Cisco 350-701 - Implementing and Operating Cisco Security Core Technologies (SCOR 350-701)
What are the two types of managed Intercloud Fabric deployment models? (Choose two.)
Which feature requires a network discovery policy on the Cisco Firepower Next Generation Intrusion Prevention
System?
What is the recommendation in a zero-trust model before granting access to corporate applications and resources?
What are two workloaded security models? (Choose two)
Which posture assessment requirement provides options to the client for remediation and requires the
remediation within a certain timeframe?
An engineer is configuring AMP for endpoints and wants to block certain files from executing. Which outbreak
control method is used to accomplish this task?
Which command enables 802.1X globally on a Cisco switch?
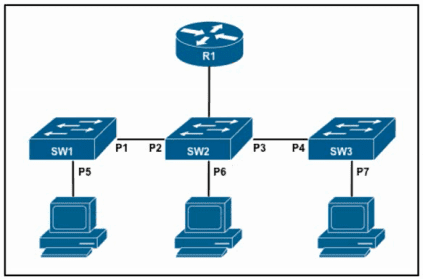
Refer to the exhibit. The DHCP snooping database resides on router R1, and dynamic ARP inspection is configured only on switch SW2. Which ports must be configured as untrusted so that dynamic ARP inspection operates normally?
In which type of attack does the attacker insert their machine between two hosts that are communicating with each other?
During a recent security audit a Cisco IOS router with a working IPSEC configuration using IKEv1 was flagged for using a wildcard mask with the crypto isakmp key command The VPN peer is a SOHO router with a dynamically assigned IP address Dynamic DNS has been configured on the SOHO router to map the dynamic IP address to the host name of vpn sohoroutercompany.com In addition to the command crypto isakmp key Cisc425007536 hostname vpn.sohoroutercompany.com what other two commands are now required on the Cisco IOS router for the VPN to continue to function after the wildcard command is removed? (Choose two)
An engineer must deploy Cisco Secure Email with Cloud URL Analysis and must meet these requirements:
To protect the network from large-scale virus outbreaks
To protect the network from non-viral attacks such as phishing scams and malware distribution
To provide active analysis of the structure of the URL and information about the domain and page contents
Which two prerequisites must the engineer ensure are configured? (Choose two.)
What is the purpose of a NetFlow version 9 template record?
What does Cisco ISE use to collect endpoint attributes that are used in profiling?
Refer to the exhibit.
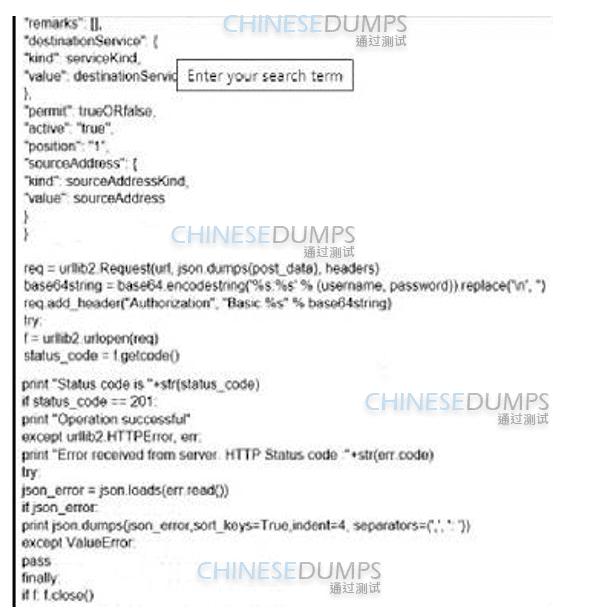
What is the function of the Python script code snippet for the Cisco ASA REST API?
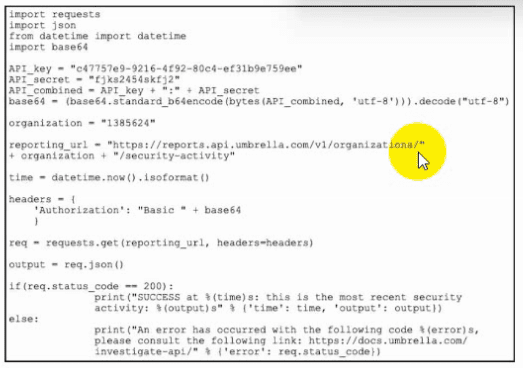
Refer to the exhibit. Which task is the Python script performing by using the Cisco Umbrella API?



