F5 301a - BIG-IP LTM Specialist: Architect Set-Up & Deploy
A virtual server is experiencing intermittent port exhaustion. What should be done to fix this issue?
An LTM specialist needs to upgrade a VCMP quest in an HA Setup with minimum interruption for all VCMP guest instances.
In which should the LTM Specialist perform this upgrade?
RADIUS authentication has been configured on the LTM device. The default remote user access requirements are as shown:
Read only access to the configuration Utility
Access to TMOS shell
Which two items need to be configured in this situation? (Choose two)
Exhibit.
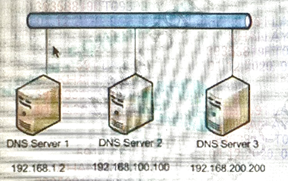
The server team has recently configured the three new DNS servers shown for the data center. No current DNS servers are currently configured on the LTM device.
Which command should be used to configure the LTM device to use the new DNS servers?
An LTM Specialist needs to force only FTP traffic, sourced from subnet 10.10.10.0/24 to virtual server 10.10.20.1 to the new FTP1 server. The following virtual servers are configured on the LTM device:
Traffic sourced from 10.10.10/24 must use the specific pool member for load balancing.
Which configuration change is needed to meet the requirements?
An LTM Specialist has noticed in the audit log that there are numerous attempts to log into the Admin account. Theses attempts are sourced from a suspicious IP address range to the Configuration Utility of the LTM device.
How should the LTM Specialist block these attempts?
An LTM Specialist configures a new HTTPS virtual server that contains a valid example.com ssl certificate. The LTM Special receives an error in the browser when connecting.
What must be added to the SSL Client profile to fix this issue?
The picture belongs to static content, you can configure static content cache in FS to meet this demand
An LTM Specialist must configure session persistence for a highly available, highly utilized web-based application.
* The following requirements are provided:
* http proxy setup for security
persistence information available to the HA peer in case of failover
The LTM Specialist needs to minimize additional burden on the LTM device to the greatest extent possible.
Which persistence profile should be used?
A virtual server configuration for traffic destined to a server is as shown:
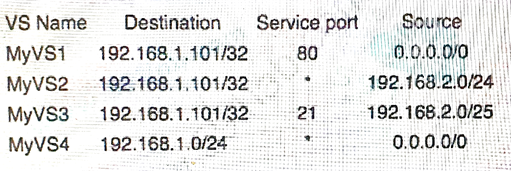
FTP traffic is destined to the 192.168.1.101 server from the source of 192.168.2.129.
Based on precedence, which virtual server accepts this traffic?
A pool has four members. Ail of the servers have been designed and configured with the same application. Each client's request can significantly the performance of the servers.
Which load balancing method should the LTM Specialist use to maintain a relatively even load across all servers?



