Cisco 350-701 - Implementing and Operating Cisco Security Core Technologies (SCOR 350-701)
Which deployment model is the most secure when considering risks to cloud adoption?
Which two request methods of REST API are valid on the Cisco ASA Platform? (Choose two.)
Why should organizations migrate to a multifactor authentication strategy?
Which feature of Cisco ASA allows VPN users to be postured against Cisco ISE without requiring an inline
posture node?
What is a commonality between DMVPN and FlexVPN technologies?
What does Cisco AMP for Endpoints use to help an organization detect different families of malware?
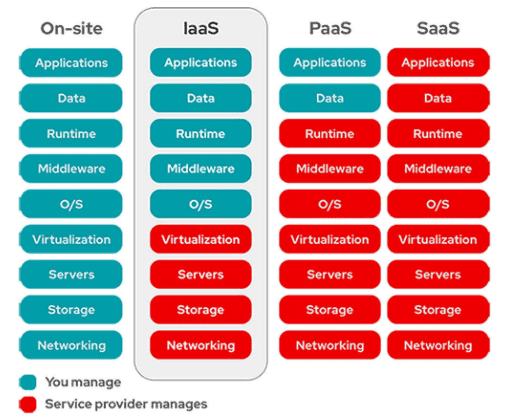
Which two aspects of the cloud PaaS model are managed by the customer but not the provider? (Choose two)
Which two commands are required when configuring a flow-export action on a Cisco ASA? (Choose two.)
What is an attribute of the DevSecOps process?
A network administrator has configured TACACS on a network device using the key Cisc0467380030 tor authentication purposes. However, users are unable to authenticate. TACACS server is reachable, but authentication is tailing. Which configuration step must the administrator complete?
An engineer is configuring their router to send NetfFow data to Stealthwatch which has an IP address of 1 1 11 using the flow record Stea!thwatch406397954 command Which additional command is required to complete the flow record?
Under which two circumstances is a CoA issued? (Choose two)
Which Cisco security solution provides patch management in the cloud?
Which two descriptions of AES encryption are true? (Choose two)
A Cisco FTD engineer is creating a new IKEv2 policy called s2s00123456789 for their organization to allow for additional protocols to terminate network devices with. They currently only have one policy established and need the new policy to be a backup in case some devices cannot support the stronger algorithms listed in the primary policy. What should be done in order to support this?