Cisco 300-425 - Designing Cisco Enterprise Wireless Networks (ENWLSD)
A customer is concerned about mesh backhaul link security. Which level of encryption does the backhaul link use?
Refer to the exhibit.
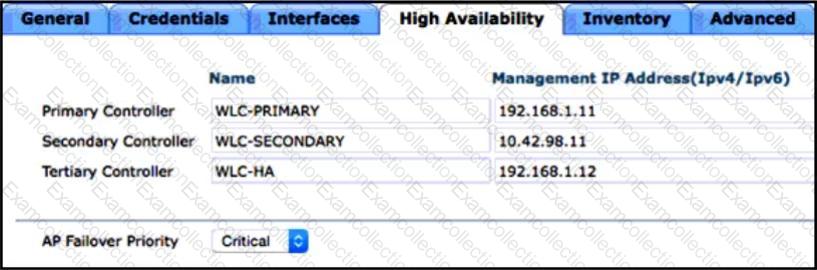
A network engineer has identified that during a recent controller failure, several APs failed over to the tertiary controller instead of the secondary controller. The configuration from one of the APs is provided. Which design consideration led to the issue?
A rapidly expanding company has tasked their network engineer with wirelessly connecting a new cubicle area with Cisco workgroup bridges until the wired network is complete. Each of 42 new users has a computer and VoIP phone. How many APs for workgroup bridging must be ordered to keep cost at a minimum while connecting all devices?
Which solution benefits from signal attenuation and provides channel reuse for high-density WI-FI deployment in an amphitheater?
During a meeting to gather the requirements for a new Wi-Fi network design, the customer requests that to connect. Which affect does this have to the wireless network?
An architect configures a set of AirOS controllers to be in the same mobility group as the existing controllers. The implementation should facilitate inter-controller roaming for users in their new campus. After the configuration, the mobility tunnel is not operational for the data path in the network. Which two validations should be performed? (Choose two.)
Which survey is performed after deployment to ensure coverage matches design requirements?
Refer to the exhibit.
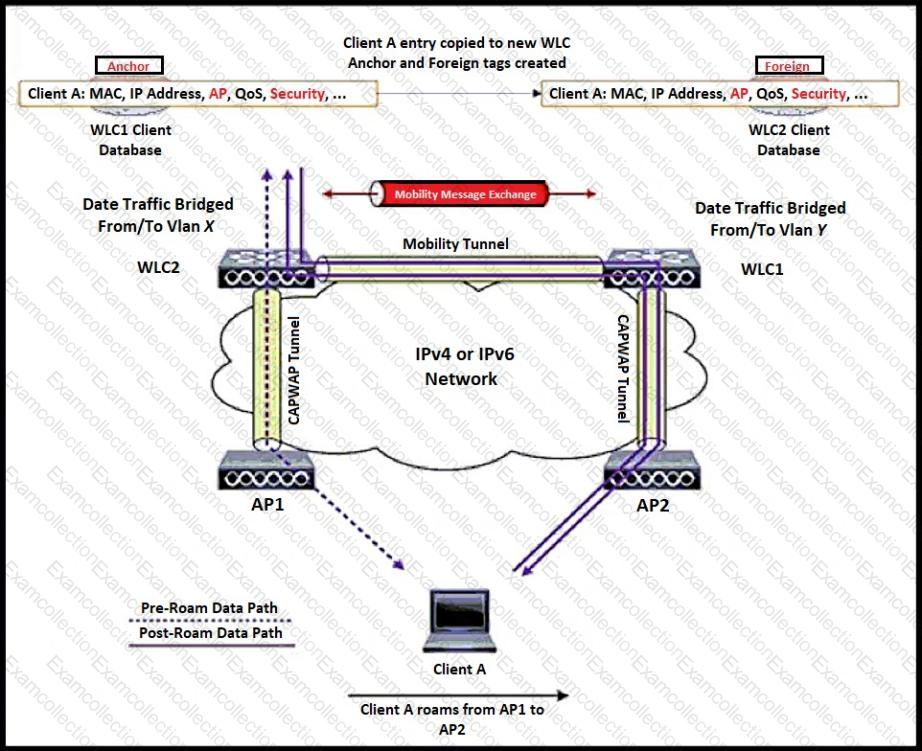
Client A is roaming from AP1 on WLC1 to AP2 on WLC2. The client roams between two APs registered to two different controllers. The WLAN on the two controllers is on a different subnet. Which scenario explains the client's roaming behavior?
Multiple WLCs are implemented in a high-availability configuration in a mobility group. APs are deployed with only a primary controller assigned. By default, which mobility group member controller do the orphaned APs join in the event of a failed controller?
A customer has a single anchor WLC named Anchor A. Anchor A is in a DMZ and provides guest access. The customer wants to deploy an additional anchor controller named Anchor B to provide redundancy if Anchor A fails. Which design approach should be taken for the guest WLAN priority on the foreign WLC for each anchor WLC?




