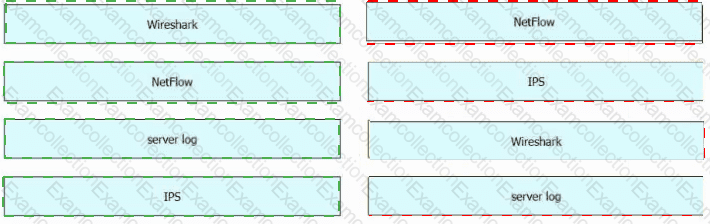
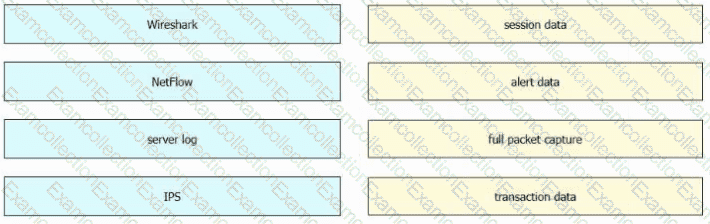
Drag and drop the data sources from the left onto the corresponding data types on the right.
How is SQL injection prevented?
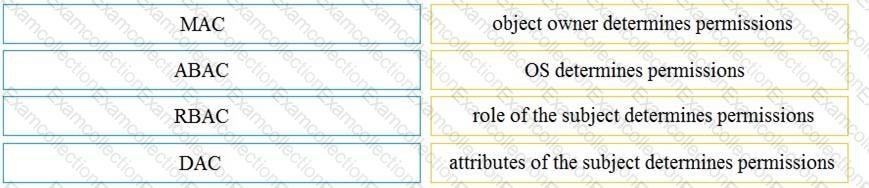
Drag and drop the access control models from the left onto the correct descriptions on the right.
A network engineer noticed in the NetFlow report that internal hosts are sending many DNS requests to external DNS servers A SOC analyst checked the endpoints and discovered that they are infected and became part of the botnet Endpoints are sending multiple DNS requests but with spoofed IP addresses of valid external sources What kind of attack are infected endpoints involved in1?
What describes the defense-m-depth principle?