Cisco 350-201 - Performing CyberOps Using Core Security Technologies (CBRCOR)
An employee who often travels abroad logs in from a first-seen country during non-working hours. The SIEM tool generates an alert that the user is forwarding an increased amount of emails to an external mail domain and then logs out. The investigation concludes that the external domain belongs to a competitor. Which two behaviors triggered UEBA? (Choose two.)
What is a limitation of cyber security risk insurance?
Which command does an engineer use to set read/write/execute access on a folder for everyone who reaches the resource?
What is the HTTP response code when the REST API information requested by the authenticated user cannot be found?
Refer to the exhibit.
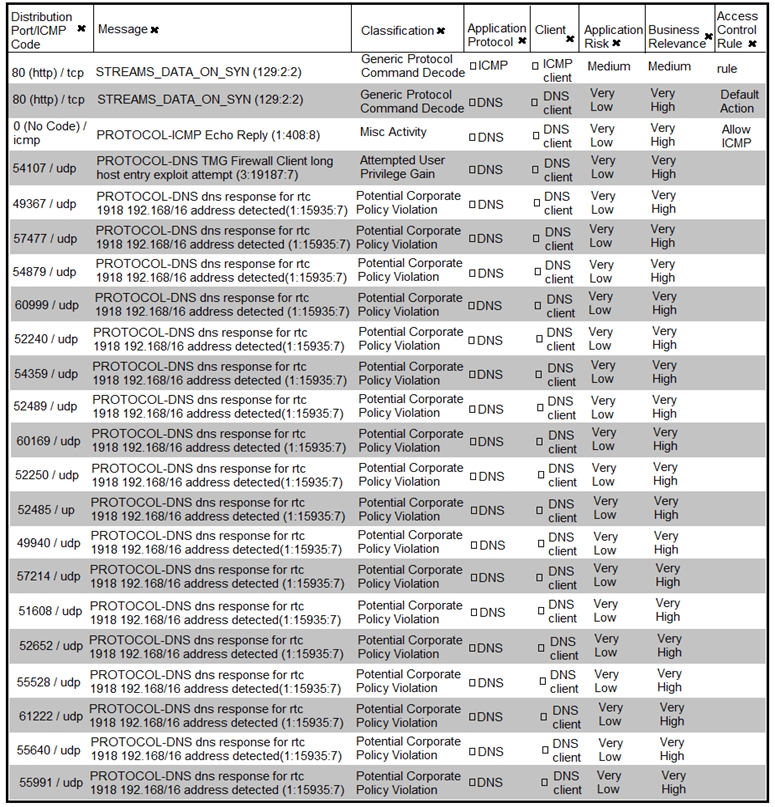
What is the connection status of the ICMP event?
Refer to the exhibit.
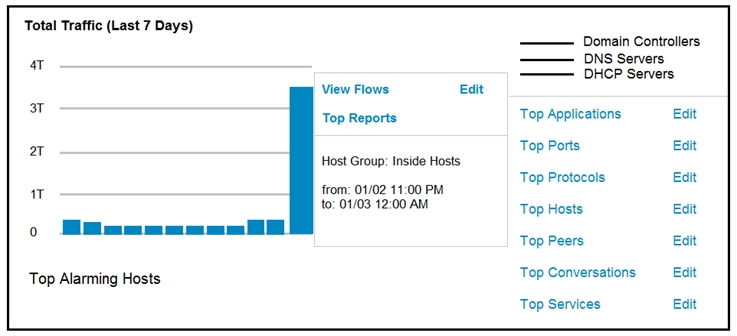
An engineer notices a significant anomaly in the traffic in one of the host groups in Cisco Secure Network Analytics (Stealthwatch) and must analyze the top data transmissions. Which tool accomplishes this task?
A payroll administrator noticed unexpected changes within a piece of software and reported the incident to the incident response team. Which actions should be taken at this step in the incident response workflow?
An employee abused PowerShell commands and script interpreters, which lead to an indicator of compromise (IOC) trigger. The IOC event shows that a known malicious file has been executed, and there is an increased likelihood of a breach. Which indicator generated this IOC event?
Refer to the exhibit.
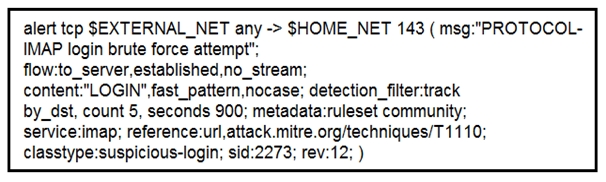
IDS is producing an increased amount of false positive events about brute force attempts on the organization’s mail server. How should the Snort rule be modified to improve performance?
A Mac laptop user notices that several files have disappeared from their laptop documents folder. While looking for the files, the user notices that the browser history was recently cleared. The user raises a case, and an analyst reviews the network usage and discovers that it is abnormally high. Which step should be taken to continue the investigation?



