Fortinet FCSS_SDW_AR-7.4 - FCSS - SD-WAN 7.4 Architect
An administrator is configuring SD-WAN to load balance their network traffic. Which two things should they consider when setting up SD-WAN? (Choose two.)
Refer to the exhibits.
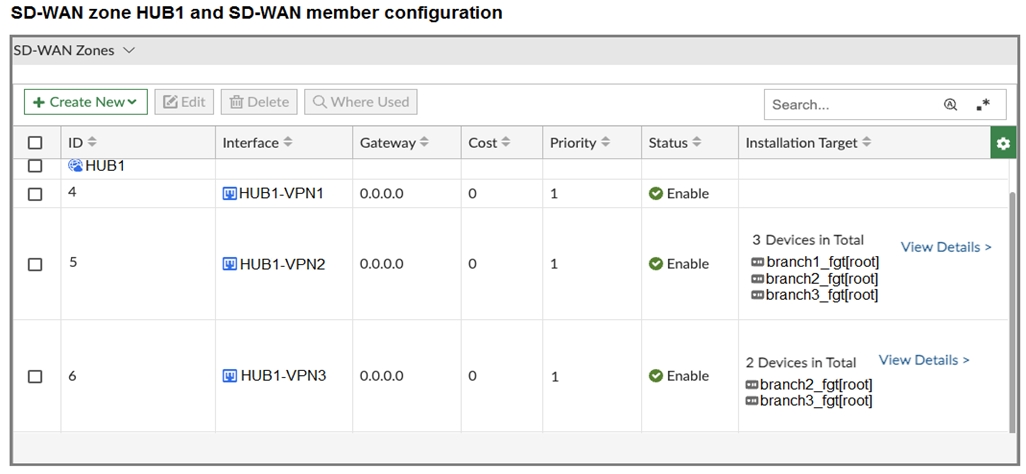
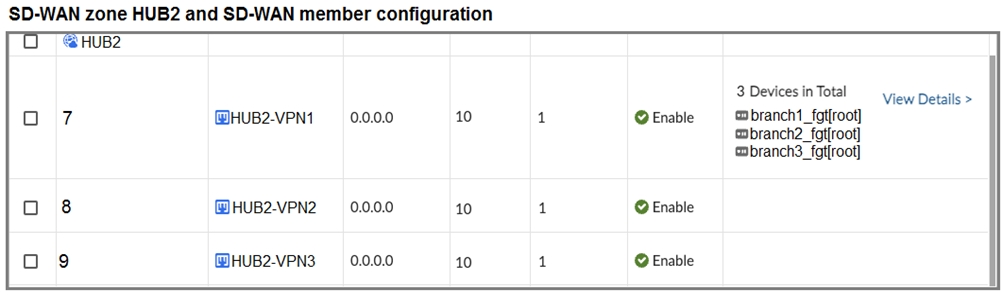
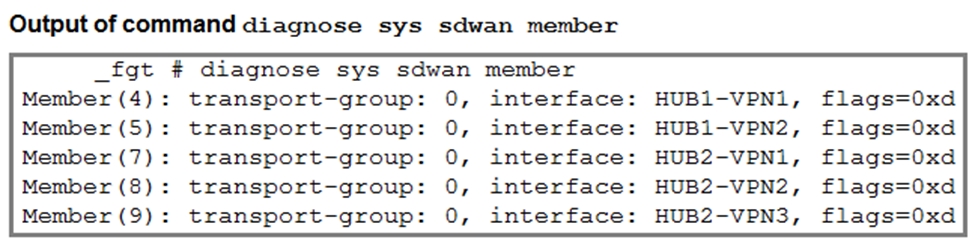
The first exhibit shows the SD-WAN zone HUB1 and SD-WAN member configuration from an SD-WAN template, and the second exhibit shows the output of command diagnose sys sdwan member collected on a FortiGate device.
Which statement best describes what the diagnose output shows?
Exhibit.
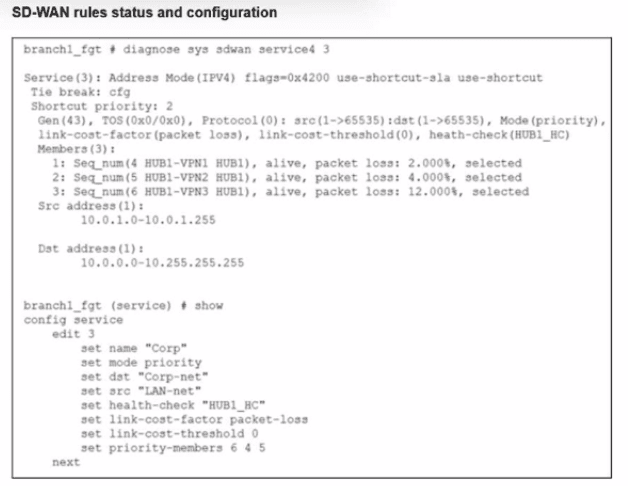
Refer to the exhibit, which shows the SD-WAN rule status and configuration.
Based on the exhibit, which change in the measured packet loss will make HUB1-VPN3 the new preferred member?
Refer to the exhibit.
