GIAC GCCC - GIAC Critical Controls Certification (GCCC)
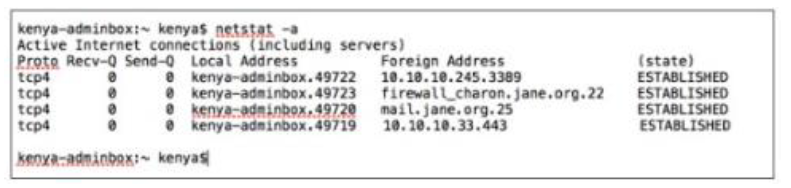
Kenya is a system administrator for SANS. Per the recommendations of the CIS Controls she has a dedicated host (kenya- adminbox / 10.10.10.10) for any administrative tasks. She logs into the dedicated host with her domain admin credentials. Which of the following connections should not exist from kenya-adminbox?
Which of the following will decrease the likelihood of eavesdropping on a wireless network?
Which of the following is necessary to automate a control for Inventory and Control of Hardware Assets?
What is the list displaying?
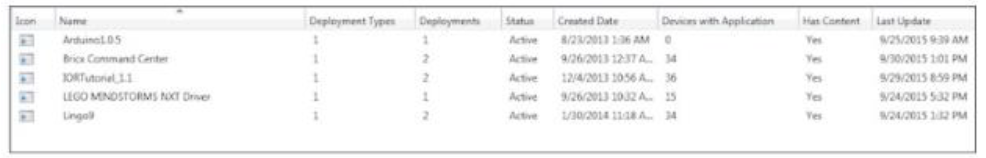
An auditor is focusing on potential vulnerabilities. Which of the following should cause an alert?
Which of the following should be measured and analyzed regularly when implementing the Secure Configuration for Hardware and Software on Mobile Devices, Laptops, Workstations, and Servers CIS Control?
What is the first step suggested before implementing any single CIS Control?



