EMC DEA-3TT2 - Associate - Data Protection and Management Version 2 Exam
What is the process of identifying and moving inactive data from primary storage systems to lower-cost storage systems for long-term retention?
Where is the index stored after an archiving operation?
Which security control detects and blocks unusual network behavior?
Which key metric should be used when updating the corporate disaster recovery plan to minimize data loss?
Which describes graceful degradation?
What is true of hot-swappable hardware?
Which cloud service model allows the deployment of consumer-created applications on the provider's infrastructure?
What are the key functions of data management?
What is a characteristic of data archiving?
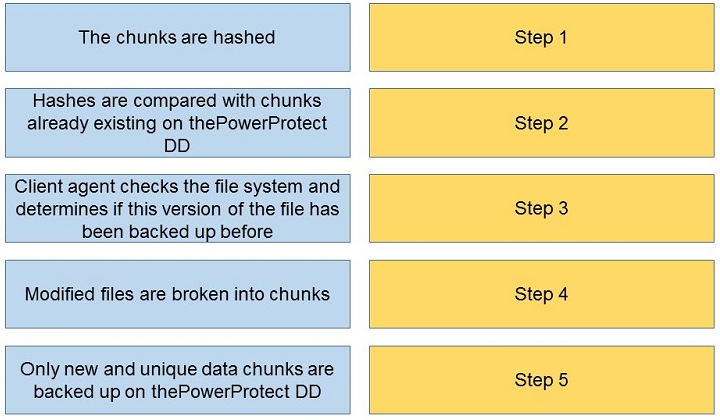
What is the correct sequence of actions during a DDBoost backup?