GIAC GCED - GIAC Certified Enterprise Defender
What is the most common read-only SNMP community string usually called?
Which control would BEST help detect a potential insider threat?
Which statement below is the MOST accurate about insider threat controls?
What would be the output of the following Google search?
filetype:doc inurl:ws_ftp
How would an attacker use the following configuration settings?
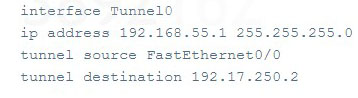
What would the output of the following command help an incident handler determine?
cscript manage-bde . wsf –status
Following a Digital Forensics investigation, which of the following should be included in the final forensics report?
What should happen before acquiring a bit-for-bit copy of suspect media during incident response?
What is needed to be able to use taskkill to end a process on remote system?
An outside vulnerability assessment reveals that users have been routinely accessing Gmail from work for over a year, a clear violation of this organization’s security policy. The users report “it just started working one dayâ€. Later, a network administrator admits he meant to unblock Gmail for just his own IP address, but he made a mistake in the firewall rule.
Which security control failed?



