Logical Operations CFR-210 - Logical Operations CyberSec First Responder
During a malware outbreak, a security analyst has been asked to capture network traffic in hourly increments for analysis by the incident response team. Which of the following tcpdump commands would generate hourly pcap files?
Which of the following tools can be used to identify open ports and services?
During an investigation on Windows 10 system, a system administrator needs to analyze Windows event logs related to CD/DVD-burning activities. In which of the following paths will the system administrator find these logs?
Which of the following types of logs is shown below, and what can be discerned from its contents?
2015-07-19 12:33:31 reject UDP 146.64.21.212 192.141.173.72 1234 80
2015-07-19 12:33:31 reject UDP 166.32.22.12 192.141.173.72 1234 80
2015-07-19 12:33:31 reject UDP 123.56.71.145 192.141.173.72 1234 80
2015-07-19 12:33:31 reject UDP 146.64.21.212 192.141.173.72 1234 80
2015-07-19 12:33:32 reject UDP 166.32.22.12 192.141.173.72 1234 80
2015-07-19 12:33:32 reject UDP 123.56.71.145 192.141.173.72 1234 80
2015-07-19 12:33:32 reject UDP 146.64.21.212 192.141.173.72 1234 80
2015-07-19 12:33:33 reject UDP 166.32.22.12 192.141.173.72 1234 80
2015-07-19 12:33:33 reject UDP 123.56.71.145 192.141.173.72 1234 80
2015-07-19 12:33:33 reject UDP 146.64.21.212 192.141.173.72 1234 80
2015-07-19 12:33:34 reject UDP 166.32.22.12 192.141.173.72 1234 80
2015-07-19 12:33:34 reject UDP 123.56.71.145 192.141.173.72 1234 80
2015-07-19 12:33:34 reject UDP 146.64.21.212 192.141.173.72 1234 80
2015-07-19 12:33:35 reject UDP 166.32.22.12 192.141.173.72 1234 80
2015-07-19 12:33:35 reject UDP 123.56.71.145 192.141.173.72 1234 80
Which of the following are legally compliant forensics applications that will detect ADS or a file with an incorrect file extension? (Choose two.)
A security professional has been tasked with the protection of a specific set of information essential to a corporation’s livelihood, the exposure of which could cost the company billions of dollars in long-term revenue. The professional is interested in obtaining advice for preventing the theft of this type of information. Which of the following is the BEST resource for finding this material?
During an annual penetration test, several rootkit-enabled systems are found to be exfiltrating data. The penetration test team and the internal incident response team work to begin cleanup. The company’s operations team offers a new emails server to use for communications during the incident. As cleanup continues, the attackers seem to know exactly what the incident response plan is. Which of the following will prevent the attackers from compromising cleanup activities?
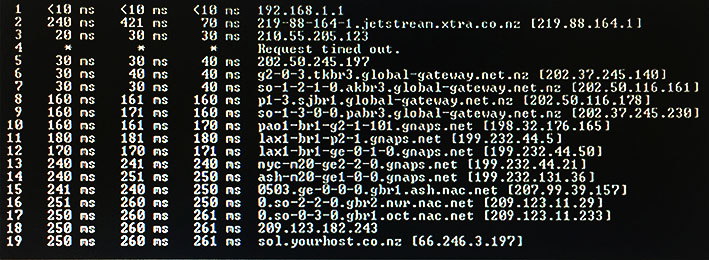
Click the exhibit button. Which of the following Windows tools is executed?
An organization’s public information website has been defaced. The incident response team is actively engaged in the following actions:
- Installing patches on the web server
- Turning off unnecessary services on web server
- Adding new ACL rules to the WAF
- Changing all passwords on web server accounts
Which of the following incident response phases is the team MOST likely conducting?
An incident responder is asked to create a disk image of a compromised Linux server. Which of the following commands should be used to do this?



