GIAC GCCC - GIAC Critical Controls Certification (GCCC)
Acme Corporation performed an investigation of its centralized logging capabilities. It found that the central server is missing several types of logs from three servers in Acme's inventory. Given these findings, what is the most appropriate next step?
Which of the following is a benefit of stress-testing a network?
Which of the following best describes the CIS Controls?
An organization is implementing an application software security control their custom-written code that provides web—based database access to sales partners. Which action will help mitigate the risk of the application being compromised?
After installing a software package on several workstations, an administrator discovered the software opened network port TCP 23456 on each workstation. The port is part of a software management function that is not needed on corporate workstations. Which actions would best protect the computers with the software package installed?
How does an organization's hardware inventory support the control for secure configurations?
Based on the data shown below.
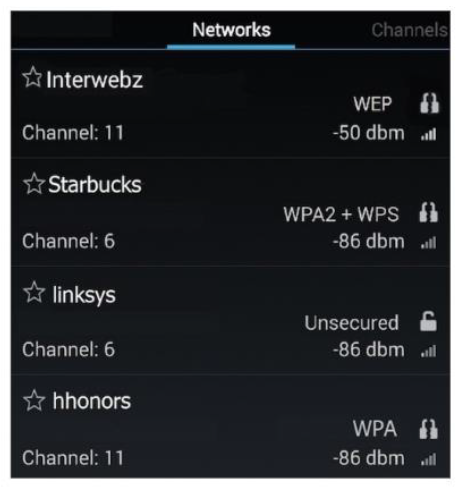
Which wireless access point has the manufacturer default settings still in place?
Executive management approved the storage of sensitive data on smartphones and tablets as long as they were encrypted. Later a vulnerability was announced at an information security conference that allowed attackers to bypass the device’s authentication process, making the data accessible. The smartphone manufacturer said it would take six months for the vulnerability to be fixed and distributed through the cellular carriers. Four months after the vulnerability was announced, an employee lost his tablet and the sensitive information became public.
What was the failure that led to the information being lost?
An auditor is validating the policies and procedures for an organization with respect to a control for Data Recovery. The organization’s control states they will completely back up critical servers weekly, with incremental backups every four hours. Which action will best verify success of the policy?
As part of a scheduled network discovery scan, what function should the automated scanning tool perform?



