GIAC GCED - GIAC Certified Enterprise Defender
Which of the following attacks would use “..†notation as part of a web request to access restricted files and directories, and possibly execute code on the web server?
A security device processes the first packet from 10.62.34.12 destined to 10.23.10.7 and recognizes a malicious anomaly. The first packet makes it to 10.23.10.7 before the security devices sends a TCP RST to 10.62.34.12. What type of security device is this?
Which tool uses a Snort rules file for input and by design triggers Snort alerts?
Which of the following would be used in order to restrict software form performing unauthorized operations, such as invalid access to memory or invalid calls to system access?
An analyst will capture traffic from an air-gapped network that does not use DNS. The analyst is looking for unencrypted Syslog data being transmitted. Which of the following is most efficient for this purpose?
What piece of information would be recorded by the first responder as part of the initial System Description?
Which of the following is an SNMPv3 security feature that was not provided by earlier versions of the protocol?
From a security perspective, how should the Root Bridge be determined in a Spanning Tree Protocol (STP) environment?
Although the packet listed below contained malware, it freely passed through a layer 3 switch. Why didn’t the switch detect the malware in this packet?
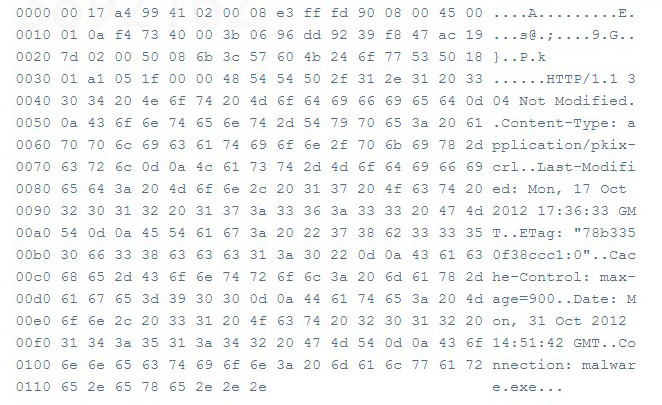
Which could be described as a Threat Vector?



