Cisco 350-201 - Performing CyberOps Using Core Security Technologies (CBRCOR)
Refer to the exhibit.
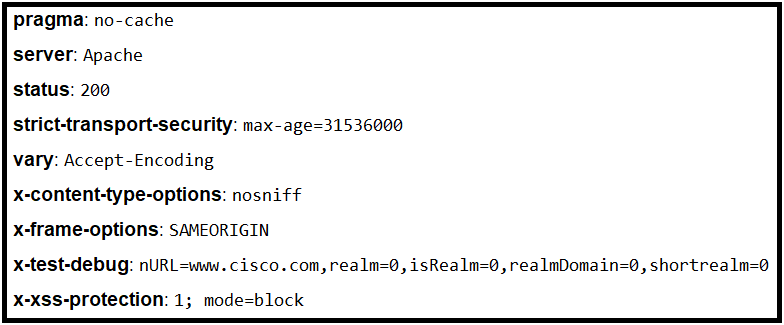
Where is the MIME type that should be followed indicated?
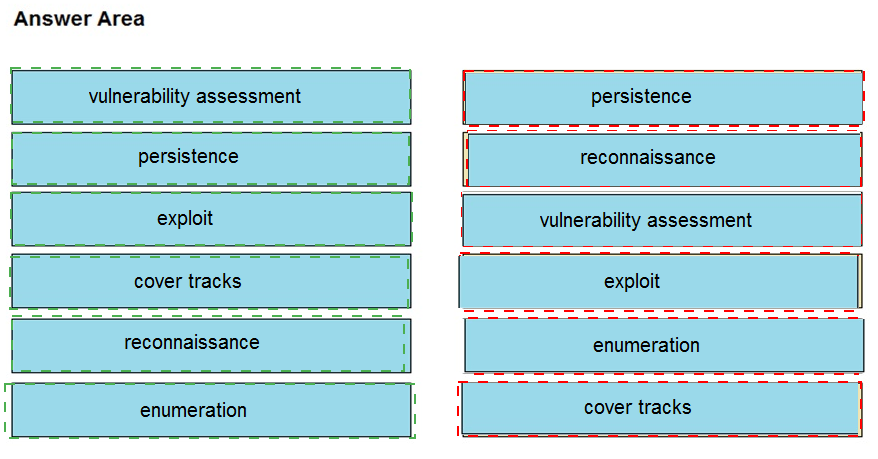
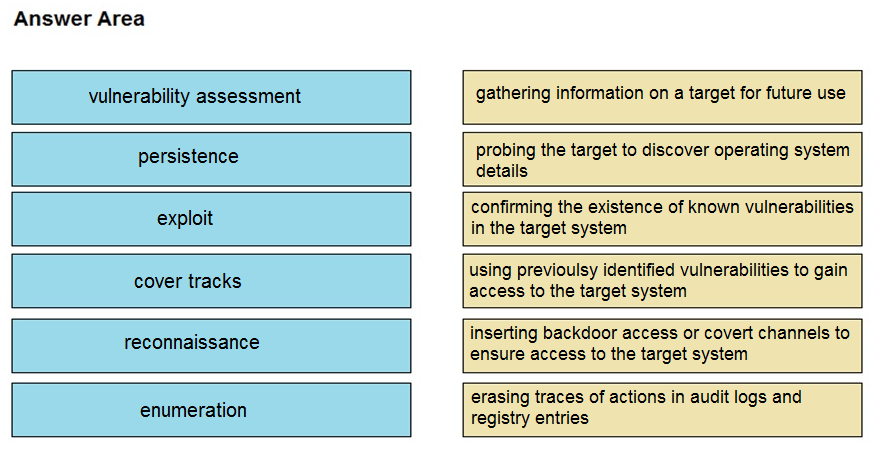
Drag and drop the phases to evaluate the security posture of an asset from the left onto the activity that happens during the phases on the right.
A security analyst receives an escalation regarding an unidentified connection on the Accounting A1 server within a monitored zone. The analyst pulls the logs and discovers that a Powershell process and a WMI tool process were started on the server after the connection was established and that a PE format file was created in the system directory. What is the next step the analyst should take?
An organization installed a new application server for IP phones. An automated process fetched user credentials from the Active Directory server, and the application will have access to on-premises and cloud services. Which security threat should be mitigated first?
An engineer is analyzing a possible compromise that happened a week ago when the company? (Choose two.)
Refer to the exhibit.
