Cisco 300-720 - Securing Email with Cisco Email Security Appliance (300-720 SESA)
What is the maximum message size that can be configured for encryption on the Cisco ESA?
When email authentication is configured on Cisco ESA, which two key types should be selected on the signing profile? (Choose two.)
What is the default method of remotely accessing a newly deployed Cisco Secure Email Virtual Gateway when a DHCP server is not available?
A security administrator deployed a Cisco Secure Email Gateway appliance with a mail policy configured to store suspected spam for review. The appliance is the DMZ and only the standard HTTP/HTTPS ports are allowed by the firewall. An administrator wants to ensure that users can view any suspected spam that was blocked. Which action must be taken to meet this requirement?
When a network engineer is troubleshooting a mail flow issue, they discover that some emails are rejected with an SMTP code of 451 and the error message "#4.7.1 Unable to perform DMARC verification". In the DMARC verification profile on the Cisco Secure Email Gateway appliance, which action must be set for messages that result in temporary failure to prevent these emails from being rejected?
Which attack is mitigated by using Bounce Verification?
An organization wants to use DMARC to improve its brand reputation by leveraging DNS records.
Which two email authentication mechanisms are utilized during this process? (Choose two.)
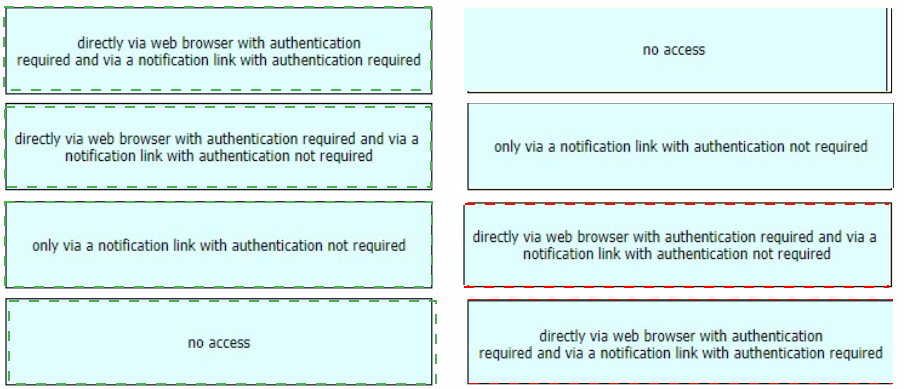
Drag and drop authentication options for End-User Quarantine Access from the left onto the corresponding configuration steps on the right.
Which two factors must be considered when message filter processing is configured? (Choose two.)
What is the default port to deliver emails from the Cisco ESA to the Cisco SMA using the centralized Spam Quarantine?