ECCouncil 312-96 - Certified Application Security Engineer (CASE) JAVA
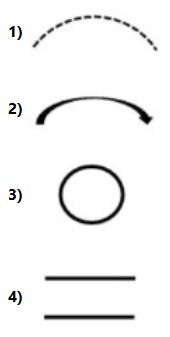
Which of the following DFD component is used to represent the change in privilege levels?
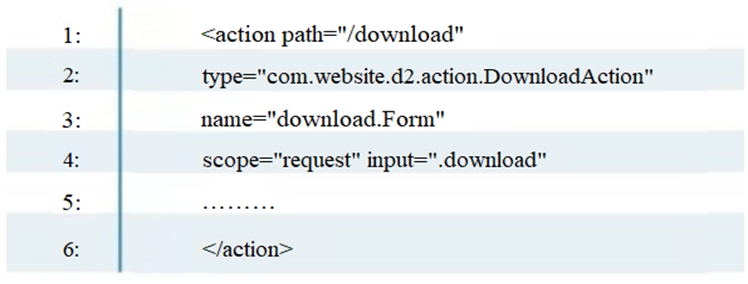
To enable the struts validator on an application, which configuration setting should be applied in the struts validator configuration file?
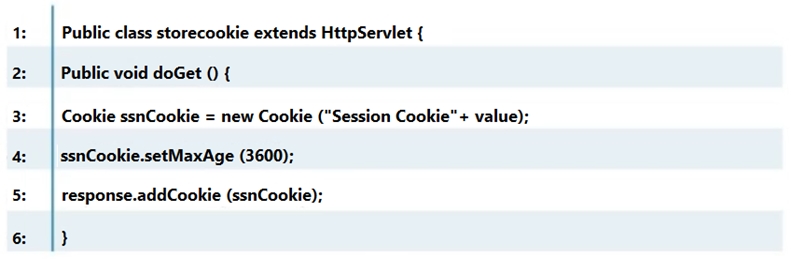
Which line of the following example of Java Code can make application vulnerable to a session attack?
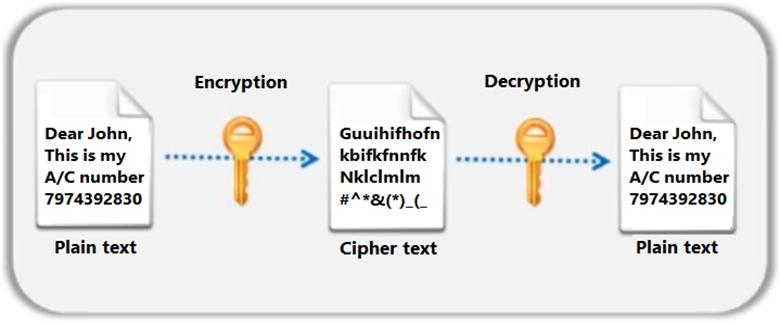
Identify the type of encryption depicted in the following figure.