Fortinet FCP_FMG_AD-7.4 - FCP - FortiManager 7.4 Administrator
What must you consider before deciding to use FortiManager to manage a FortiAnalyzer device?
Which configuration setting for FortiGate is part o an ADOM-level database on FortiManager?
What happens if you create an ADOM with version 7.2, add FortiGate devices running FortiOS 7.2, and then upgrade the FortiGate devices to FortiOS 7.4?
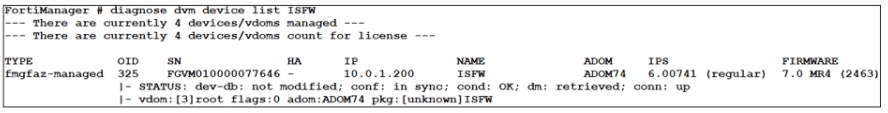
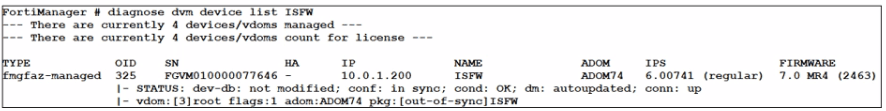
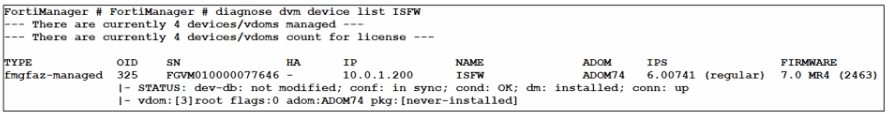
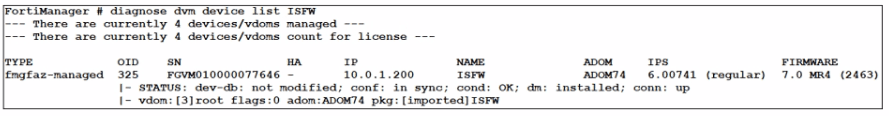
Which output is displayed right after moving the ISFW device from one ADOM to another?
A)
B)
C)
D)
An administrator configures a new OSPF area on FortiManager and has not yet pushed the changes to the managed FortiGate device. In which database will the configuration be saved?
Refer to the exhibit.
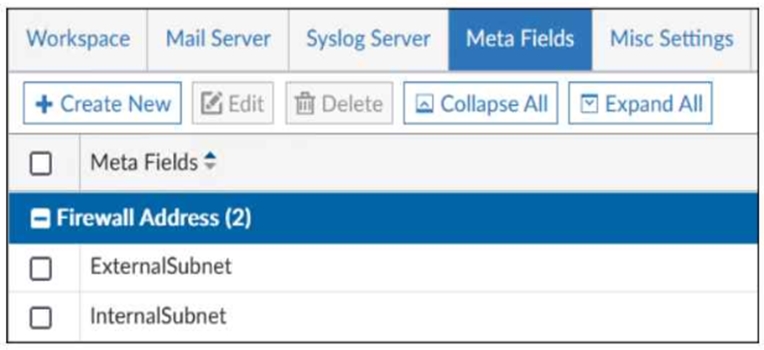
An administrator created two new meta fields in FortiManager.
Which operation can be performed with these parameters?
An administrator created a new ADOM named Training for FortiGate devices only, and added the root FortiGate device of a Security Fabric group to the Training ADOM.
Given the administrator's actions, which statement correctly describes the expected result for the downstream devices in the Security Fabric?
Refer to the exhibit.

Given the configuration shown in the exhibit, what are two results from this configuration? (Choose two.)



