Cisco 300-715 - Implementing and Configuring Cisco Identity Services Engine (SISE) v4.0 (300-715 SISE)
What is a difference between RADIUS versus TACACS+ with regards to packet encryption?
An administrator wants to configure network device administration and is trying to decide whether to use TACACS* or RADIUS. A reliable protocol must be used that can check command authorization Which protocol meets these requirements and why?
An organization is adding nodes to their Cisco ISE deployment and has two nodes designated as primary and secondary PAN and MnT nodes. The organization also has four PSNs An administrator is adding two more PSNs to this deployment but is having problems adding one of them What is the problem?
An engineer has been tasked with standing up a new guest portal for customers that are waiting in the lobby. There is a requirement to allow guests to use their social media logins to access the guest network to appeal to more customers What must be done to accomplish this task?
An administrator is editing a csv list of endpoints and wants to reprofile some of the devices indefinitely before importing the list into Cisco ISE. Which field and Boolean value must be changed for the devices before the list is reimported?
An engineer must configure guest access on Cisco ISE for company visitors. Which step must be taken on the Cisco ISE PSNs before a guest portal is configured?
Which Cisco ISE service allows an engineer to check the compliance of endpoints before connecting to the network?
An administrator is configuring sponsored guest access using Cisco ISE Access must be restricted to the sponsor portal to ensure that only necessary employees can issue sponsored accounts and employees must be classified to do so What must be done to accomplish this task?
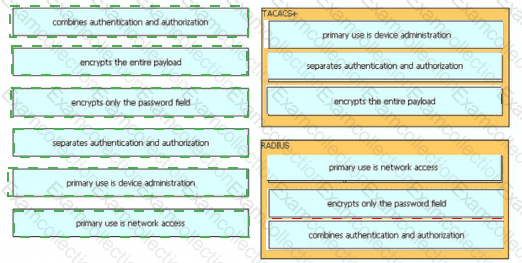
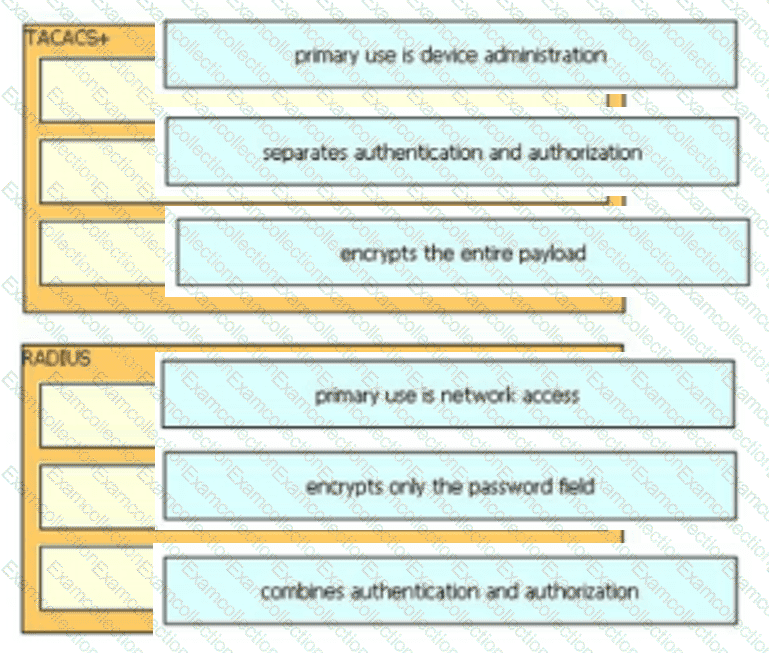
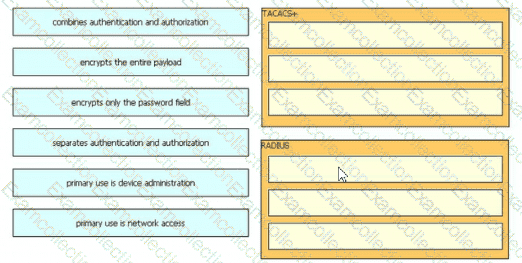
Drag and drop the description from the left onto the protocol on the right that is used to carry out system authentication, authentication, and accounting.
Which two features are available when the primary admin node is down and the secondary admin node has not been promoted? (Choose two.)