CompTIA CS0-003 - CompTIA CyberSecurity Analyst CySA+ Certification Exam
A security analyst needs to identify a computer based on the following requirements to be mitigated:
The attack method is network-based with low complexity.
No privileges or user action is needed.
The confidentiality and availability level is high, with a low integrity level.
Given the following CVSS 3.1 output:
Computer1: CVSS3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:L/A:H
Computer2: CVSS3.1/AV:L/AC:L/PR:N/UI:N/S:U/C:H/I:L/A:H
Computer3: CVSS3.1/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:L/A:H
Computer4: CVSS3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:L/A:H
Which of the following machines should the analyst mitigate?
While configuring a SIEM for an organization, a security analyst is having difficulty correlating incidents across different systems. Which of the following should be checked first?
While reviewing the web server logs, a security analyst notices the following snippet:
.. \ .. / .. \ .. /boot.ini
Which of the following Is belng attempted?
A user is flagged for consistently consuming a high volume of network bandwidth over the past week. During the investigation, the security analyst finds traffic to the following websites:
Date/Time
URL
Destination Port
Bytes In
Bytes Out
12/24/2023 14:00:25
youtube.com
80
450000
4587
12/25/2023 14:09:30
translate.google.com
80
2985
3104
12/25/2023 14:10:00
tiktok.com
443
675000
105
12/25/2023 16:00:45
netflix.com
443
525900
295
12/26/2023 16:30:45
grnail.com
443
1250
525984
12/31/2023 17:30:25
office.com
443
350000
450
12/31/2023 17:35:00
youtube.com
443
300
350000
Which of the following data flows should the analyst investigate first?
Which of the following security operations tasks are ideal for automation?
An analyst is evaluating the following vulnerability report:
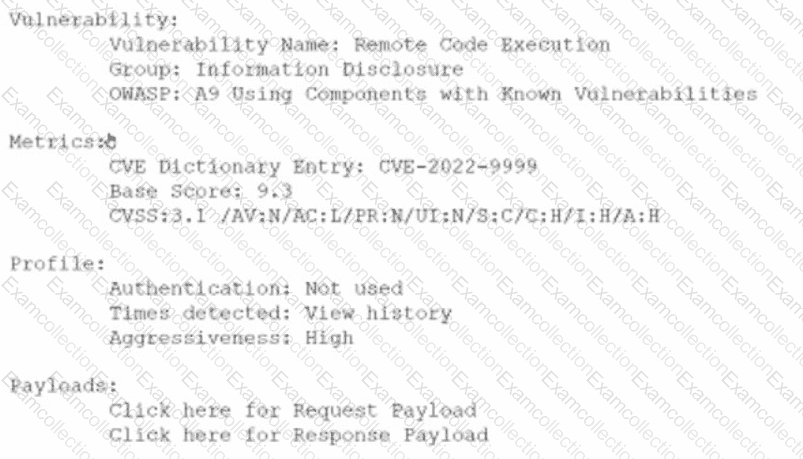
Which of the following vulnerability report sections provides information about the level of impact on data confidentiality if a successful exploitation occurs?
A security analyst reviews a SIEM alert related to a suspicious email and wants to verify the authenticity of the message:
SPF = PASS
DKIM = FAIL
DMARC = FAIL
Which of the following did the analyst most likely discover?
After completing a review of network activity. the threat hunting team discovers a device on the network that sends an outbound email via a mail client to a non-company email address daily
at 10:00 p.m. Which of the following is potentially occurring?
Which of the following explains the importance of a timeline when providing an incident response report?
A technician identifies a vulnerability on a server and applies a software patch. Which of the following should be the next step in the remediation process?



