Logical Operations CFR-210 - Logical Operations CyberSec First Responder
An organization’s firewall has recently been bombarded with an excessive amount of failed requests. A security analyst has been tasked with providing metrics on any failed attempts to ports above 1000. Which of the following regular expressions will work BEST to identify an IP address with the desired port range?
A security analyst for a financial services firm is monitoring blogs and reads about a zero-day vulnerability being exploited by a little-known group of hackers. The analyst wishes to independently validate and corroborate the blog’s posting. Whichof the following sources of information will provide the MOST credible supporting threat intelligence in this situation?
A network administrator has been asked to configure a new network. It is the company’s policy to segregate network functions using different Virtual LANs (VLANs). On which of the following is this configuration MOST likely to occur?
An attacker has exfiltrated the SAM file from a Windows workstation. Which of the following attacks is MOST likely being perpetrated?
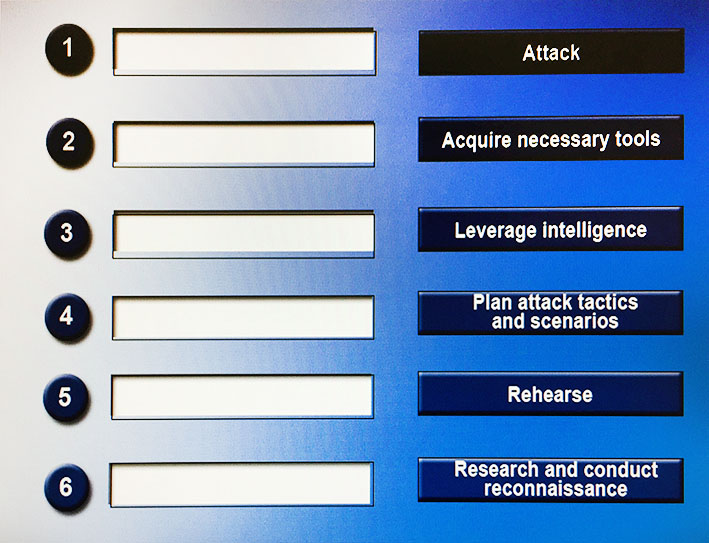
Drag and drop the following steps to perform a successful social engineering attack in the correct order, from first (1) to last (6).
To redact or obfuscate sensitive data, a company requires its name be changed throughout a port-incident report. Using a Linux sed command, which of the following will replace the company’s name with “Acme�
Which of the following could an attacker use to perpetrate a social engineering attack? (Choose two.)
Which of the following is an automated password cracking technique that uses a combination of upper and lower case letters, 0-9 numbers, and special characters?
Which of the following describes pivoting?
Which of the following can hackers use to gain access to a system over the network without knowing the actual password?




