Cisco 300-215 - Conducting Forensic Analysis and Incident Response Using Cisco CyberOps Technologies (CBRFIR)
A security team received reports of users receiving emails linked to external or unknown URLs that are non-returnable and non-deliverable. The ISP also reported a 500% increase in the amount of ingress and egress email traffic received. After detecting the problem, the security team moves to the recovery phase in their incident response plan. Which two actions should be taken in the recovery phase of this incident? (Choose two.)
Which technique is used to evade detection from security products by executing arbitrary code in the address space of a separate live operation?
What is the goal of an incident response plan?
Refer to the exhibit.
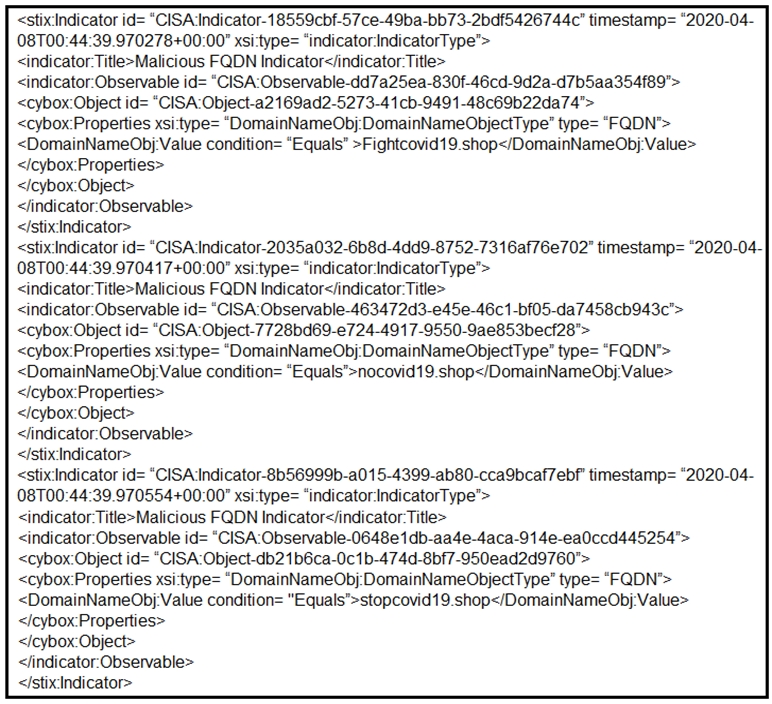
Which two actions should be taken based on the intelligence information? (Choose two.)



