Cisco 350-201 - Performing CyberOps Using Core Security Technologies (CBRCOR)
Refer to the exhibit.
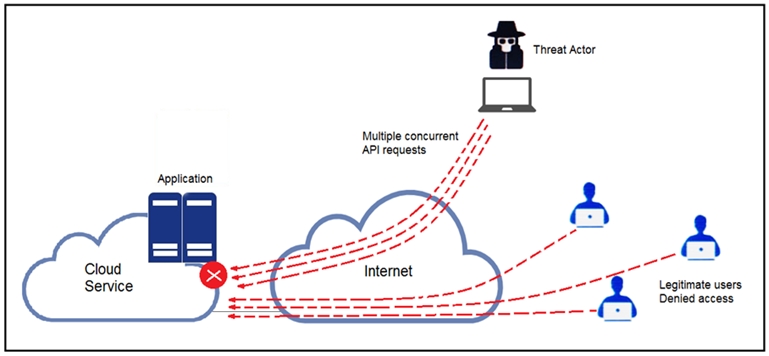
A threat actor behind a single computer exploited a cloud-based application by sending multiple concurrent API requests. These requests made the application unresponsive. Which solution protects the application from being overloaded and ensures more equitable application access across the end-user community?
Refer to the exhibit.
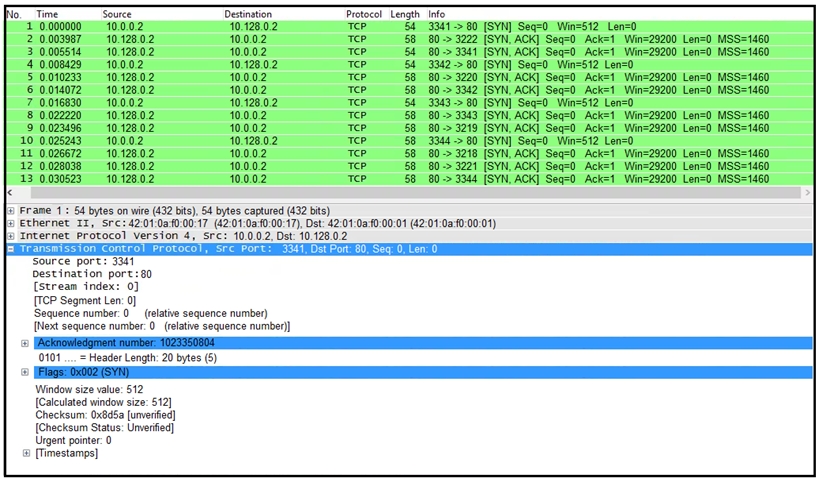
What is the threat in this Wireshark traffic capture?
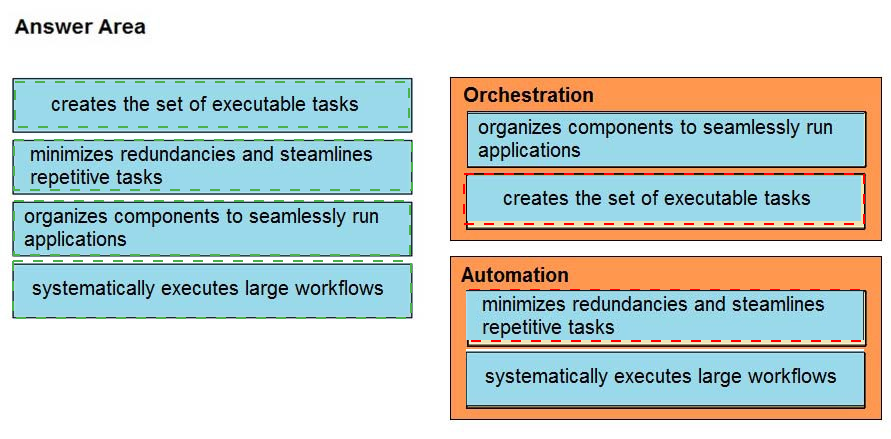
Drag and drop the function on the left onto the mechanism on the right.
An audit is assessing a small business that is selling automotive parts and diagnostic services. Due to increased customer demands, the company recently started to accept credit card payments and acquired a POS terminal. Which compliance regulations must the audit apply to the company?
A cloud engineer needs a solution to deploy applications on a cloud without being able to manage and control the server OS. Which type of cloud environment should be used?
An engineer is investigating several cases of increased incoming spam emails and suspicious emails from the HR and service departments. While checking the event sources, the website monitoring tool showed several web scraping alerts overnight. Which type of compromise is indicated?
Refer to the exhibit.
