Cisco 300-710 - Securing Networks with Cisco Firepower (300-710 SNCF)
An engineer must change the mode of a Cisco Secure Firewall Threat Defense (FTD) firewall in the Cisco Secure Firewall Management Center (FMC) inventory. The engineer must take these actions:
• Register Secure FTD with Secure FMC.
• Change the firewall mode.
• Deregister the Secure FTD device from Secure FMC.
How must the engineer take FTD take the actions?
A company is deploying intrusion protection on multiple Cisco FTD appliances managed by Cisco FMC. Which system-provided policy must be selected if speed and detection are priorities?
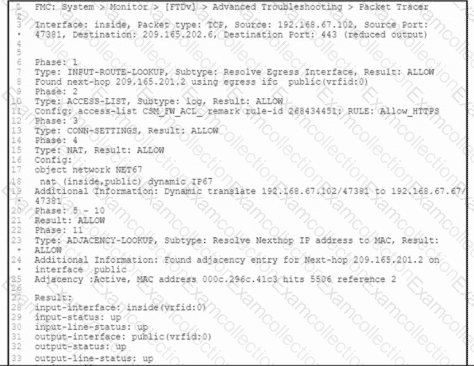
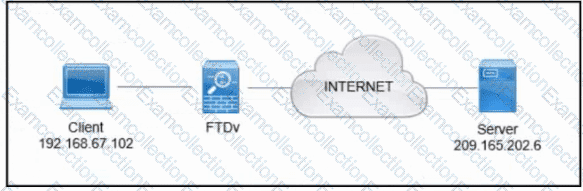
Refer to the exhibit. A client that has IP address 192.168.67.102 reports issues when connecting to a remote server. Based on the topology and output of packet tracer tool, which action resolves the connectivity issue?
An engineer wants to change an existing transparent Cisco FTD to routed mode.
The device controls traffic between two network segments. Which action is mandatory to allow hosts to reestablish communication between these two segments after the change?
A network engineer must monitor threat events from the console of Cisco Secure Firewall Management Center. The engineer integrates the Cisco Secure Firewall Malware Defense in Secure Firewall Management Center. Which action must the engineer take next?



