Cisco 300-540 - Designing and Implementing Cisco Service Provider Cloud Network Infrastructure (SPCNI v1.0)
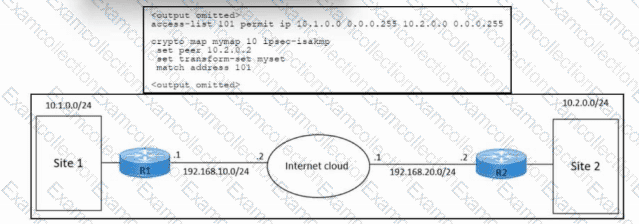
Refer to the exhibit. An engineer must configure an IPsec VPN connection between site 1 and site 2. The indicated configuration was applied to router R1; however, the tunnel fails to come up. Which command must be run on R1 to resolve the issue?
Which type of cyberattack does Cisco Umbrella DNS-layer security effectively help mitigate?
What is a benefit of using VXLANs in a cloud-scale environment?
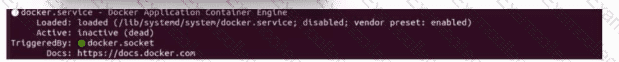
Refer to the exhibit. An engineer is troubleshooting a Cisco NFVI issue where the management node fails to start. Which service must be restarted to resolve the issue?
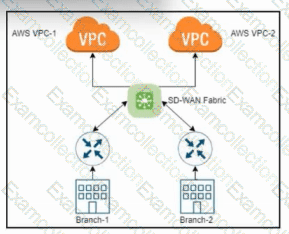
Refer to the exhibit. An engineer must design a solution that allows a user to choose which private Cisco Catalyst SD-WAN network they want to connect to AWS. The solution must automatically identify the AWS VPC and other cloud services based on the user credentials. What must be used?
What does Cisco Always-On Cloud DDoS use to protect against DDoS attacks?
How does log management assist in meeting the requirements of cloud security regulatory compliance?
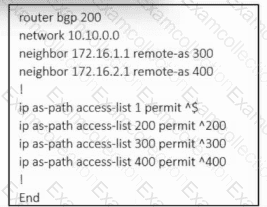
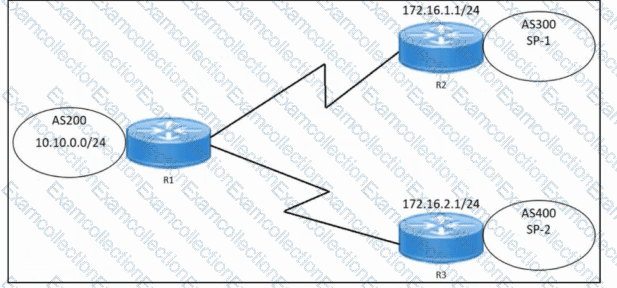
Refer to the exhibit. An engineer must configure multihoming between router R1 and service providers SP-1 and SP-2. Locally generated routes must be advertised to the service providers, and should prevent the risk that the local autonomous system becomes a transit AS for Internet traffic. Which two commands must be run on R1 to complete the configuration? (Choose two.)



