GIAC GCCC - GIAC Critical Controls Certification (GCCC)
An analyst investigated unused organizational accounts. The investigation found that:
-10% of accounts still have their initial login password, indicating they were never used
-10% of accounts have not been used in over six months
Which change in policy would mitigate the security risk associated with both findings?
Acme Corporation is doing a core evaluation of its centralized logging capabilities. Which of the following scenarios indicates a failure in more than one CIS Control?
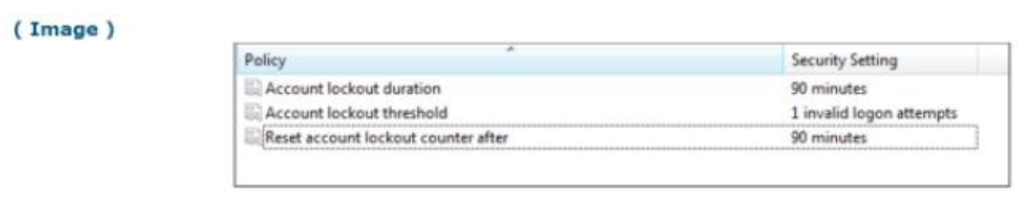
An organization is implementing a control for the Account Monitoring and Control CIS Control, and have set the Account Lockout Policy as shown below. What is the risk presented by these settings?
What could a security team use the command line tool Nmap for when implementing the Inventory and Control of Hardware Assets Control?
Which of the following is necessary for implementing and automating the Continuous Vulnerability Assessment and Remediation CIS Control?
Below is a screenshot from a deployed next-generation firewall. These configuration settings would be a defensive measure for which CIS Control?
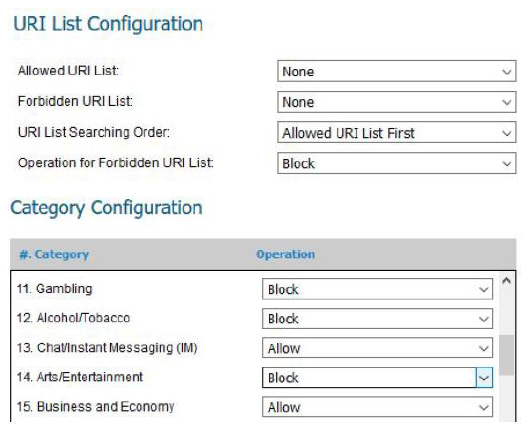
As part of an effort to implement a control on E-mail and Web Protections, an organization is monitoring their webserver traffic. Which event should they receive an alert on?
Which projects enumerates or maps security issues to CVE?
An organization has implemented a control for Controlled Use of Administrative Privileges. They are collecting audit data for each login, logout, and location for the root account of their MySQL server, but they are unable to attribute each of these logins to a specific user. What action can they take to rectify this?
Which of the following can be enabled on a Linux based system in order to make it more difficult for an attacker to execute malicious code after launching a buffer overflow attack?