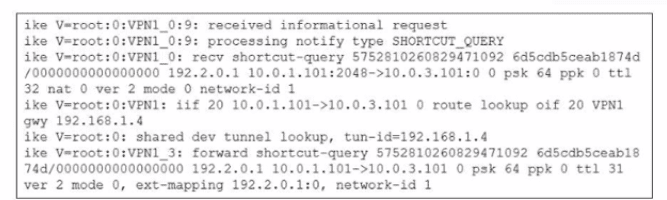
Which statement best describe the role of the ADVPN device in handling traffic?
Refer to the exhibit.
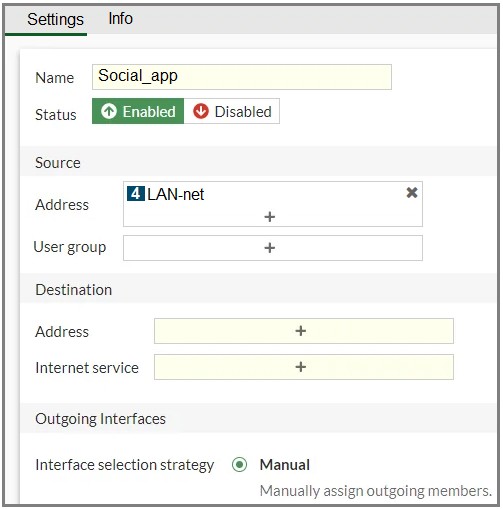
You configure SD-WAN on a standalone FortiGate device. You want to create an SD-WAN rule that steers Facebook and Linkedin traffic through the less costly internet link. The FortiGate GUI page appears as shown in the exhibit.
What should you do to set Facebook and LinkedIn as destinations?
Refer to the exhibits.
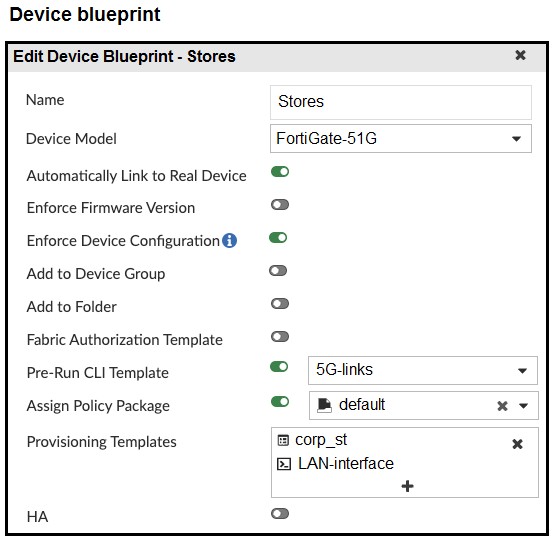
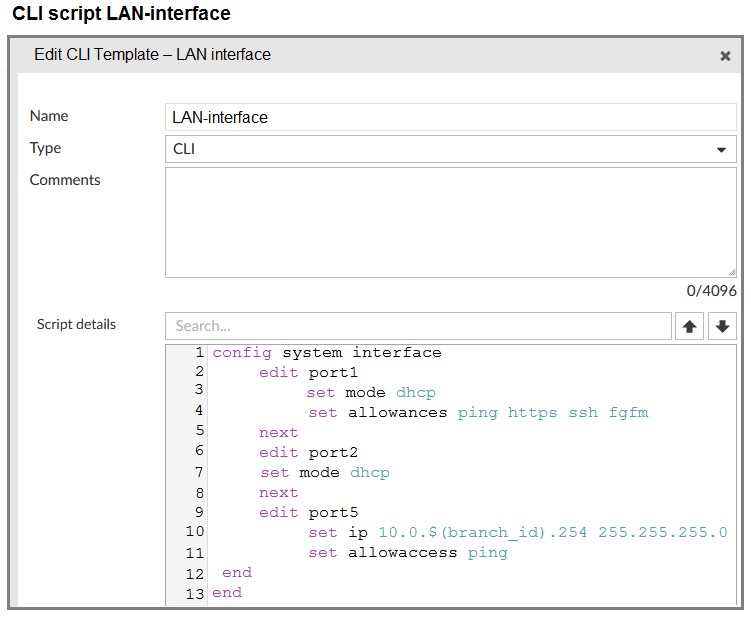
The administrator configured a device blueprint and CLI scripts as shown in the exhibits, to prepare for onboarding FortiGate devices in the company’s stores. Later, a technician prepares a FortiGate 51G with a basic configuration and connects it to the network. The basic configuration contains the port1 configuration and the minimal configuration required to allow the device to connect to FortiManager.
After the device first connects to FortiManager, FortiManager updates the device configuration.
Based on the exhibits, which actions does FortiManager perform?
An SD-WAN member is no longer used to steer SD-WAN traffic. The administrator updated the SD-WAN configuration and deleted the unused member. After the configuration update, users report that some destinations are unreachable. You confirm that the affected flow does not match an SD-WAN rule.
What could be a possible cause of the traffic interruption?
You want FortiGate to use SD-WAN rules to steer local-out traffic.
Which two constraints should you consider? (Choose two.)
When you use the command diagnose sys session list, how do you identify the sessions that correspond to traffic steered according to SD-WAN rules?
Which statement describes FortiGate behavior when you reference a zone in a static route?



