Cisco 350-701 - Implementing and Operating Cisco Security Core Technologies (SCOR 350-701)
A network administrator is using the Cisco ESA with AMP to upload files to the cloud for analysis. The network
is congested and is affecting communication. How will the Cisco ESA handle any files which need analysis?
An engineer has been tasked with implementing a solution that can be leveraged for securing the cloud users,
data, and applications. There is a requirement to use the Cisco cloud native CASB and cloud cybersecurity
platform. What should be used to meet these requirements?
Which two characteristics of messenger protocols make data exfiltration difficult to detect and prevent?
(Choose two)
In which situation should an Endpoint Detection and Response solution be chosen versus an Endpoint Protection Platform?
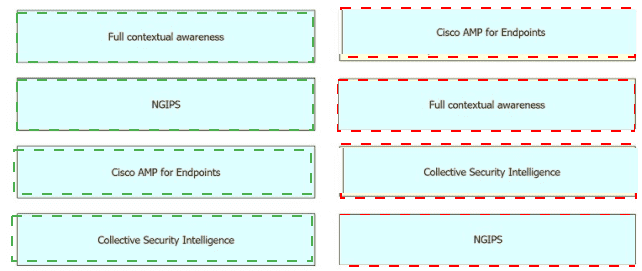
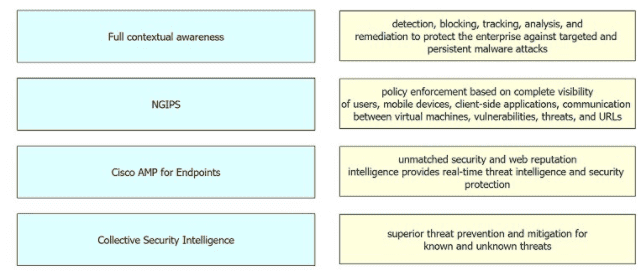
Drag and drop the security solutions from the left onto the benefits they provide on the right.
What is the concept of Cl/CD pipelining?
Which form of attack is launched using botnets?
What is a feature of the open platform capabilities of Cisco DNA Center?
How does a Cisco Secure Firewall help to lower the risk of exfiltration techniques that steal customer data?
Which Cisco Secure Client module is integrated with Splunk Enterprise to provide monitoring capabilities to administrators to allow them to view endpoint application usage?
What is a functional difference between Cisco Secure Endpoint and Cisco Umbrella Roaming Client?
What is a functional difference between Cisco AMP for Endpoints and Cisco Umbrella Roaming Client?
What is a difference between an XSS attack and an SQL injection attack?
What is the term for the concept of limiting communication between applications or containers on the same node?
What are the components of endpoint protection against social engineering attacks?