Cisco 200-201 - Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS)
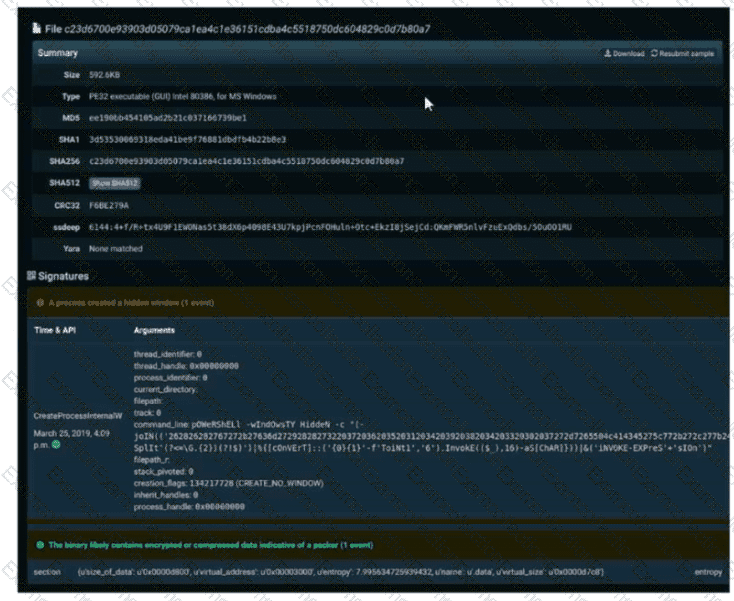
Refer to the exhibit. A SOC engineer is analyzing Cuckoo Sandbox report for a file that has been identified as suspicious by the endpoint security system. What is the state of the file?
What is the difference between deep packet inspection and stateful inspection?
An organization has recently adjusted its security stance in response to online threats made by a known hacktivist group.
What is the initial event called in the NIST SP800-61?
An engineer is sharing folders and files with different departments and got this error: "No such file or directory". What must the engineer verify next?
Refer to the exhibit.

An analyst received this alert from the Cisco ASA device, and numerous activity logs were produced. How should this type of evidence be categorized?
An employee of a company receives an email with an attachment. They notice that this email is from a suspicious source, and they decide not to open the attached file. After further investigation, a security analyst concludes that this file is malware. To which category of the Cyber Kill Chain model does this event belong?
What is the practice of giving employees only those permissions necessary to perform their specific role within an organization?
How does the approach of a behavioral detection system to identifying security threats compare to that of a rule-based detection system?
Which of these describes SOC metrics in relation to security incidents?
Why is encryption challenging to security monitoring?



