Cisco 300-740 - Designing and Implementing Secure Cloud Access for Users and Endpoints (SCAZT)
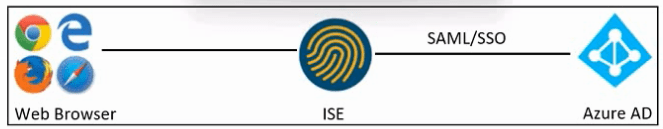
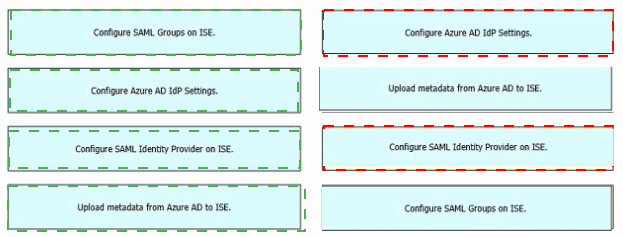
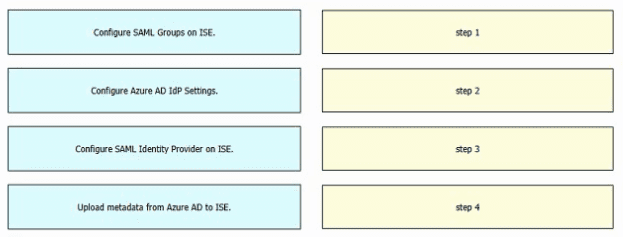
Refer to the exhibit. An engineer must configure SAML single sign-on in Cisco ISE to use Microsoft Azure AD as an identity provider. Drag and drop the steps from the left into the sequence on the right to configure Cisco ISE with SAML single sign-on.
What does the MITRE ATT&CK framework catalog?
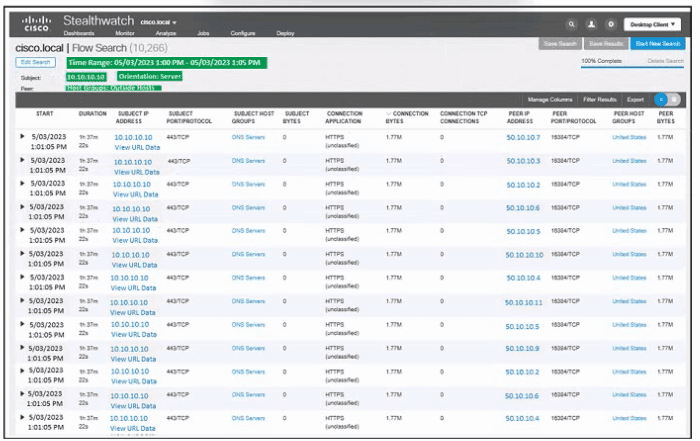
Refer to the exhibit. An engineer must troubleshoot an incident by using Cisco Secure Cloud Analytics. What is the cause of the issue?
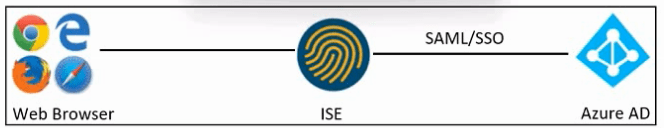
Refer to the exhibit. An engineer must configure SAML SSO in Cisco ISE to use Microsoft Azure AD as an identity provider. These configurations were performed:
Configure a SAML IdP in ISE.
Configure the Azure AD IdP settings.
Which two actions must the engineer take in Cisco ISE? (Choose two.)
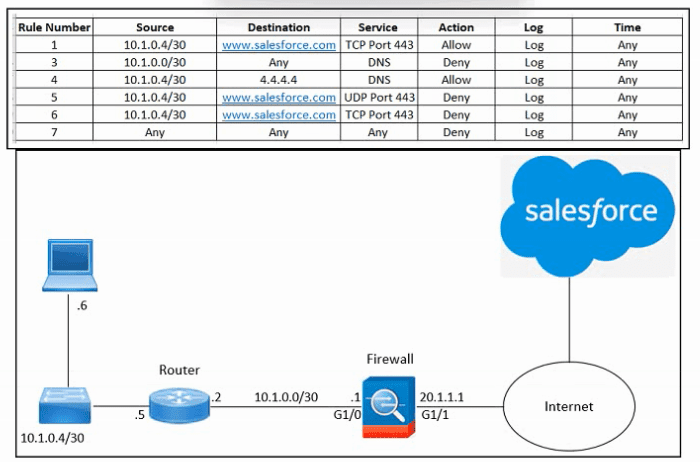
Refer to the exhibit. An engineer must configure the Cisco ASA firewall to allow the client with IP address 10.1.0.6 to access the Salesforce login page at https://www.salesforce.com. The indicated configuration was applied to the firewall and public DNS 4.4.4.4 is used for name resolution; however, the client still cannot access the URL. What should be done to meet the requirements?
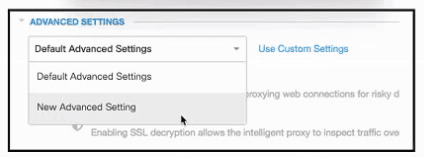
Refer to the exhibit. An engineer must configure a global allow list in Cisco Umbrella for the cisco.com domain. All other domains must be blocked. After creating a new policy and adding the cisco.com domain, the engineer attempts to access a site outside of cisco.com and is successful. Which additional Security Settings action must be taken to meet the requirement?
Which mitigation technique does a web application firewall use to protect a web server against DDoS attacks?
Which common strategy should be used to mitigate directory traversal attacks in a cloud environment?