Logical Operations CFR-210 - Logical Operations CyberSec First Responder
While a network administrator is monitoring the company network, an unknown local IP address is starting to release high volumes of anonymous traffic to an unknown external IP address. Which of the following would indicate to the network administrator potential compromise?
When performing an investigation, a security analyst needs to extract information from text files in a Windows operating system. Which of the following commands should the security analyst use?
A malicious attacker has compromised a database by implementing a Python-based script that will automatically establish an SSH connection daily between the hours of 2:00 am and 5:00 am. Which of the following is the MOST common motive for the attack vector that was used?
A suspicious laptop is found in a datacenter. The laptop is on and processing data, although there is no application open on the screen. Which of the following BEST describes a Windows tool and technique that an investigator should use to analyze the laptop’s RAM for working applications?
An attacker has sent malicious macro-enabled Office files. Which of the following regular expressions will return a list of macro-enabled files?
Click the exhibit button. After reviewing captured network traffic logs, a security auditor suspects a violation of the organization’s computer use policy. Which of the following is the likely indicator of the violation?
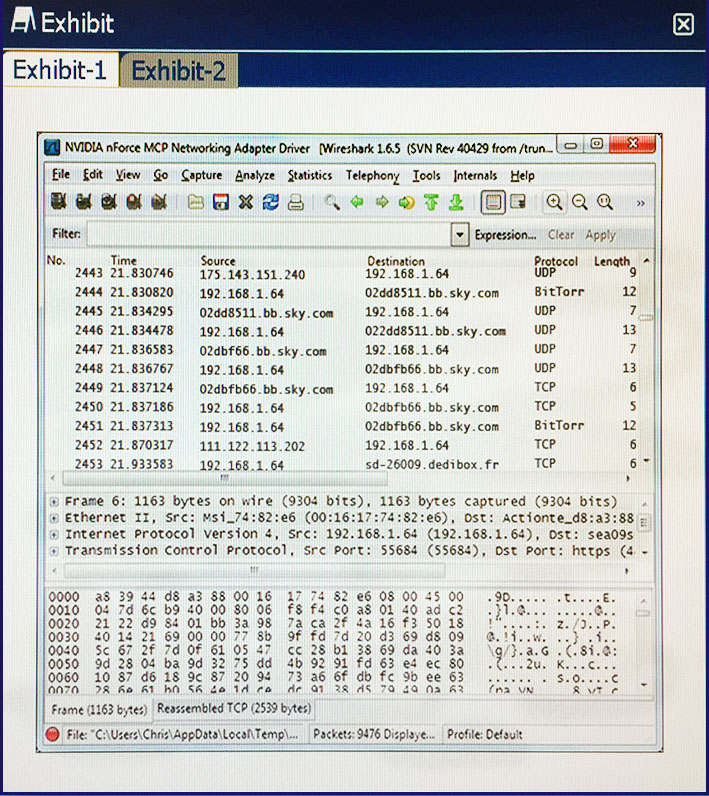
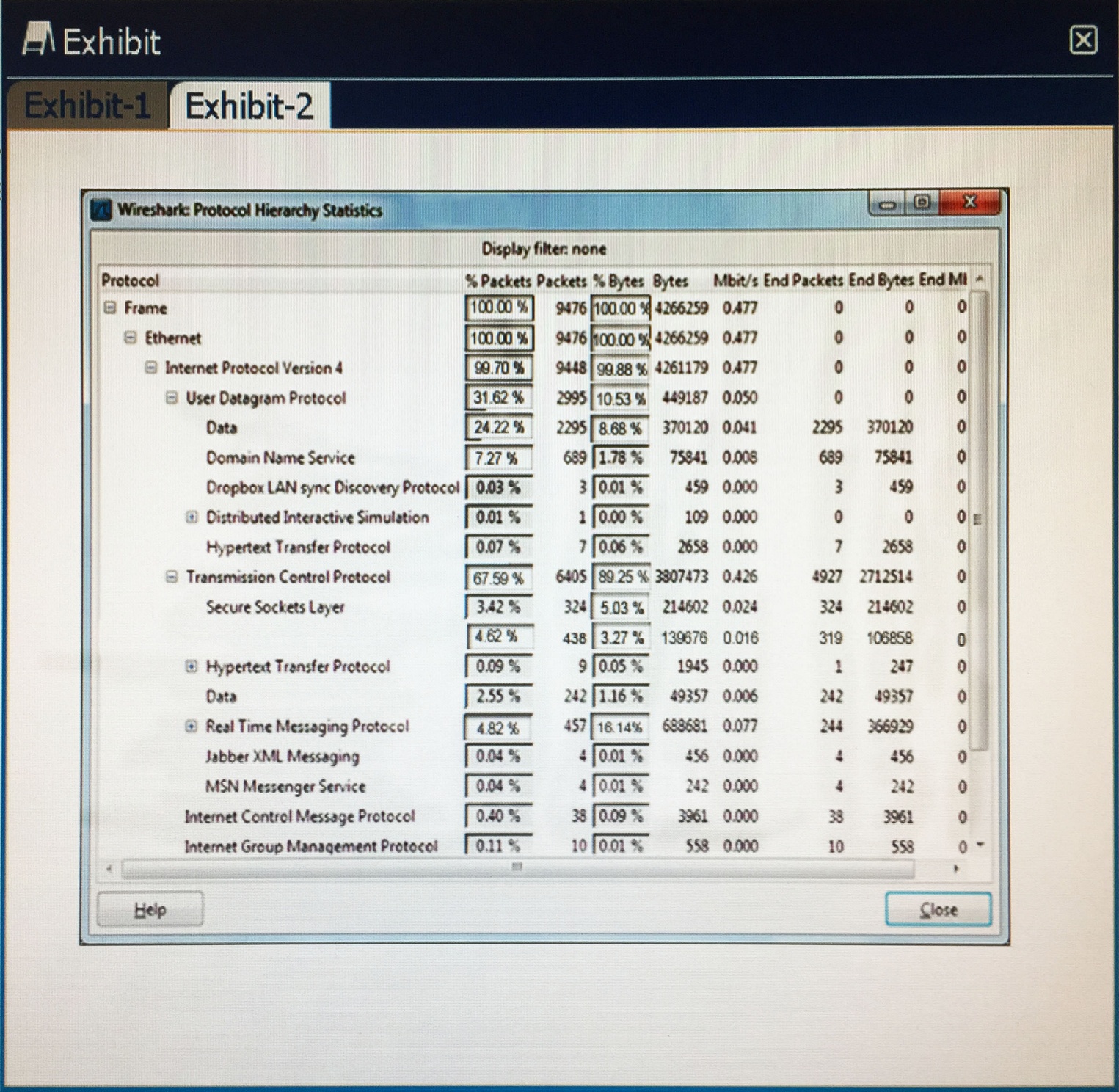
An attacker performs reconnaissance on a Chief Executive Officer (CEO) using publicity available resources to gain access to the CEO’s office. The attacker was in the CEO’s office for less than five minutes, and the attack left no traces in any logs, nor was there any readily identifiable cause for the exploit. The attacker in then able to use numerous credentials belonging to the CEO to conduct a variety of further attacks. Which of the following types of exploit is described?
Which of the following is the reason that out-of-band communication is used during a security incident?
A hacker’s end goal is to target the Chief Financial Officer (CFO) of a bank. Which of the following describes this social engineering tactic?
An outside organization has reported to the Chief Information Officer (CIO) of a company that it has received attack from a Linux system in the company’s DMZ. Which of the following commands should an incident responder use to review a list of currently running programs on the potentially compromised system?



