CompTIA CS0-003 - CompTIA CyberSecurity Analyst CySA+ Certification Exam
Which of the following is a KPI that is used to monitor or report on the effectiveness of an incident response reporting and communication program?
Which of the following best describes the importance of implementing TAXII as part of a threat intelligence program?
When undertaking a cloud migration of multiple SaaS application, an organizations system administrator struggled … identity and access management to cloud-based assets. Which of the following service models would have reduced the complexity of this project?
Which of the following documents sets requirements and metrics for a third-party response during an event?
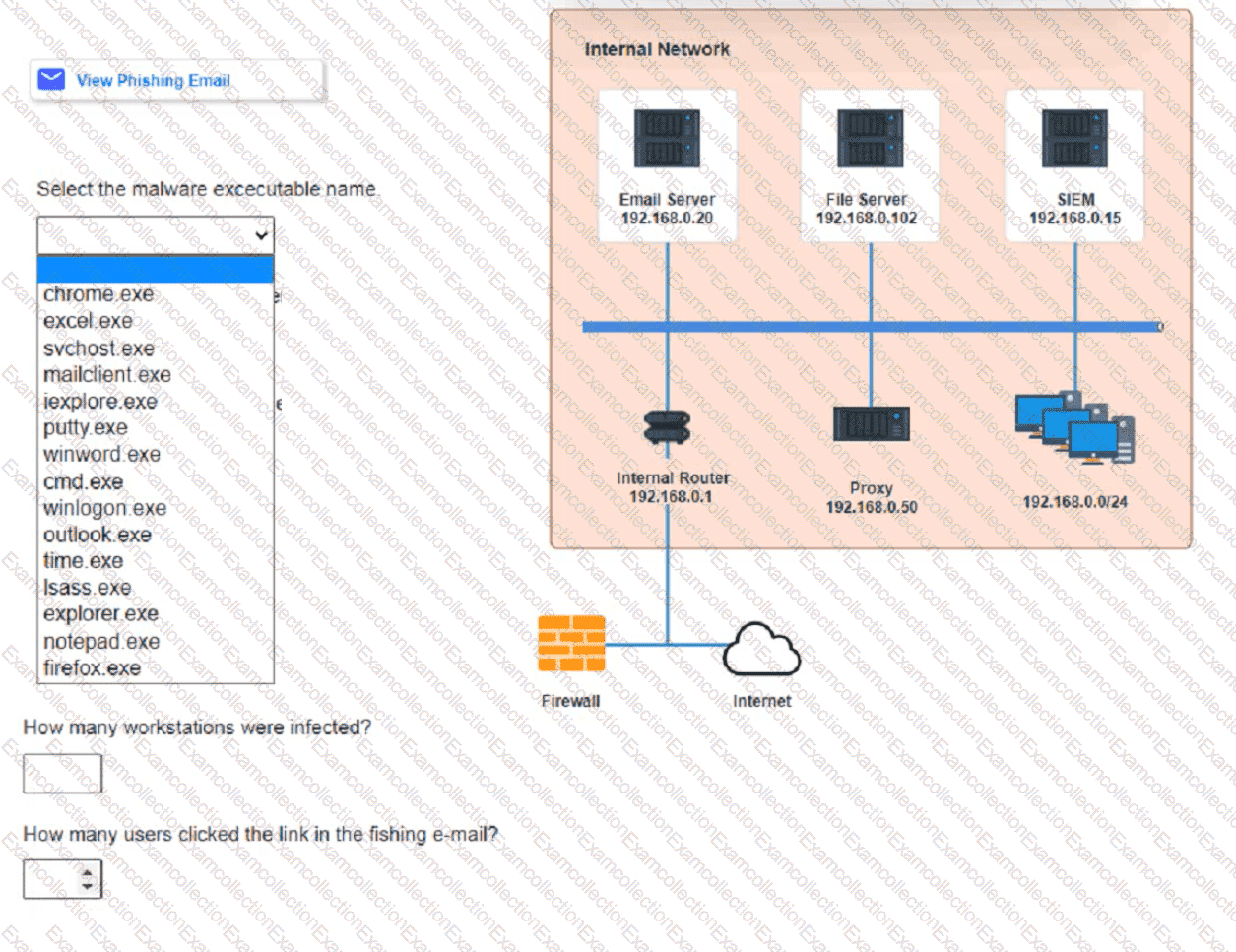
Approximately 100 employees at your company have received a Phishing email. AS a security analyst. you have been tasked with handling this Situation.
