EMC DEA-3TT2 - Associate - Data Protection and Management Version 2 Exam
What is a healthcare use case for Big Data Analytics?
The operating time of a system is 24 hours per day, Monday through Saturday. Failure of the system occurs as follows.
Monday: No failure
Tuesday: 5 A. M. to 7 A. M.
Wednesday: No failure
Thursday: 4 P.M. to 8 P.M.
Friday: 8 A. M. to 11 A. M.
Saturday: No failure
What is the MTBF of the system?
A backup of 20 GB of data is reduced by a deduplication algorithm to 4 GB of data. What is the deduplication ratio?
Which product allows data owners to back up and restore using native applications?
A consumer performs backup at its on-premise data center for operational recovery. The consumer wants disaster recovery (DR) protection for their data, but they do not want to own and manage a remote site for DR. Which paid backup service is most appropriate for this consumer?
A full backup of a production volume is created on Sunday, and incremental backups are created for the rest of the week. What are the contents of the backup on Thursday?
What makes services visible and accessible to the users?
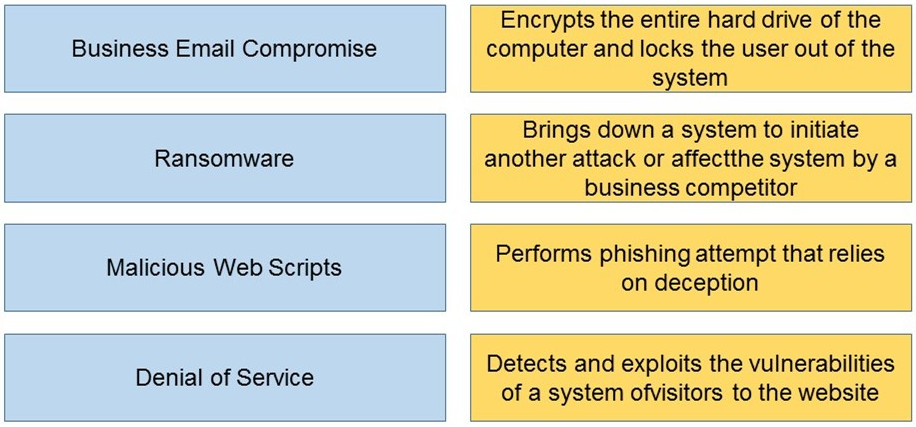
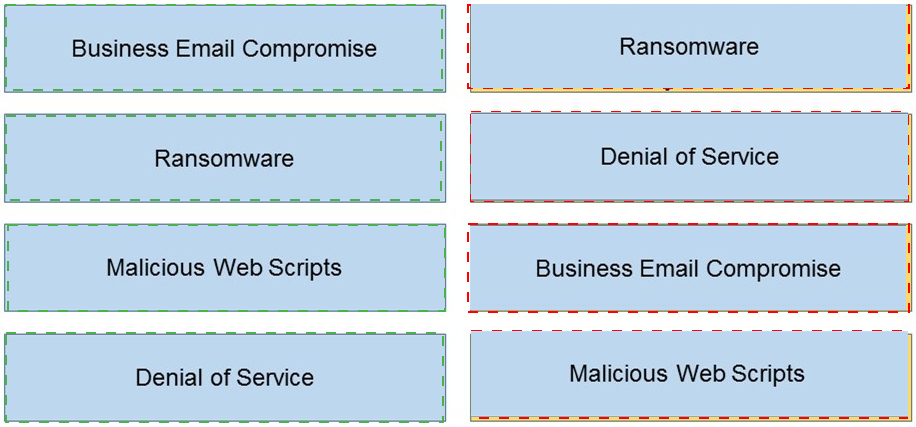
Match the types of cyber-attack with their respective description.