CyberArk ACCESS-DEF - CyberArk Defender Access (ACC-DEF)
Which feature does the CyberArk Identity Connector provide?
Which predefined roles does CyberArk Identity provide?
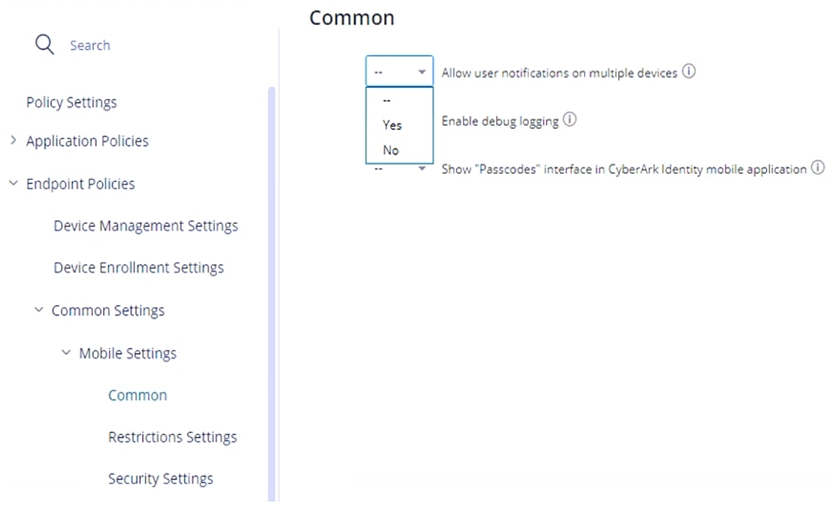
Refer to the exhibit.
Within the "Allow user notifications on multiple devices", if you leave the setting as Default (--), what happens if a user triggers a MFA Push notification and has enrolled three different devices?
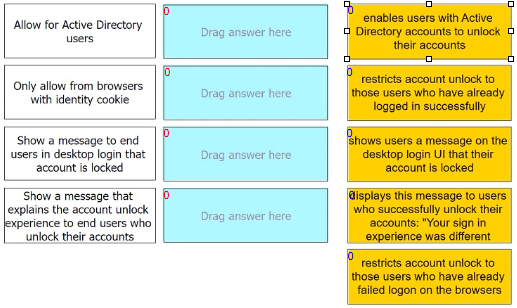
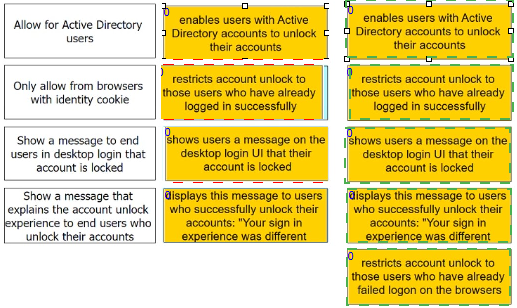
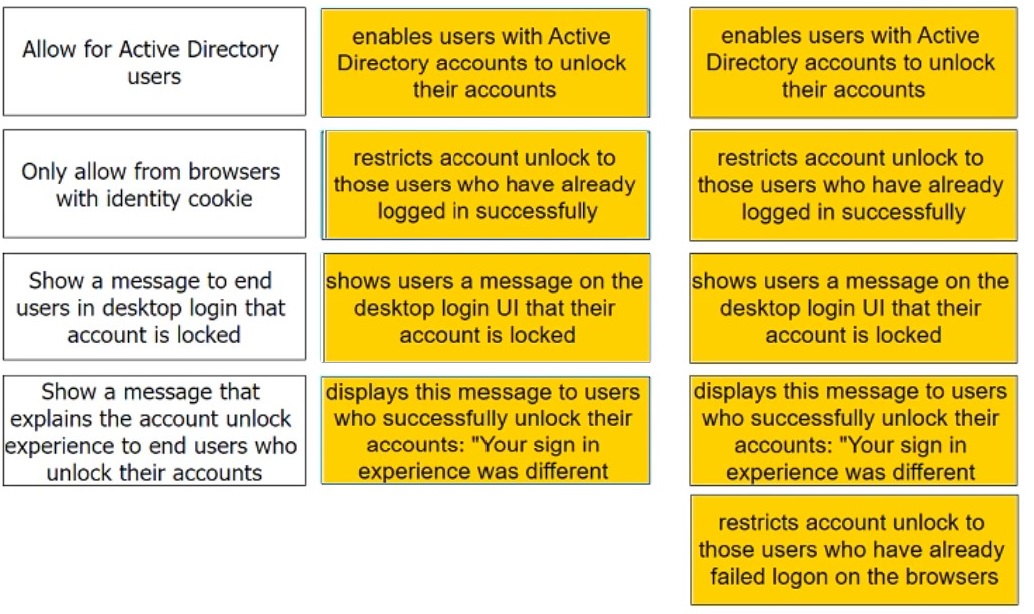
Admins can enable self-service for users to unlock their accounts. There are four options under the Admin Portal Core Services > Policies > User Security Policies > Self Service > Account Unlock options.
Match each option to the correct description.
You are tasked to enforce certificate based authentication onto all the domain-joined Windows machines within your organization. Based on the inventory record, there are 1000 