Cisco 350-701 - Implementing and Operating Cisco Security Core Technologies (SCOR 350-701)
Which metric is used by the monitoring agent to collect and output packet loss and jitter information?
What is a feature of NetFlow Secure Event Logging?
Which VPN technology can support a multivendor environment and secure traffic between sites?
A company identified a phishing vulnerability during a pentest What are two ways the company can protect employees from the attack? (Choose two.)
An administrator is trying to determine which applications are being used in the network but does not want the
network devices to send metadata to Cisco Firepower. Which feature should be used to accomplish this?
Which type of dashboard does Cisco Catalyst Center provide for complete control of the network?
An engineer must force an endpoint to re-authenticate an already authenticated session without disrupting the
endpoint to apply a new or updated policy from ISE. Which CoA type achieves this goal?
A network engineer entered the snmp-server user asmith myv7 auth sha cisco priv aes 256
cisc0xxxxxxxxx command and needs to send SNMP information to a host at 10.255.255.1. Which
command achieves this goal?
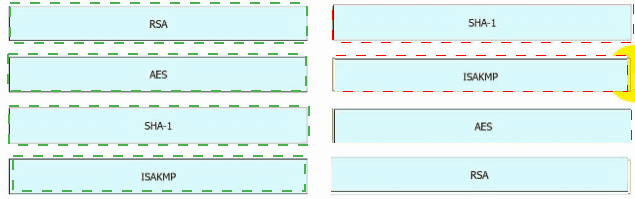
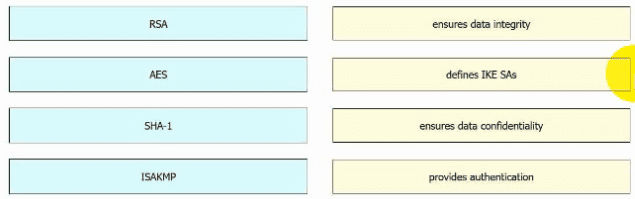
Drag and drop the VPN functions from the left onto the descriptions on the right.
Why should organizations migrate to an MFA strategy for authentication?
v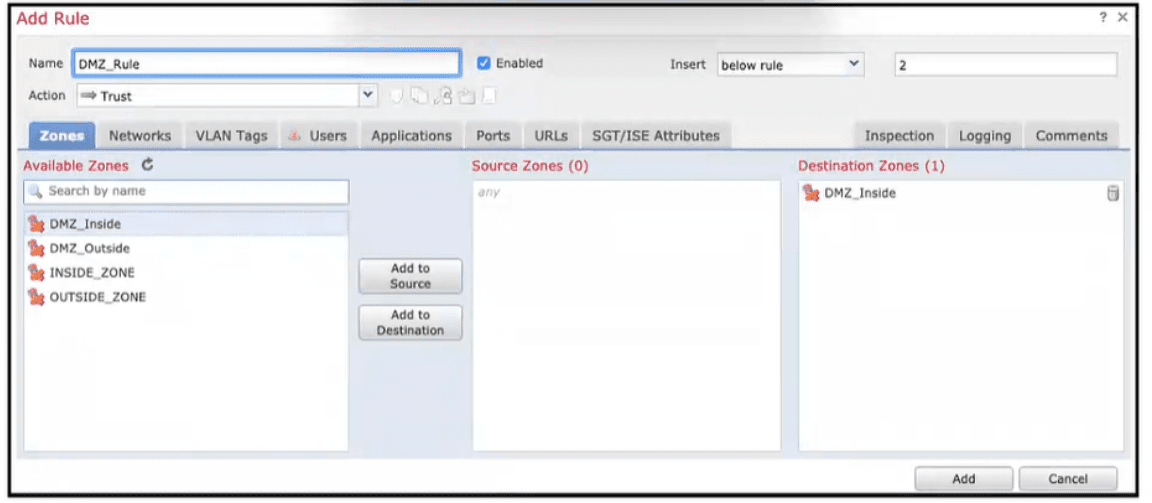
Refer to the exhibit When configuring this access control rule in Cisco FMC, what happens with the traffic destined to the DMZjnside zone once the configuration is deployed?
In which cloud services model is the customer responsible for scanning for and mitigation of application vulnerabilities?
Which feature is used to restrict communication between interfaces on a Cisco ASA?
Which solution combines Cisco IOS and IOS XE components to enable administrators to recognize applications, collect and send network metrics to Cisco Prime and other third-party management tools, and prioritize application traffic?
In which scenario is endpoint-based security the solution?