Cisco 300-220 - Conducting Threat Hunting and Defending using Cisco Technologies for Cybersecurity 300-220 CBRTHD
While investigating multiple incidents using Cisco telemetry, analysts notice that attackers consistently use valid credentials, avoid malware, and rely on remote management protocols. Why is this information valuable for attribution?
Refer to the exhibit.
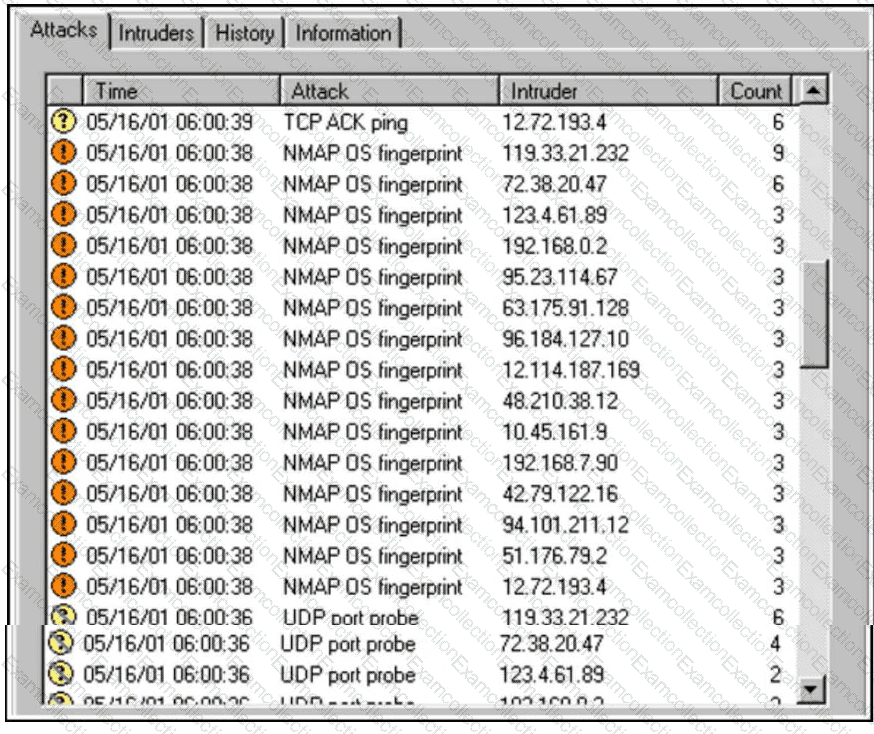
An increase in company traffic is observed by the SOC team. After they investigate the spike, it is concluded that the increase is due to ongoing scanning activity. Further analysis reveals that an adversary used Nmap for OS fingerprinting. Which type of indicators used by the adversary sits highest on the Pyramid of Pain?
Refer to the exhibit.
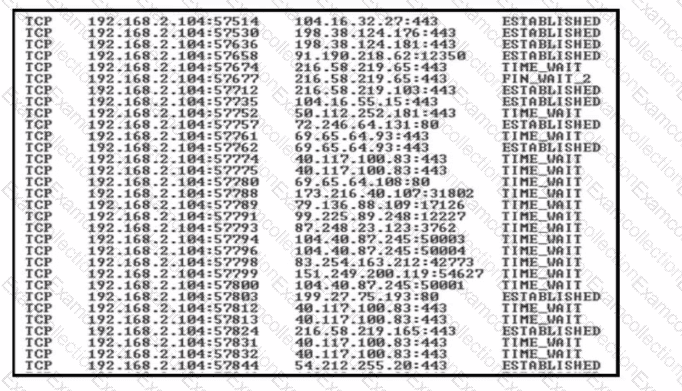
A security team detects a spike in traffic from the company web server. After further investigation, the team discovered that multiple connections have been established from the server to different IP addresses, but the web server logs contain both expected traffic and DDoS traffic. Which attribute must the team use to further filter the logs?
Refer to the exhibit.

A security engineer notices that a Windows Batch script includes calls to suspicious APIs. How will the script affect the system when it is executed?
During a structured hunt, analysts using Cisco SIEM tools complete hypothesis testing and confirm malicious activity. What is the NEXT step in the Cisco threat hunting lifecycle?
A mature SOC notices that several incidents over the past year involved attackers abusing legitimate administrative tools rather than deploying custom malware. Leadership asks the threat hunting team to improve detection coverage in a way that increases attacker cost rather than relying on easily replaceable indicators. Which detection strategy best aligns with this objective?
What is the classification of the pass-the-hash technique according to the MITRE ATT&CK framework?
During multiple intrusions, analysts observe that attackers consistently perform internal reconnaissance before privilege escalation, avoid noisy exploitation, and limit actions to business hours of the victim’s region. Why is this observation important for attribution?



