Cisco 200-201 - Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS)
Refer to exhibit.
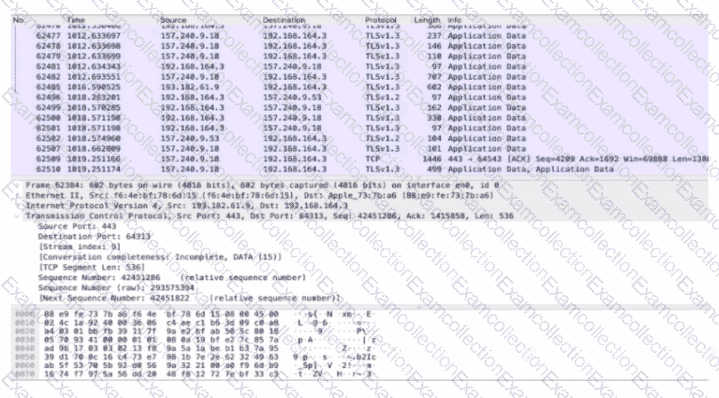
An analyst performs the analysis of the pcap file to detect the suspicious activity. What challenges did the analyst face in terms of data visibility?
What is the purpose of a ransomware attack?
Which statement describes threat hunting?
What is the role of indicator of compromise in an investigation?
An engineer needs to fetch logs from a proxy server and generate actual events according to the data received. Which technology should the engineer use to accomplish this task?
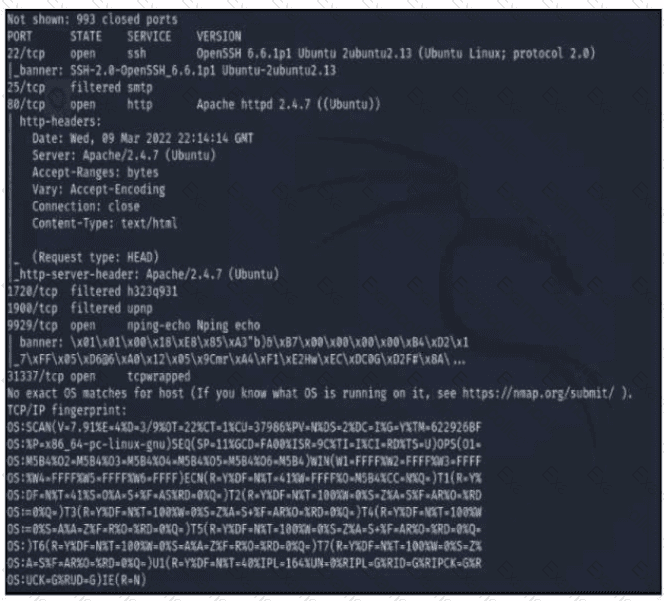
Refer to the exhibit A penetration tester runs the Nmap scan against the company server to uncover possible vulnerabilities and exploit them Which two elements can the penetration tester identity from the scan results? (Choose two.)
What is the difference between mandatory access control (MAC) and discretionary access control (DAC)?
A company had a recent breach and lost confidential data to a competitor. An internal investigation found out that a new junior accounting specialist logged in to the accounting server with their user ID and stole confidential data. The junior accounting specialist denies the action and claims that the attempt was done by someone else. During court proceedings, the company presents logs and CCTV camera recordings that show the malicious insider in action. Which type of evidence has the company presented?
During a quarterly vulnerability scan, a security analyst discovered unused uncommon ports open and in a listening state. Further investigation showed that the unknown application was communicating with an external IP address on an encrypted channel. A deeper analysis revealed a command and control communication on an infected server. At which step of the Cyber Kill Chain was the attack detected?
Exhibit.
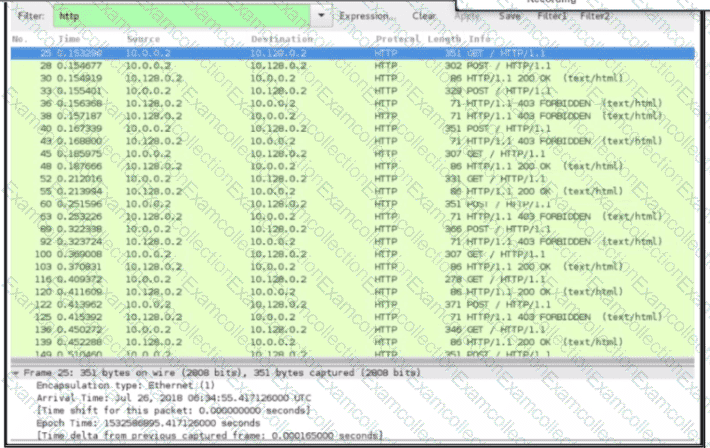
An engineer received a ticket about a slowdown of a web application, Drug analysis of traffic, the engineer suspects a possible attack on a web server. How should the engineer interpret the Wiresharat traffic capture?



