Cisco 200-201 - Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS)
What is a difference between data obtained from Tap and SPAN ports?
Refer to the exhibit.
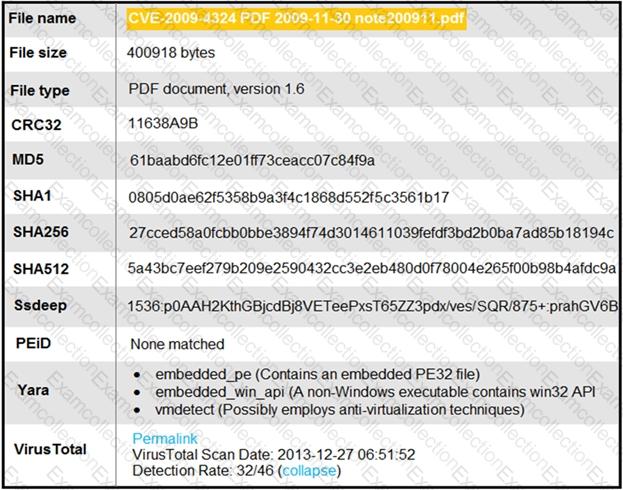
An engineer is analyzing this Cuckoo Sandbox report for a PDF file that has been downloaded from an email. What is the state of this file?
A security engineer notices confidential data being exfiltrated to a domain "Ranso4134-mware31-895" address that is attributed to a known advanced persistent threat group The engineer discovers that the activity is part of a real attack and not a network misconfiguration. Which category does this event fall under as defined in the Cyber Kill Chain?
A user received an email attachment named "Hr405-report2609-empl094.exe" but did not run it. Which category of the cyber kill chain should be assigned to this type of event?
Which type of access control depends on the job function of the user?
Endpoint logs indicate that a machine has obtained an unusual gateway address and unusual DNS servers via DHCP Which type of attack is occurring?
Which of these is a defense-in-depth strategy principle?
Which technique obtains information about how the system works without knowing it's design details?
Refer to the exhibit.
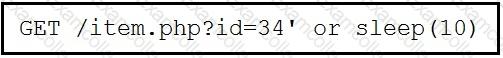
This request was sent to a web application server driven by a database. Which type of web server attack is represented?
What is the difference between discretionary access control (DAC) and role-based access control (RBAC)?



