Cisco 300-215 - Conducting Forensic Analysis and Incident Response Using Cisco CyberOps Technologies (CBRFIR)
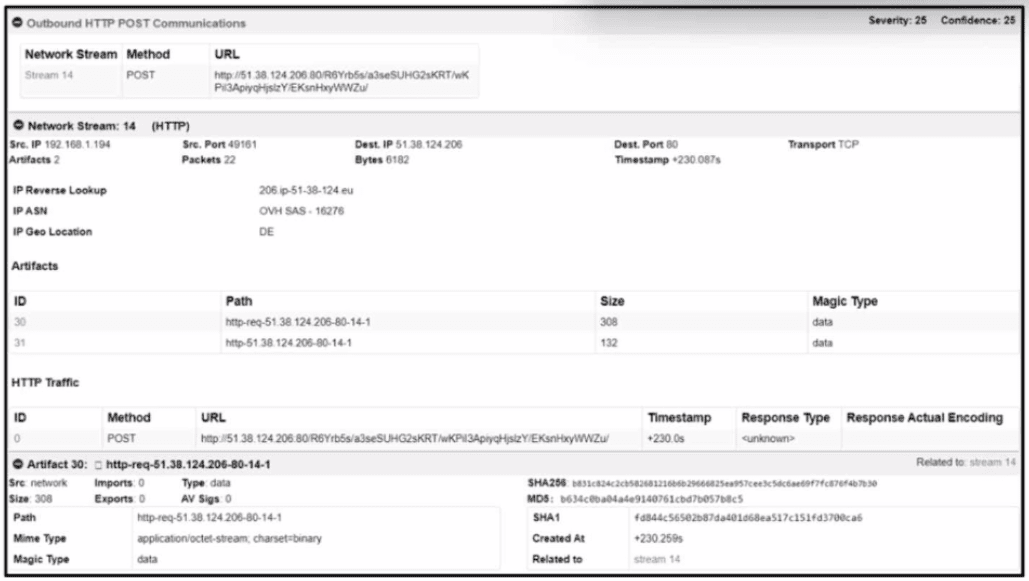
Refer to the exhibit.
According to the SNORT alert, what is the attacker performing?
A cybersecurity analyst is examining a complex dataset of threat intelligence information from various sources. Among the data, they notice multiple instances of domain name resolution requests to suspicious domains known for hosting C2 servers. Simultaneously, the intrusion detection system logs indicate a series of network anomalies, including unusual port scans and attempts to exploit known vulnerabilities. The internal logs also reveal a sudden increase in outbound network traffic from a specific internal host to an external IP address located in a high-risk region. Which action should be prioritized by the organization?
A security team receives reports of multiple files causing suspicious activity on users’ workstations. The file attempted to access highly confidential information in a centralized file server. Which two actions should be taken by a security analyst to evaluate the file in a sandbox? (Choose two.)
What is an issue with digital forensics in cloud environments, from a security point of view?
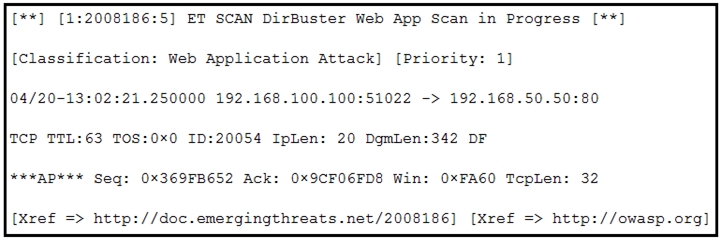
Refer to the exhibit.
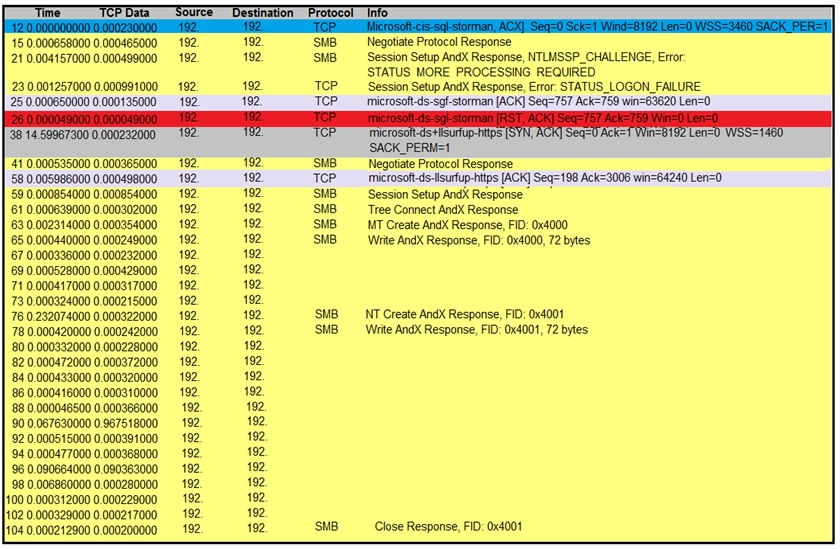
An engineer is analyzing a TCP stream in Wireshark after a suspicious email with a URL. What should be determined about the SMB traffic from this stream?
A security team is discussing lessons learned and suggesting process changes after a security breach incident. During the incident, members of the security team failed to report the abnormal system activity due to a high project workload. Additionally, when the incident was identified, the response took six hours due to management being unavailable to provide the approvals needed. Which two steps will prevent these issues from occurring in the future? (Choose two.)
A cybersecurity analyst is analyzing a complex set of threat intelligence data from internal and external sources. Among the data, they discover a series of indicators, including patterns of unusual network traffic, a sudden increase in failed login attempts, and multiple instances of suspicious file access on the company's internal servers. Additionally, an external threat feed highlights that threat actors are actively targeting organizations in the same industry using ransomware. Which action should the analyst recommend?
Refer to the exhibit.
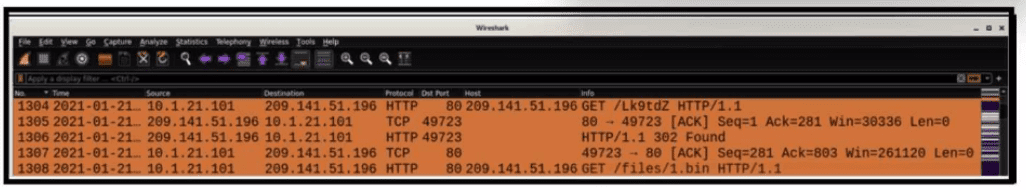
What is occurring within the exhibit?
Refer to the exhibit.
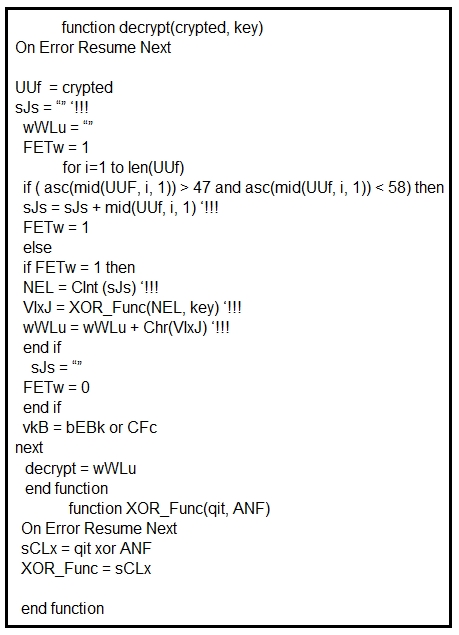
Which type of code created the snippet?