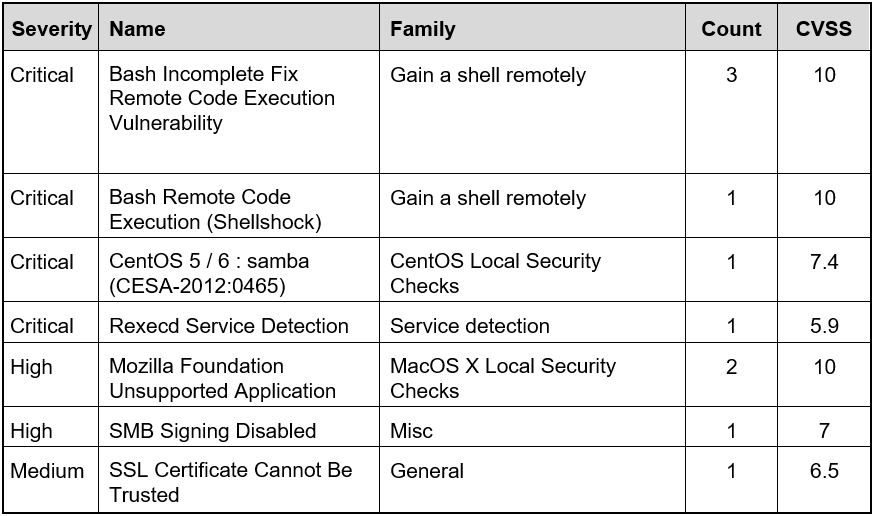
Based on the detected vulnerabilities, what is the next recommended mitigation step?
Refer to the exhibit.

At which stage of the threat kill chain is an attacker, based on these URIs of inbound web requests from known malicious Internet scanners?
Refer to the exhibit.
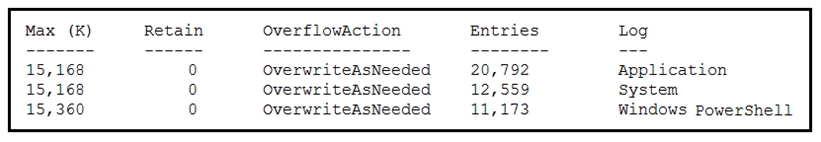
An employee is a victim of a social engineering phone call and installs remote access software to allow an “MS Support†technician to check his machine for malware. The employee becomes suspicious after the remote technician requests payment in the form of gift cards. The employee has copies of multiple, unencrypted database files, over 400 MB each, on his system and is worried that the scammer copied the files off but has no proof of it. The remote technician was connected sometime between 2:00 pm and 3:00 pm over https. What should be determined regarding data loss between the employee’s laptop and the remote technician’s system?
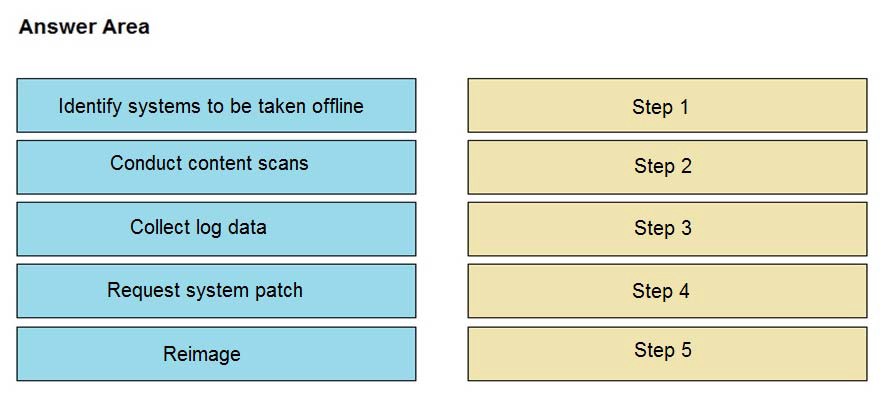
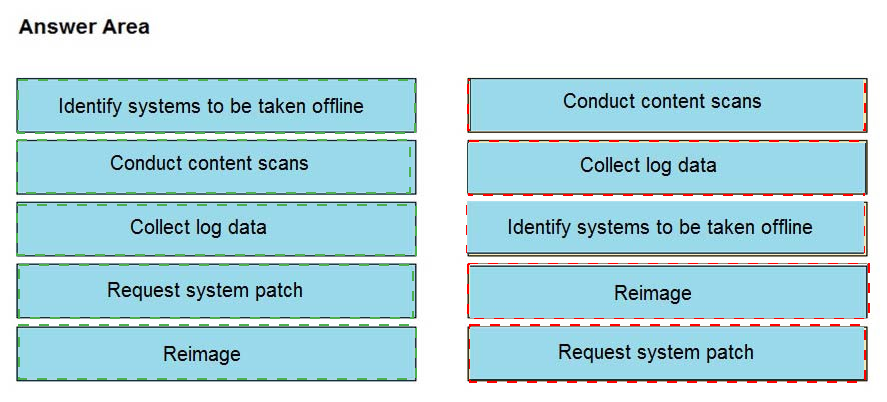
An engineer notices that unauthorized software was installed on the network and discovers that it was installed by a dormant user account. The engineer suspects an escalation of privilege attack and responds to the incident. Drag and drop the activities from the left into the order for the response on the right.