Windows machines, which include 150 standalone Windows machines. The enrollment will be conducted from either the office network or through the Virtual Private Network (VPN).
Which parameter(s) should you define within the enrollment code to ensure the security of the code and that only the authorized endpoints get registered?
Which HR system supports synchronization to both Active Directory and CyberArk Identity Cloud Directory?
You get the following error: "Not Authorized. You do not have permission to access this feature".
What is most likely the cause of the error?
As part of an ongoing incident investigation, you want to examine all data/events that are relevant to updating user profiles.
Which dataset from the UBA portal should you use?
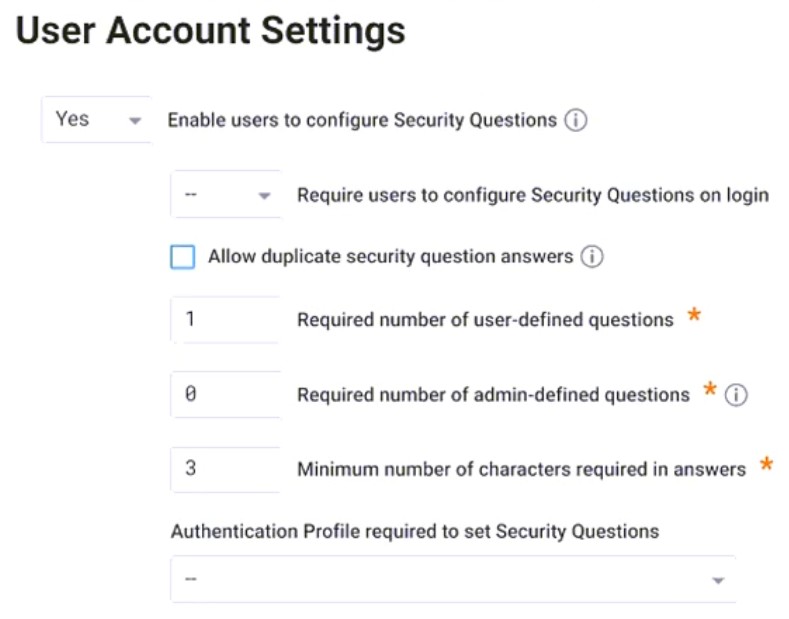
Refer to the exhibit.
Which statement is correct about this configuration shown?



 C:\Users\Waqas Shahid\Desktop\Mudassir\Untitled.jpg
C:\Users\Waqas Shahid\Desktop\Mudassir\Untitled.jpg