Cisco 300-220 - Conducting Threat Hunting and Defending using Cisco Technologies for Cybersecurity 300-220 CBRTHD
During multiple investigations using Cisco telemetry, analysts observe attackers consistently perform internal discovery before privilege escalation and avoid high-risk actions. Why is this observation useful for attribution?
Refer to the exhibit.
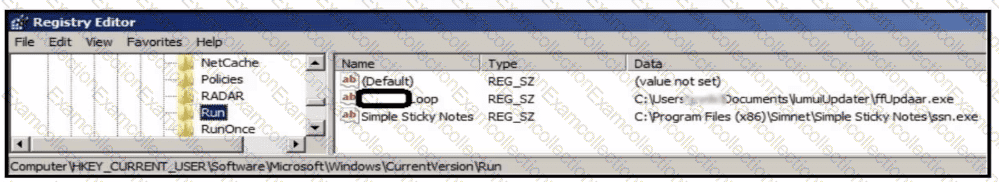
An analyst is evaluating artifacts and logs collected from recent breach. In the logs, ATP established persistency of malware by placing a path to the executable in a specific registry entry. What is the difference between the ATP's approach and using HKEY LOCAL MACHINE\Software\Microsoft\Windows\CurrentVersion\Run instead?
A SOC using Cisco security technologies wants to measure the success of its threat hunting program over time. Which metric BEST reflects increased threat hunting maturity?
A security team wants to create a plan to protect companies from lateral movement attacks. The team already implemented detection alerts for pass-the-hash and pass-the-ticket techniques. Which two components must be monitored to hunt for lateral movement attacks on endpoints? (Choose two.)
Refer to the exhibit.

A company went through several rounds of restructuring and the previous security team has been let go A new engineer joins and rediscovers all the tools thatthe previous team left behind.One of the tools Is a Bash script related to monitoring AWS accounts for threats What is the purpose of the script?
While investigating multiple incidents, analysts notice that attackers consistently use SMB for lateral movement and avoid PowerShell execution. Why is this observation valuable for attribution?
Refer to the exhibit.
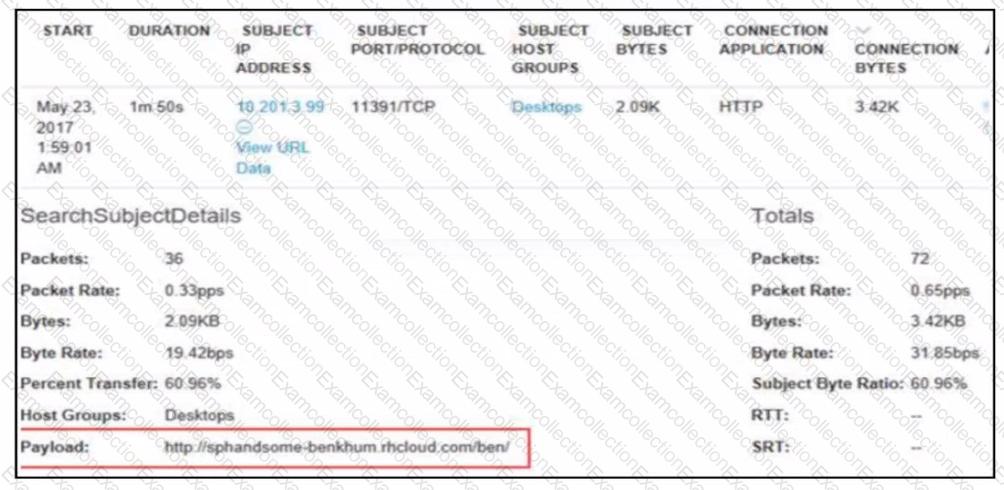
A security analyst receives an alert from Cisco Secure Network Analytics (formerly StealthWatch) with the C2 category. Which information aids the investigation?
Which hunting technique is MOST effective for detecting stealthy data exfiltration over standard web protocols?
A threat hunter wants to detect fileless malware activity usingCisco Secure Endpoint. Which behavior would MOST strongly indicate fileless execution?
A threat hunting team is attempting to attribute a series of intrusions across multiple organizations to a known threat actor. The malware binaries differ across incidents, infrastructure changes frequently, and IP addresses rotate daily. Which evidence provides the STRONGEST basis for confident attribution?



