CompTIA 220-1101 - CompTIA A+ Certification Exam: Core 1
Which of the following utilizes TCP ports 20/21 and transfers data in cleartext?
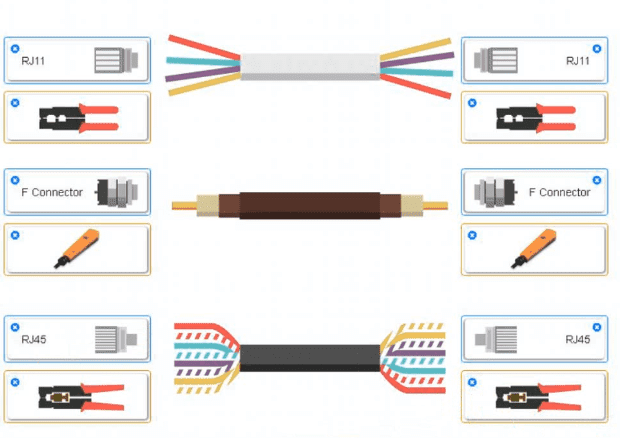
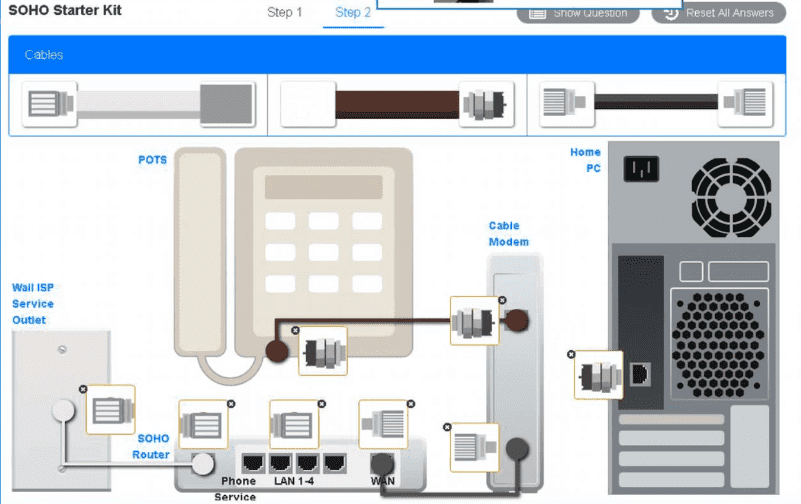
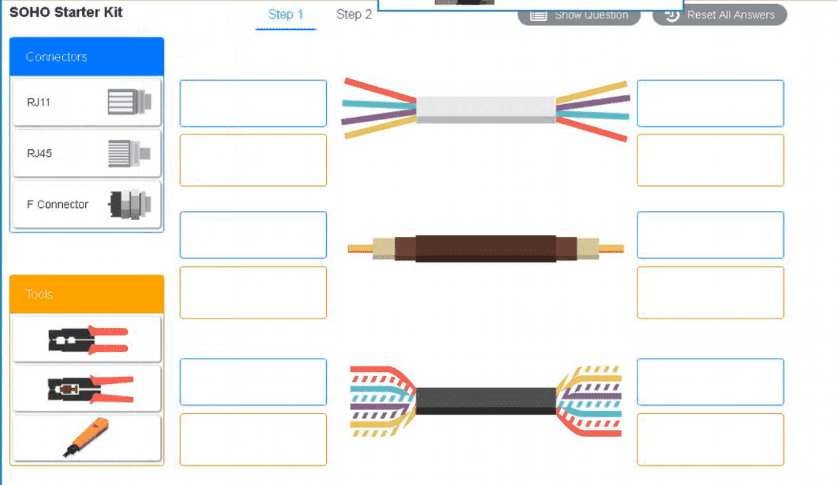
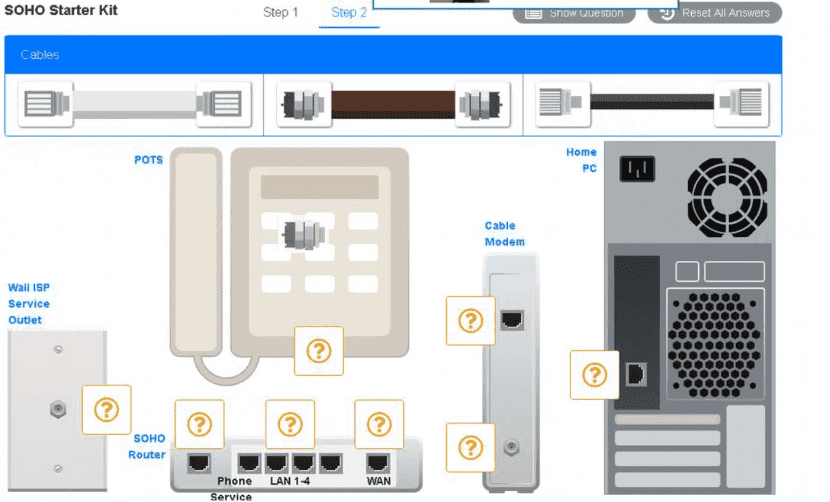
A small ISP has hired a new technician Joe, the new technician, is being trained to configure customers* home networks The trailing instructor gives me technician a starter kit with cables, cable ends, and other network equipment and asks mm to build a working network.
The computer should be connected to have internet connectivity and the phone should be connected to have a dial tone.
INSTRUCTIONS
Use the appropriate cables. cable ends, tools and equipment to configure the network ana connect an components accordingly
There are 3 steps and the simulation starts on step 1.
A computer that contains critical data has not been backed up and will not boot past a S. M. A. R. T, error that indicates imminent hard disk failure. Which of the following actions should the technician take FIRST?
A technician goes to a classroom to troubleshoot a projector that occasionally powers off. The technician recreates the issue and notices the projector will not power back on until approximately 15 minutes have passed. After 15 minutes of being powered on. the projector shuts off again. Which of the following should the technician perform NEXT to resolve the issue?
A company just bought a printer capable of automatically printing on both sides of the paper After installation, however, the technician can only print on both sides of the paper manually. Which of the following should the technician do to fix the issue?
A user reports that a PC occasionally falls to boot. The user reboots the PC. but the performance is degrading. The technician hears a strange, repetitive, ticking noise coming from the PC. Which of the following should the technician do FIRST?
A laptop's external webcam software is running, but it shows no image or video. Which of the following should a technician perform FIRST?
A system administrator has been tasked with allowing SMTP traffic through the system’s host-based firewall. Which of the following ports should the administrator enabled?