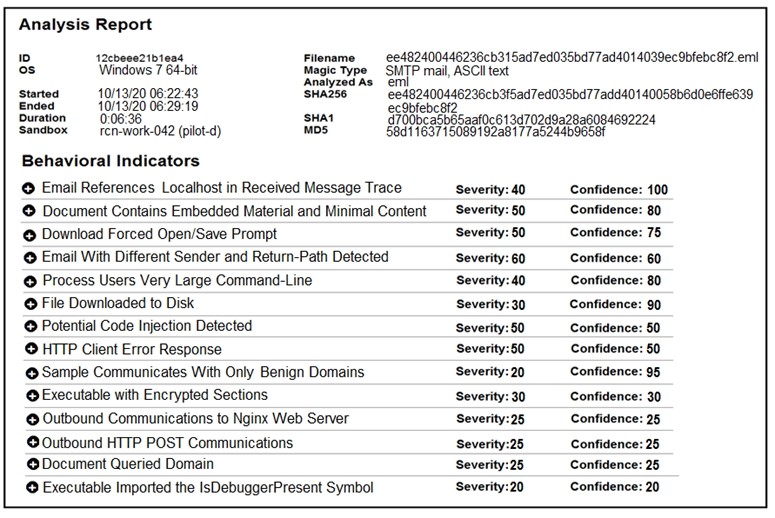
Cisco Advanced Malware Protection installed on an end-user desktop automatically submitted a low prevalence file to the Threat Grid analysis engine. What should be concluded from this report?
Refer to the exhibit.
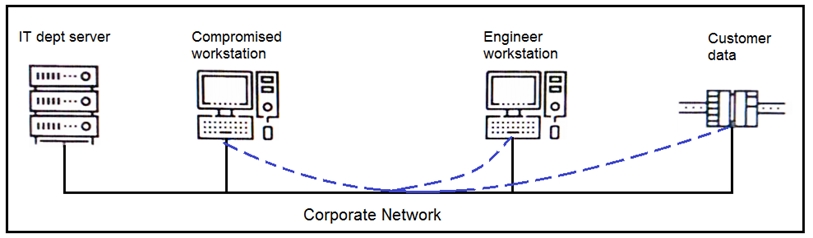
An engineer received a report that an attacker has compromised a workstation and gained access to sensitive customer data from the network using insecure protocols. Which action prevents this type of attack in the future?
A logistic company must use an outdated application located in a private VLAN during the migration to new technologies. The IPS blocked and reported an unencrypted communication. Which tuning option should be applied to IPS?
Refer to the exhibit.
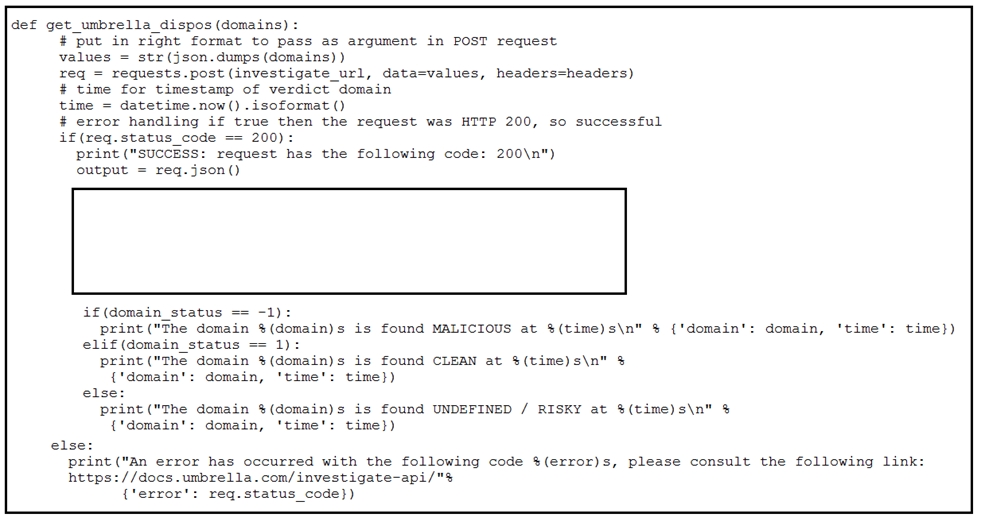
Which code snippet will parse the response to identify the status of the domain as malicious, clean or undefined?
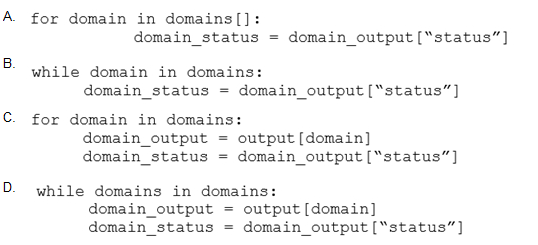
A SOC team receives multiple alerts by a rule that detects requests to malicious URLs and informs the incident response team to block the malicious URLs requested on the firewall. Which action will improve the effectiveness of the process?