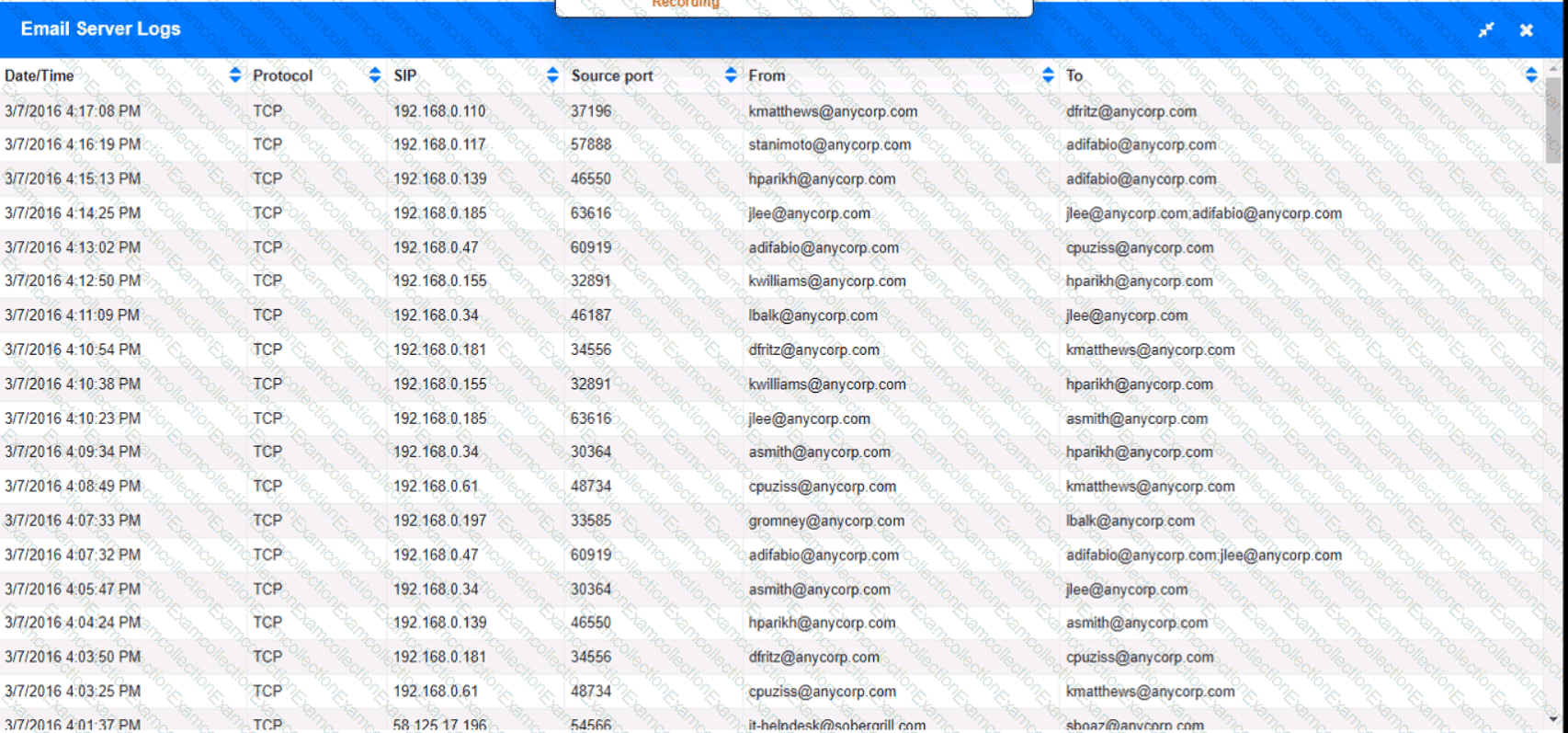
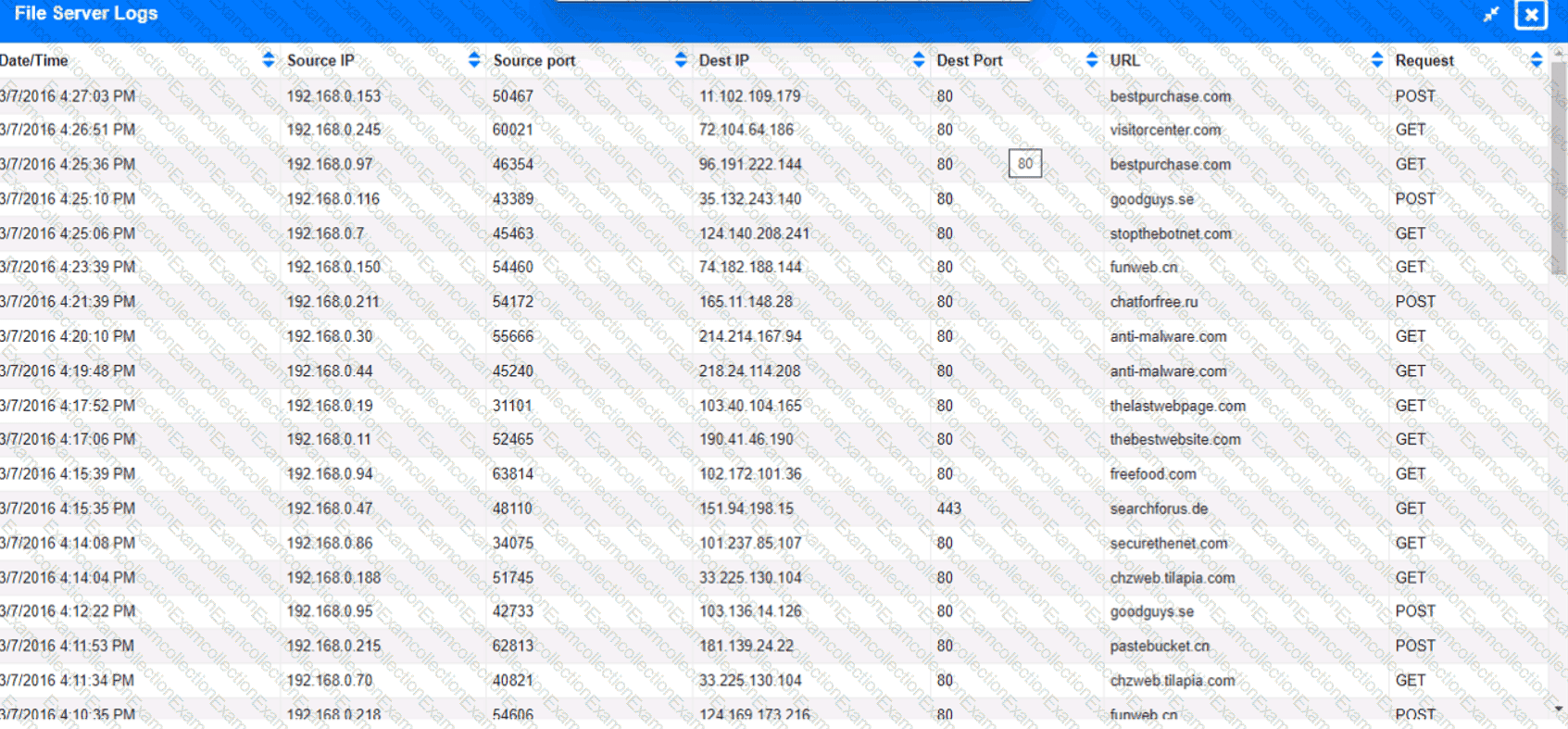
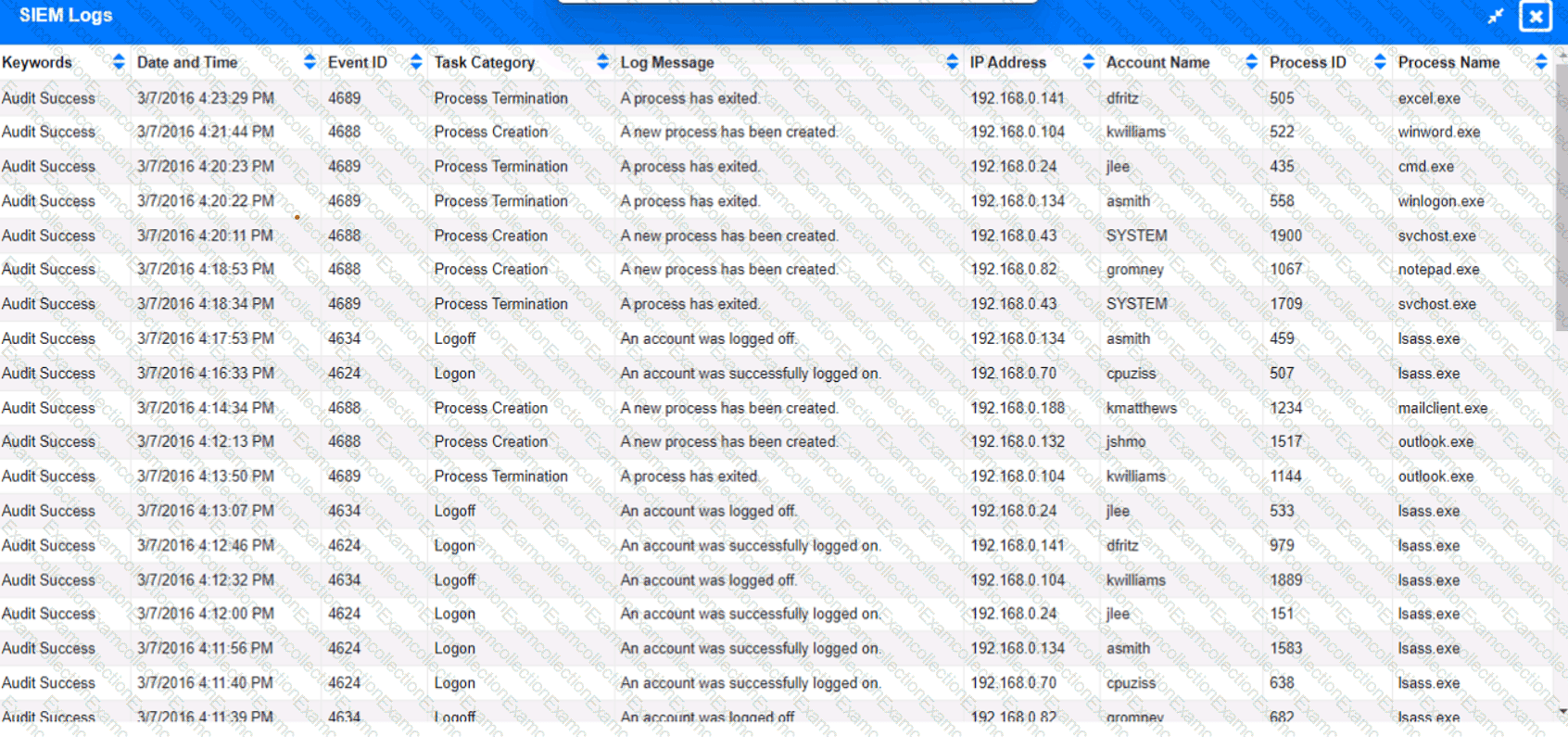
Review the information provided and determine the following:
1. HOW many employees Clicked on the link in the Phishing email?
2. on how many workstations was the malware installed?
3. what is the executable file name of the malware?
During an internal code review, software called "ACE" was discovered to have a vulnerability that allows the execution of arbitrary code. The vulnerability is in a legacy, third-party vendor resource that is used by the ACE software. ACE is used worldwide and is essential for many businesses in this industry. Developers informed the Chief Information Security Officer that removal of the vulnerability will take time. Which of the following is the first action to take?
During a recent site survey. an analyst discovered a rogue wireless access point on the network. Which of the following actions should be taken first to protect the network while preserving evidence?
An organization has tracked several incidents that are listed in the following table:
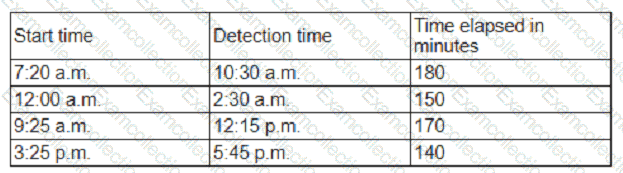 Which of the following is the organization's MTTD?
Which of the following is the organization's MTTD?
When investigating a potentially compromised host, an analyst observes that the process BGInfo.exe (PID 1024), a Sysinternals tool used to create desktop backgrounds containing host details, has bee running for over two days. Which of the following activities will provide the best insight into this potentially malicious process, based on the anomalous behavior?
An organization receives a legal hold request from an attorney. The request pertains to emails related to a disputed vendor contract. Which of the following is the first step for the security team to take to ensure compliance with the request?