A technician needs to improve a workstation's overall response time for frequently used applications and data without removing the current hard drive. Which of the following storage devices should the technician install to BEST accomplish the objective?
A user acquired a new workstation and is attempting to open multiple targe Excel files simultaneously. The user is not experiencing the expected performance when executing such large requests. Which of the following should a technician do FIRST?
Which of the following would MOST likely be used to obtain electronic images of a large number of printed documents?
A user's computer is not receiving a network connection. The technician confirms that the connection seems to be down and looks for the user's port on the patch panel. The port and patch panel are not labeled. Which of the following network tools should the technician use to identify the port?
Which of the following would an administrator use to migrate virtual machines from on premises to the cloud?
In which of the following places is a laptop's wireless antenna MOST likely located?
A technician identified an issue on a workstation, obtained details from the user, and made a backup of the system. Which of the following should the technician do NEXT?
An administrator is configuring a corporate-owned smartphone for a new manager. The company requires the ability to wipe the phone's data remotely in the event of loss or theft and the capability to approve applications installed on the phone. Which of the following tools would BEST meet this need?
A user in a medical office contacts a technician regarding a printer that is used to print A4-sized labels. After the labels are printed, they mistakenly contain white space in the middle of the page. Which of the following would MOST likely be the cause?
A technician is upgrading a legacy wireless router for a home user. After installing the new router and configuring the SSID to be the same, none of the devices will connect to the network. Which of the following should the technician check NEXT?
Which of the following describes metered utilization of cloud resources?
Which of the following components enables the input on a mobile device's touch screen?