Cisco 350-701 - Implementing and Operating Cisco Security Core Technologies (SCOR 350-701)
Which cloud model is a collaborative effort where infrastructure is shared and jointly accessed by several organizations from a specific group?
Which policy does a Cisco Secure Web Appliance use to block or monitor URL requests based on the reputation score?
An engineer needs to configure an access control policy rule to always send traffic for inspection without
using the default action. Which action should be configured for this rule?
Refer to the exhibit.
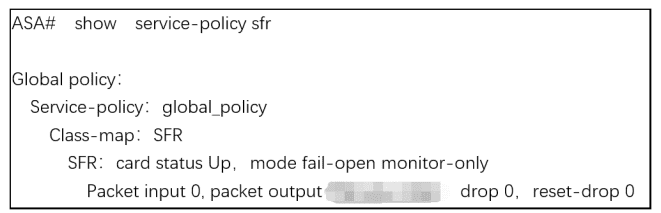
What are two indications of the Cisco Firepower Services Module configuration?
(Choose two.)
Which solution is more secure than the traditional use of a username and password and encompasses at least two of the methods of authentication?
A network administrator is setting up Cisco FMC to send logs to Cisco Security Analytics and Logging (SaaS). The network administrator is anticipating a high volume of logging events from the firewalls and wants lo limit the strain on firewall resources. Which method must the administrator use to send these logs to Cisco Security Analytics and Logging?
Refer to the exhibit.
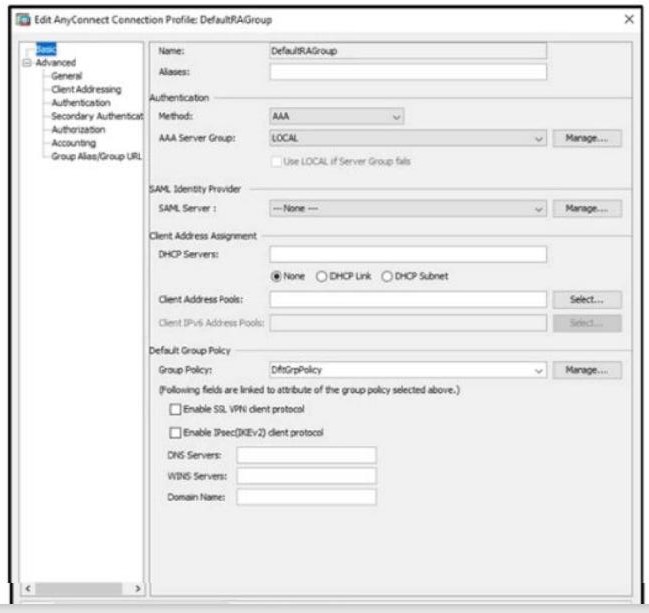
When configuring a remote access VPN solution terminating on the Cisco ASA, an administrator would like to utilize an external token authentication mechanism in conjunction with AAA authentication using machine
certificates. Which configuration item must be modified to allow this?
What is the role of an endpoint in protecting a user from a phishing attack?
An engineer is configuring guest WLAN access using Cisco ISE and the Cisco WLC. Which action temporarily gives guest endpoints access dynamically while maintaining visibility into who or what is connecting?
Which term describes when the Cisco Firepower downloads threat intelligence updates from Cisco Talos?
Which two methods must be used to add switches into the fabric so that administrators can control how switches are added into DCNM for private cloud management? (Choose two.)
What is provided by the Secure Hash Algorithm in a VPN?
Which PKI enrollment method allows the user to separate authentication and enrollment actions and also
provides an option to specify HTTP/TFTP commands to perform file retrieval from the server?
With regard to RFC 5176 compliance, how many IETF attributes are supported by the RADIUS CoA feature?
Refer to the exhibit. A network engineer must configure a Cisco router to send traps using SNMPv3. The engineer configures a remote user to receive traps and sets the security level to use authentication without privacy. Which command completes the configuration?



